16.3 Issues for Protocol Layers in Manets
16.3 Issues for Protocol Layers in Manets
In this section, we look at the various issues for the OSI reference model layers for MANETs and briefly describe the functionality of the layers as they apply to MANETs (see Figure 16.3 for an overview). We pay special attention to the application, transport, network, data link, and physical layers. The OSI reference model contains presentation and session layers, which are not described in great detail in this chapter for the sake of simplicity. A more detailed explanation of the OSI reference model and its layers can be found in Tanenbaum [11] and Martin. [12]
16.3.1 Application Layer
The application layer provides network access to applications and protocols commonly used by end users. These applications and protocols include multimedia (audio/video, file system, and print services), file transfer protocol (FTP), electronic mail (SMTP), telnet, domain name service (DNS), and Web page retrieval (HTTP). Other higher-level issues such as security, privacy, user profiles, authentication, and data encryption also are handled by the application layer. In the case of ad hoc networks, the application layer also is responsible for providing location-based services. [13], [14], [15], [16] The presentation layer is responsible for data representation as it appears to the end user, including character sets (ASCII/EBCIDIC), syntax, and formatting. The protocols associated with the presentation layer include Network Virtual Terminal (NVT), AppleTalk Filing Protocol (AFP), and Server Message Block (SMB). The session layer is responsible for data exchange between application processes, including session flow control and error checking.
16.3.2 Transport Layer
The purpose of the transport layer is to support integrity of data packets from the source node to the destination node (end-to-end). Transport protocols can be either connection-oriented or connectionless. Connection-oriented transport protocols are needed for ensuring sequenced data delivery. In order to ensure reliable sequenced delivery, the transport layer performs multiplexing, segmenting, blocking, concatenating, error detection and recovery, flow control, and expedited data transfer. Connectionless protocols are used if reliability and sequenced data can be traded in exchange for fast data delivery. The transport layer assumes that the network layer is inherently unreliable, as the network layer can drop or lose packets, duplicate packets, and deliver packets out of order.
The transport layer ensures reliable delivery by the use of acknowledgments and retransmissions. The destination node, after it receives a packet, sends the acknowledgment back to the sender. The destination node sometime uses cumulative acknowledgment wherein a single acknowledgment is used to acknowledge a group of packets received. The sender, rather than sending a single segment at a time, sometimes sends a group of segments. This group size is referred to as the window size. The sender increases its window size as the acknowledgments arrive. The Transmission Control Protocol (TCP), [17], [18] which is the most commonly used reliable transport layer protocol, also takes care of congestion avoidance and control. The TCP protocol increases its throughput as acknowledgments arrive within a time period called the TCP time interval. If the acknowledgments arrive late, it assumes that the network is overloaded and reduces its throughput to avoid congesting the network. In contrast, User Datagram Protocol (UDP) [19], [20] is a connectionless transport protocol used for applications such as voice-and-video transport and DNS lookup.
In the MANET environment, the mobility of the nodes will almost certainly cause packets to be delivered out of order and a significant delay in the acknowledgments is to be expected as a result. In a static MANET environment, the packet losses are mainly due to errors in the wireless channel. Retransmissions are very expensive in terms of the power requirements and also occur more often than in wired networks for the reasons explained previously. In the design of efficient transport layer protocol for MANETs, the following issues must be taken into consideration:
-
Window size adjustments have to be made that not only take into account the channel errors and the end-to-end delays, but also should adjust based on the mobility dynamics of the network nodes. As pointed out earlier, in a stable ad hoc network packet losses are mainly due to errors in wireless channel and end-to-end delays.
-
Cumulative acknowledgments can be both good and bad. Given the packet losses expected in MANETs, the loss of a single acknowledgment packet will result in retransmission of a large number of packets. In a static MANET environment, there is a significant advantage in using cumulative acknowledgments. Mechanisms to adjust the acknowledgment schemes based on the dynamics of the network should be taken into consideration.
