Tunnel Endpoint Discovery
| Tunnel Endpoint Discovery (TED) is a logical extension to the dynamic crypto maps that allows an endpoint to dynamically, proactively discover a previously unknown peer. TED therefore allows peers to proactively initiate the negotiation of IPSec tunnels with unknown peers when the local peer is brought online. TED accomplishes these tasks by sending TED probes out of the local VPN endpoint's crypto-enabled interfaces. The remote peer does not need to have TED configured in order to be discovered by inbound TED probes. As we will see when configuring TED, VPN devices that receive TED probes on interfaces that do not have TED configured can successfully negotiate a dynamically initiated tunnel using TED. We will use Figure 12-4 to demonstrate how a TED-enabled router can dynamically determine the remote endpoint. Figure 12-4. Using TED to Initiate IPSec VPN Tunnel Negotiation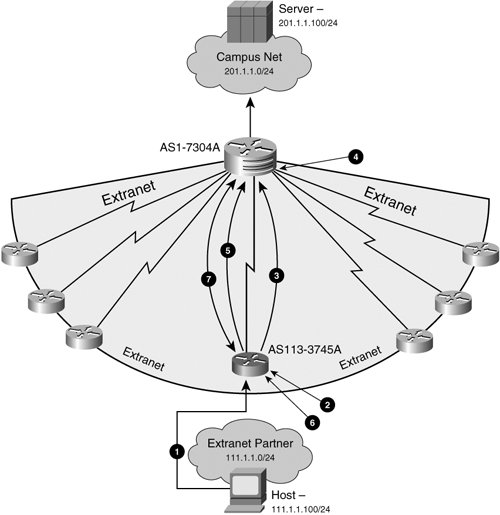 In the extranet topology configured in Figure 12-4, a host on the extranet partner site wants to communicate with a server on the central campus. The extranet partner's local VPN endpoint, however, does not know the peer address with which to build a tunnel. Instead, TED has been enabled on the extranet partner router so that the peer address can be dynamically discovered through the following steps (also referenced in Figure 12-4):
In the next section, we will explore TED configuration and verification steps required. The configurations will follow the steps and dynamic crypto map procedures outlined previously in this chapter. TED Configuration and VerificationIn this configuration, we will discuss enabling TED as well as the appropriate steps to take when verifying IPSec VPN operation using TED. As illustrated in Example 12-8, TED is only allowed on dynamic crypto maps. As a result, the only two prerequisites for the use of TED are the use of ISAKMP (TED is not supported with manual IPSec keying) and the use of dynamic crypto maps. Example 12-8. Enabling Tunnel Endpoint Discovery
Enabling TED in this fashion allows AS1-7304A to initiate IPSec tunnel negotiation with AS113-3745A. Without TED, traffic tagged as IPSec on AS1-7304A would be dropped if a remote peer had not initiated a VPN connection previously. With TED, however, this IPSec-tagged traffic would initiate ISAKMP Phase 1 negotiation to the remote peer, and traffic would therefore not be dropped. |
EAN: 2147483647
Pages: 113