-
The time-out interval that dictates how long the protocol waits before beginning the retransmission should be adjusted based on the dynamics of the network. Clearly, a shorter time-out interval will increase the number of retransmissions, while longer time-out intervals decrease the throughput.
-
The original TCP congestion control is purely based on acknowledgment delays. This does not necessarily work well in the case of MANETs, where the delays are attributed to channel errors, broken links caused by mobility, and the contention at the medium access control (MAC) layer that is not only dependent on the traffic in the network, but also on the degree (number of neighbors) of nodes in the network.
Research in the area of transport protocols for MANETs has focused on the development of feedback mechanisms that enable the transport layer to recognize the dynamics of the network, adjust its retransmission timer and window size, and perform congestion control with more information on the network. For example, when a session is initiated, the transport layer assumes that the route is available for a period of time. When the route changes, the transport layer is informed; then transmission freezes until a new route is established. [21] Several research efforts have examined the impact of various routing algorithms on TCP. [22], [23], [24], [25] All of these studies have concluded that the route reestablishment time significantly and adversely impacts the throughput of the TCP.
For the robot team application, we presume that that the control packets sizes and hence the window sizes are small. The retransmission timer should be kept small and this will cause command and control packets to be sent constantly so as to ensure that the destination node receives it in the midst of constant route changes.
16.3.3 Network Layer and Routing
The routing algorithms for MANETs have received the most attention in recent years, and many techniques have been proposed to find a feasible path between source and destination node pairs. In the wired environment, the routing protocol [26] can either be based on link state or distance vector. In link-state routing, each router periodically send a broadcast packet to all the other routers in the network that contains information about the adjacent routers. Upon receiving this broadcast message, each router has complete knowledge of the topology of the network and executes the shortest path algorithm (Dijkstra's algorithm) to determine the routing table for itself. In the case of distance-vector routing, which is a modification of the Bellman-Ford algorithm, each router maintains a vector that contains distances it knows at that point in time (initially infinity for all nodes other than its neighbors) between itself and every other node in the network. Periodically, each node sends this vector to all its neighbors and the nodes that receive the vector update their vectors based on the information contained in the neighbor's vector.
In MANETs, routing algorithms based on link state and distance vector face serious issues as outlined below:
-
Executing a link-state protocol would require each node to send information about its neighborhood as it changes. The number of broadcast message sent by a node is related to the dynamics of the network. In a highly dynamic network, it is advisable that the nodes send updates based on the stability of a neighbor. It may be even useful to send information on only those neighbors that have been newly added or removed from its neighborhood since the last broadcast.
-
Distributing the distance vector information in a highly dynamic environment is very ineffective. The distances to the nodes keep changing as the nodes move in the network. Constant updates are required for up-to-date distance information.
-
Due to incorrect topological information, both algorithms produce routes containing loops.
-
Both algorithms cause severe drain on batteries due to the excessive amounts of messages needed to construct routing tables at nodes.
Routing in MANETs involves two important problems: (1) finding a route from the source node to the destination node, and (2) maintaining routes when there is at least one session using the route. MANET routing protocols described in the literature [27] can be either reactive, proactive, hybrid (combination of reactive and proactive), or location based. In a proactive protocol, the nodes in the system continuously monitor the topology changes and update the routing tables, similar to the link state and distance vector algorithms. There is a significant route management overhead in the case of proactive schemes, but a new session can begin as soon as the request arrives. A reactive protocol, on the other hand, discovers a route as a request arrives (on-demand). The route discovery process is performed either on a per-packet basis or a per-session basis. When routes are discovered on a per-packet basis, the routing algorithm has a high probability of sending the packet to the destination in the presence of high mobility. A routing algorithm that uses the route discovery process for a session must perform local maintenance of severed or broken paths. Location-based routing protocols use the location information about each node to perform intelligent routing.
Dynamic Source Routing (DSR) [28] is a reactive algorithm similar in concept to source routing in IP. Before a packet is routed to the destination, the DSR algorithm initiates a route discovery process in which a broadcast packet is sent to all the nodes in the network that are reachable. A node receiving the broadcast packet appends its address and broadcasts it to its neighbors. When the destination node receives the broadcast packet, it uses source routing to send a route request reply packet back to the source. Each intermediate node receiving the route request reply packet simply forwards it to the next node in the route to the source node address contained in the packet. Upon discovering the route, the source sends the packets using route information gathered during the route discovery process. A route cache is maintained at nodes that use information gathered during reception of broadcast packets of the discovery process. To avoid the route discovery process for every packet that needs to be routed, a route maintenance process is initiated, which keeps track of route changes and makes local changes to the route cache.
The temporally ordered routing algorithm (TORA) [29] maintains a virtual network topology that is a directed acyclic graph (DAG). The source has an in-degree (number of arcs coming into the source) of zero. The height of node in the DAG is its distance from the source in the DAG. The entire algorithm is based on the maintenance of the DAG as the node moves and its height changes. The three phases of the algorithm are route creation, route maintenance, and erasing of invalid routes. Once the DAG is known, the packets are routed along the edges of the DAG.
In a MANET, certain routes are more stable than others because links on those routes are not severed for a period of time. It is important that the routing algorithms determine these routes. To select these routes, each node can advertise its presence to its neighbors from time to time. Nodes receiving this advertisement increment a counter associated with the node that sends the advertisement. The degree of stability is proportional to the value of the counter. Nodes prefer routing through nodes associated with a higher counter value. This concept has been used in associativity-based routing (ABR). [30] A similar concept based on the relative signal strength between nodes has been suggested in signal-stability-based adaptive routing (SSA). [31]
Destination-sequenced distance vector routing (DSDV) [32] is a proactive routing algorithm that maintains consistent routing information at all nodes in the network by propagating changes in links. Proactive protocols that build routing tables that contain next-hop information for each destination should be very concerned about the possibility of forming loops in certain routes. These loops are due to mobility of nodes that exchange distance vectors. DSDV is the standard distance vector protocol adapted for the MANET environment and is especially equipped to avoid loops in routes. The basic idea to avoid loops is the same as that used for effective flooding in wired networks. In each packet, a sequence number is placed and each node receiving the packet increases the sequence number by one and forwards it to its neighbor. If a node receives a packet from the same source with a sequence number smaller than the one it has seen so far, then the packet is not forwarded. However, care should be taken to purge the sequence number information at each node from time to time. Ad hoc on-demand distance vector routing (AODV) [33], [34] is a routing algorithm that improves the performance of DSDV by minimizing the number of broadcast messages. This is done by on-demand route creation.
Proactive algorithms have been shown to perform effectively when the topology of the network is stable; reactive algorithms are highly effective in finding routes in the presence of high rates of topological changes. Reactive algorithms require a large number of broadcast packets to determine the destination. The dynamic spanning tree (DST) algorithm [35] is an efficient protocol that maintains a forest of trees containing the nodes and performs shortest path routing on the links of the trees. It has been shown that reactive routing on the forest of trees significantly reduces the number of messages required to find the path to the destinations. A novel concept called connectivity through time is introduced in the DST algorithm wherein if the path from the source node and the destination node may be absent currently but may be available in the future, then a path may be formed while the packet is in en route to the destination node. The DST algorithm also uses a concept termed holding time, where a packet is both forwarded and held for a period of time to allow the node to forward it later to new neighbors with which it may come in contact. The holding time allows the implementation of the concept of connectivity through time. The algorithm can be considered a hybrid protocol that is proactive in the sense that messages are to be exchanged to maintain the forest of trees and reactive when it comes to finding the path to the destination on the trees.
Zone Routing Protocol (ZRP) [36] is yet another hybrid protocol in which each node is associated with a zone of fixed radius r and contains all the nodes within a distance of r from it. ZRP uses proactive routing for routing within a zone and reactive routing to route between nodes belonging to two different zones. The size of the radius is adjusted according to the requirements of the application.
Change in the radius of influence (radius of the node's communication cell) directly affects the reachability of packets in MANETs. Ramanathan and Rosales-Hain [37] proposed a novel algorithm that determines the size of the radius of influence for each node to ensure connectedness, biconnectedness, and other levels of connectivity. The overall goals of the algorithm are to keep the radius of influence to a minimum because increase in the radius is directly proportional to the power expended. Power-aware routing protocols take into account available power at nodes and find paths containing nodes that have maximum power available in them.
Location-based routing algorithms use location information obtained from sources such as the Global Positioning System (GPS) to improve the efficiency of routing. Location-aided routing (LAR) [38] is an example of location-based routing. The LAR algorithm intelligently uses the location information of nodes to limit the search of routes in a MANET to a request zone. Two different methods of determining the request zone are supported in LAR.
Royer and Toh, [39] Broch et al., [40] Das et al., [41] and Racherla and Radhakrishnan [42] compare and contrast several proposed MANET routing algorithms using analytical modeling and simulation. Johnson [43] was one of the first to analyze issues involved in routing in MANETs. Obraczka and Tsudik [44] have made a similar analysis for multicast routing in MANETs. Mauve et al. [45] have surveyed several location-based routing algorithms. There have been a number of approaches proposed for the performance evaluation of ad hoc routing protocols, including simulation and analytical cost modeling. [46], [47] The network simulator (ns-2) [48] and the GloMoSim/Parsec [49] are the two most popular MANET simulation tools. Simulation studies have examined the effectiveness of ad hoc routing protocols in terms of number of messages delivered, given different traffic loads and dynamics of the network. The other parameters that were evaluated include routing overhead, sensitivity of the protocols with increased network traffic, and choice of paths taken with respect to its end-to-end delay and other optimization characteristics. A detailed discussion on MANET routing protocol performance issues, quantitative metrics for comparing routing algorithm performance, and appropriate parameters to be considered can be found in the IETF MANET Charter [50] and Perkins. [51]
16.3.4 Data Link Layer
The data link layer consists of the logical link control (LLC) and the medium access control (MAC) sublayers. The MAC sublayer is responsible for channel access, and the LLC is responsible for link maintenance, framing data unit, synchronization, error detection, and possibly recovery and flow control. The MAC sublayer tries to gain access to the shared channel so that the frames that it transmits do not collide (and hence get distorted) with frames sent by the MAC sublayers of other nodes sharing the medium. There have been many MAC sublayer protocols suggested in the literature for exclusive access to shared channels. Some of these protocols are centralized and others are distributed in nature. With the centralized protocols, there is a central controller and all other nodes request channel access from the controller. The controller then allocates time slots (or frequencies) to the requesting nodes. These are reservation-based protocols. The nonreservation-based protocols are purely based on contention and are very suitable for MANETs, where it is impossible to designate a leader that might be moving all the time. A detailed discussion on wireless MAC schemes can be found in Chandra et al. [52]
CSMA (Carrier Sense Multiple Access) is a distributed nonreservation-based MAC layer protocol that was used for packet radio networks wherein the MAC layer senses the carrier for any other traffic and sends the frame immediately if the medium is free. When the channel is busy, the MAC layer waits for a random time period (which grows exponentially) and then tries to resend the frame after sensing the medium. The CSMA scheme suffers from a few serious problems. [53] Assume that three nodes — A, B, and C — are in communication range, i.e., node A can hear node B's transmissions, B can hear A's as well as node C's transmissions, and C can hear B's transmissions. Assume that B is not transmitting any frames, while A and C have frames to be transmitted to B. A and C will find the channel free and send frames to B; this will result in a collision at B. This type of problem with CSMA is called the hidden terminal problem. Assume that there is a node D that is in communication with C. If B has frames to send to A, and C has frames to send to D, then both B and C will back off even though the frames sent by B and C can arrive at their respective destinations without distortions. This unnecessary backoff is termed the exposed terminal problem. These problems are depicted in Figure 16.4.
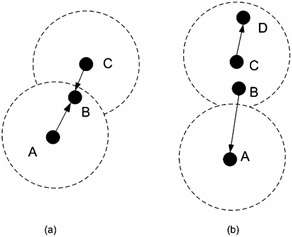
Figure 16.4: Terminal problems— (a) hidden; (b) exposed.
Multiple Access with Collision Avoidance (MACA) [54] is a distributed reservation-based protocol that tries to remove the two problems that exist in the CSMA protocol. Two control frames named RTS (request-to-send) and CTS (clear-to-send) are used for channel access and reservation. Each station (node) that has a frame to transmit sends RTS to the destination along with the length of the message it wants to send to the destination. It then waits for a CTS frame from the destination. All stations sending an RTS message on the medium defer transmission for collision-free delivery of CTS. If the other stations do not hear the CTS with a specified time interval, then they are allowed to send their requests. The stations hearing CTS defer transmission for a period of time required to transmit a frame of the size specified in the CTS. Because each RTS has a source and destination address, the exposed terminal problem can be eliminated. Because collisions occur at the destination, by the use of CTS the hidden terminal problem can be eliminated. The MACAW [55] protocol is an enhancement of MACA that allows stations to choose proper retransmission time and acknowledgments for LLC activity.
There has been a growing interest in the study of the IEEE 802.11 MAC standard which has gained popularity among vendors and users. The 802.11 MAC [56] provides access control functions such as addressing, access coordination, frame check sequence generation, and frame checking. The MAC sublayer performs the addressing and recognition of frames in support of the LLC. This protocol expands on the MACA protocol with link-level acknowledgments and performs collision avoidance, thus falling into the category of CSMA/CA protocols. All nodes are assumed to be time synchronized in this protocol. Time is divided into time slots which are divided into two portions. In the first portion, nodes contend by the exchange of RTS/CTS pairs and backing off if necessary for recontending. In the second portion of the time slot, the node that has gained channel access sends the frame and all other nodes simply wait for the beginning of the next time interval. It is important to note that the size of the frame to be sent is fixed and its size is chosen in a way that it can be sent during the allocated second portion of the time interval. If a node has a frame that is smaller in length, then it is padded with additional blanks. Several research efforts [57], [58] have concentrated on extending the IEEE 802.11 MAC for MANETs. One of the main concerns in trying to extend the IEEE 802.11 MAC is the problem of time synchronization in a multihop environment, as in the case of MANETs.
There has been growing interest in the design of power-efficient MAC layer protocols, especially for MANETs. For example, the IEEE 802.11 has a built-in power-saving feature that allows nodes to awaken themselves during the contention period (the first portion of the time slot) and to go to sleep mode during the second phase of the time slot if it is either not receiving or transmitting. The PAMAS (Power Aware Multiaccess with Signalling) protocol [59],[60],[61],[62],[63] attempts to reduce contention and hence power consumed by use of a special channel. Using this special channel, nodes determine the status of the other channel before transmitting through the regular channel. More information on efficient power usage in wireless systems can be found in references 46 through 49.
In the case of the 802.15.3 draft, [64] the MAC is designed to support fast connection times, ad hoc networking, data transport with QoS, security, dynamic device membership, and efficient data transfer. The 802.15.3 standard is based on the concept of a piconet. Each piconet operates in a personal operating space (POS) that is defined as an approximate 10-m envelope around devices in all directions. Each piconet consists of a piconet coordinator (PNC) and devices (DEVs). The 802.15.3 is a combination of CSMA/CA and time-division multiple access (TDMA) MACs that use superframes for channel access. Each superframe consists of three parts: the beacon, the contention access period (CAP), and contention-free period (CFP). The beacon is used for setting the timing allocations and the channel to use, as well as communicating management. The CAP is used to communicate commands and uses CSMA/CA for access. The CFP is composed of guaranteed time slots (GTS) dedicated for data communication between a pair of DEVs.
16.3.5 Physical Layer
The physical (PHY) layer [65], [66], [67] is a very complex layer that deals with the medium specification (physical, electrical, and mechanical) for data transmission between devices. The PHY layer specifies the operating frequency range, the operating temperature range, modulation scheme, channelization scheme, channel switch time, timing, synchronization, symbol coding, interference from other systems, carrier-sensing and transmit/receive operations of symbols, and power requirements for operations. The PHY layer interacts closely with the MAC sublayer to ensure smooth performance of the network. The PHY layer for wireless systems (such as MANETs) has special considerations that need to be taken into account:
-
The wireless medium is inherently error-prone.
-
The wireless medium is prone to interference from other wireless and RF systems in proximity.
-
Multipath is important to consider when designing a wireless PHY layer, as the RF propagation environment changes dynamically with time. Multipath results in a composite received signal equal to the vector sum of the direct and reflected paths.
-
Frequent disconnections may be caused because of the wireless link. The problem is compounded when the devices in the network are mobile because of handoffs and new route establishment.
PHY layer specifications and its parameters vary depending on the wireless system used. For example, the IEEE 802.11 Standard has a provision for three different PHYs. [68] Another example is the emerging draft standard of IEEE 802.15.3 for wireless personal area networks; Table 16.1 contains PHY parameters defined for IEEE 802.15.3.
| Parameter | Value/Range/Comments |
|---|---|
| Operating frequency | 2.4 to 2.4835 GHz |
| Range | 10m |
| Modulation | Quadrature phase shift keying, eight-state trellis-coded modulation, 11 Mbps |
| Coding | Differential quadrature phase shift keying, none, 22 Mbps |
| Data rate | 16/32/64 quadrature amplitude modulation, eight-state trellis-coded modulation, 33/44/55 Mbps |
| Operating temperature range | 0 to 40 C |
| Base data rate | 22 Mbps (uncoded differential quadrature phase shift keying) |
| PHY preamble | Multiple periods of 16 symbols constant-amplitude zero-autocorrection sequence |
| Symbol rate | 11 Mbps 25 ppm |
| Clock accuracy | 25 ppm |
| Power-on ramp | 2 μs |
| Power-down ramp | 2 μs |
| Maximum transmit power limit (United States) | 50 mV/m at 3 m in at least 1-MHz resolution |
[11]Tanenbaum, A.S., Computer Networks, 3rd ed., Prentice-Hall, Englewood Cliffs, NJ, 1996.
[12]Martin, M.J., Understanding the Network: A Practical Guide to Internetworking, New Riders, Indiana, 2000.
[13]Camp, T., Boleng, J., and Wilcox, L., Location information services in mobile ad hoc networks, Proc. IEEE International Conference on Communications (ICC), 2002, pp. 3318–3324.
[14]Capkun, S., Hamdi, M., and Hubaux, J.P., GPS-free positioning in mobile ad hoc networks, Proc. Hawaii International Conference on System Sciences, January 2001.
[15]Niculescu, D. and Nath, B., Ad hoc postioning system, Internet draft, available at http://www.cs.rutgers.edu/dataman/papers/aps.ps, August 2002.
[16]Li, J. et al., A scalable location service for geographic ad hoc routing, Proc. ACM Mobicom 2000, Boston.
[17]Tanenbaum, A.S., Computer Networks, 3rd ed., Prentice-Hall, Englewood Cliffs, NJ, 1996.
[18]Martin, M.J., Understanding the Network: A Practical Guide to Internetworking, New Riders, Indiana, 2000.
[19]Tanenbaum, A.S., Computer Networks, 3rd ed., Prentice-Hall, Englewood Cliffs, NJ, 1996.
[20]Martin, M.J., Understanding the Network: A Practical Guide to Internetworking, New Riders, Indiana, 2000.
[21]Chandran, K. et al., A feedback based scheme for improving TCP performance in ad hoc networks, IEEE Personal Communication Systems Magazine, Special issue on Ad Hoc Networks, 8 (1), 34–39, 2001.
[22]Ahuja, A. et al., Performance of TCP over different routing protocols in mobile ad hoc networks, Proc. IEEE Vehicular Technology Conference (VTC '2000), Vol. 3, Tokyo, May 2000, pp. 2315–2319.
[23]Dyer, T.D. and Boppana, R.V., A comparison of TCP performance over three routing protocols for mobile ad hoc networks, Proc. ACM Symposium on Mobile ad hoc Networking and Computing, October 2001.
[24]Gerla, M., Tang, K., and Bagrodia, R., TCP performance in wireless multihop networks, Proc. IEEE Workshop on Mobile Computing Systems and Applications (WMCSA), February 1999, pp. 41–50.
[25]Holland, G. and Vaidya, N.H., Analysis of TCP performance over ad hoc networks, Proc. International Conference on Mobile Computing and Networking (MOBICOM), August 1999.
[26]Tanenbaum, A.S., Computer Networks, 3rd ed., Prentice-Hall, Englewood Cliffs, NJ, 1996.
[27]Perkins, C.E., Ed., Ad hoc Networking, Addison Wesley, Reading, MA, 2001.
[28]Johnson, D.B. and Maltz, D.A., Dynamic source routing in ad hoc wireless networks, in Mobile Computing, Imielinki, T. and Korth, H. Eds., Kluwer, Dordrecht, 1996, pp. 153–181.
[29]Park, V.D. and Corson, M.S., A highly adaptive distributed routing algorithm for mobile wireless networks, Proc. IEEE INFOCOM, 1997, pp. 1405–1413.
[30]Toh, C.-K. Associativity-based routing for ad hoc networks, Wireless Personal Commun. J., Special issue on ad hoc Networks, 17 (8), 1466–1487, 1999.
[31]Dube, R. et al., Signal stability based adaptive routing (SSA) for ad hoc mobile networks, IEEE Personal Commun., 36–45, Feb. 1997.
[32]Perkins, C.E. and Bhagwat, P., Highly dynamic destination-sequenced distance-vector routing (DSDV) for mobile computers, Comput. Commun. Rev., 24 (4), 234–244, 1994.
[33]Perkins, C.E. and Royer, E.M., Ad hoc on-demand distance vector routing, Proc. IEEE Workshop on Mobile Computing Systems and Applications (WMCSA), Feb. 1999.
[34]Perkins, C., Ad hoc on demand distance vector (AODV) routing, Internet draft, draft-ietf-manet-aodv-00.txt, Aug. 2002.
[35]Radhakrishnan, S. et al., DST - A routing protocol for ad hoc networks using distributed spanning trees, Proc. IEEE International Conference on Wireless Communications and Networking (WCNC '98), 1998.
[36]Hass, Z. and Pearlman, M., The performance of a new routing protocol for the reconfigurable wireless networks, Proc. International Conference on Communications (ICC 98), June 1998, pp. 156–160.
[37]Ramanathan, R. and Rosales-Hain, R., Topology control of multihop wireless networks using transmit power adjustment, Proc. IEEE InfoCom, Mar. 2000, pp. 404–413.
[38]Ko, Y. and Vaidya, N., Location-aided routing (LAR) mobile ad hoc networks, Proc. MobiCom 98, Dallas, Oct. 1998.
[39]Royer, E.M. and Toh, C.-K., A review of current routing protocols for ad hoc mobile wireless networks, IEEE Personal Communications Magazine, April 1999, pp. 46–55.
[40]Broch, J. et al., A performance comparison of multihop wireless ad hoc network routing protocols, Proc. 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking (MobiCom 98), ACM, Dallas, Oct. 1998.
[41]Das, S.R., Perkins, C.E., and Royer, E.M., Performance comparison of two on-demand routing protocols for ad hoc networks, Proc. InfoCom, Mar. 2000, pp. 3–12.
[42]Racherla, G. and Radhakrishnan, S., Survey of routing algorithms in ad hoc networks, Proc. 4th World Multiconference on Systemics, Cybernetics and Informatics (SCI 2000)/6th International Conference on Information Systems Analysis and Synthesis (ISAS 2000), Orlando, FL, July 23–26, 2000.
[43]Johnson, D.B., Routing in ad hoc networks of mobile hosts, Proc. IEEE Workshop on Mobile Computing Systems and Applications, Dec. 1994.
[44]Obraczka, K. and Tsudik, G., Multicast routing issues in ad hoc networks, Proc. IEEE International Conference on Universal Personal Communication (ICUPC 98), Oct. 1998.
[45]Mauve, M., Widmer, J., and Hartenstein, H., A survey on position-based routing in mobile ad hoc networks, IEEE Network Magazine, 15 (6), 30–39, 2001.
[46]Takai, M., Martin, J., and Bagrodia, R., Effects of wireless physical layer modeling in mobile ad hoc networks, Scalable Networks white paper, http://www.scalable-networks.com/pdf/mobihoc.pdf, Aug. 2002.
[47]Golmie, N. and Mouveaux, F., Modeling and simulation of MAC protocols for wireless devices coexistence performance evaluation, Internet draft, Aug. 2002.
[48]The network simulator — ns-2, http://www.isi.edu/nsnam/ns/, Aug. 2002.
[49]GloMoSim home page, http://pcl.cs.ucla.edu/projects/glomosim/, Aug. 2002.
[50]IETF MANET Charter, available at www.ietf.org/html.charters/manet-charter.html, August 2002.
[51]Perkins, C.E., Ed., Ad hoc Networking, Addison Wesley, Reading, MA, 2001.
[52]Chandra, A., Gummalla, V., and Limb, J.O., Wireless medium access control protocols, IEEE Commun. Surv., www.comsoc.org/surveys, Second Quarter, 2000.
[53]Chandra, A., Gummalla, V., and Limb, J.O., Wireless medium access control protocols, IEEE Commun. Surv., www.comsoc.org/surveys, Second Quarter, 2000.
[54]Karn, P., MACA: a new channel access method for packet radio, Proc. ARRL/CRRL Amateur Radio 9th Computer Networking Conference, Sept. 1990.
[55]Bharghavan, V. et al., MACAW: a media access protocol for wireless LANs, Proc. ACM SIGCOMM, Aug. 1994, pp. 212–225.
[56]IEEE 802.11 Specifications, grouper.ieee.org/groups/802/11/index.html, Aug. 2002.
[57]Chowdary, N. and Radhakrishnan, S., A power efficient enhancement to IEEE 802.11 protocol for multihop wireless networks, Technical report, University of Oklahoma, Norman, 2002.
[58]Lahiri, K., Raghunathan, A., and Dey, S., Battery efficient architecture for an 802.11 MAC processor, Proc. International Conference on Communications (ICC), New York, May 2002.
[59]Singh, S. and Raghavendra, C., PAMAS - power aware multi-access with signaling for ad hoc networks, Proc. IEEE International Personal, Indoor and Mobile Radio Communications Conference, 1998, pp. 153–157.
[60]Srisathapornphat, C. and Shen, C.C., Coordinated power conservation for ad hoc networks, Proc. IEEE International Conference on Communications (ICC), New York, April 28-May 2, 2002.
[61]Agarwal, P., Energy Efficient Protocols for Wireless Systems, Proc. IEEE PIMRC 98, Sept. 1998.
[62]Zorzi, M. and Rao, R,."Error control and energy consumption in communications for nomadic computing, IEEE Trans. Comput., Mar. 1997.
[63]Singh, S., Woo, M., and Raghavendra, C.S., Power-aware routing in mobile ad hoc networking, Proc. International Conference in Mobile Computing and Networking, 1998, pp. 181–190.
[64]IEEE 802.15 Working Group for WPAN, http://grouper.ieee.org/groups/802/15/, Aug. 2002.
[65]Perkins, C.E., Ed., Ad hoc Networking, Addison Wesley, Reading, MA, 2001.
[66]Tanenbaum, A.S., Computer Networks, 3rd ed., Prentice-Hall, Englewood Cliffs, NJ, 1996.
[67]Martin, M.J., Understanding the Network: A Practical Guide to Internetworking, New Riders, Indiana, 2000.
[68]IEEE 802.11 Specifications, grouper.ieee.org/groups/802/11/index.html, Aug. 2002.
EAN: 2147483647
Pages: 239