Characteristics of an Effective VPN
| VPNs exist to effectively, securely, and privately protect data that is transmitted between two networks from the common, shared, and separately maintained infrastructure between the two networks. In order to effectively perform this task, there are four goals that a confidential VPN implementation must meet:
Incorporating the appropriate data confidentiality capabilities into a VPN ensures that only the intended sources and destinations are capable of interpreting the original message contents. IPsec is very effective at encrypting data using the encapsulating security protocol (ESP), described in RFC 1827. Utilizing ESP, IPsec transforms clear text in to encrypted data, or cipher text. Because ESP-transformed messages are only sent across in their ciphered representations, the original contents of the message are kept confidential from would be interceptors of the message. Figure 1-1 illustrates a high-level exchange of encrypted message between to endpoints, James and Charlie. Figure 1-1. Confidentiality and Authenticity in Encrypted Communications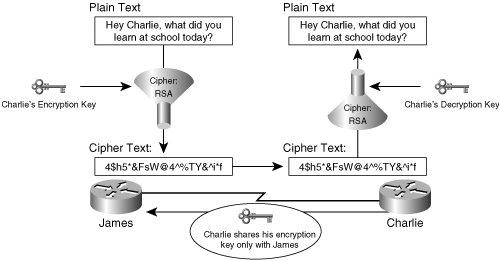 Encrypting messages relies on the use of a key to encrypt clear text and to decrypt ciphered messages. In the exchange of messages in Figure 1-1, both James and Charlie require the appropriate keys to encrypt and decrypt communications from each other. Assuming that these keys were exchanged or derived securely (for example, via a Diffie-Hellman exchange, which is discussed in detail in Chapter 2, "IPsec Fundamentals"), when James receives a message from Charlie that he is able to decrypt, he can be assured that the message has been delivered with full confidentiality, and vice versa. Hashes and digital signatures protect the integrity of a specific communication of data. Hashes and digital signatures append unique messages to the original message before transmission that ensure that the message has not been tampered with in transit. Figure 1-2 illustrates the operation of a hash performed on a message to ensure data integrity. Figure 1-2. Data Integrity, Secure Hashes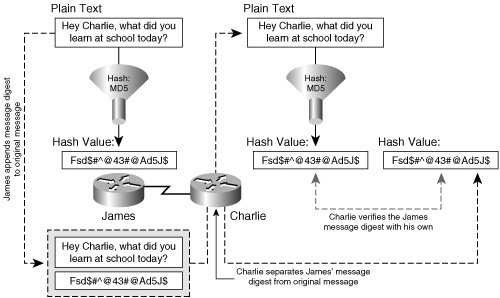 By providing a unique fingerprint specific only to the sender of the message, a digital signature also provides the receiver a method of message authentication and sender non-repudiation. Notice in Figure 1-3 that digital signatures require the use of a public decryption key unique to the sender's private encryption key. The use of this cryptographic keypair thus guarantees message authenticity, ensuring that the message was sent from the authentic origin, and safeguards against sender non-repudiation, preventing a situation in which the sender of a specific message intentionally and falsely denies their transmittal of the message. While a secure hash can provide data integrity, digital signatures provide added levels of security by offering message authentication and sender non-repudiation, the operation of which is illustrated in Figure 1-3. Figure 1-3. Message Authenticity and Data Non-Repudiation with Digital Signatures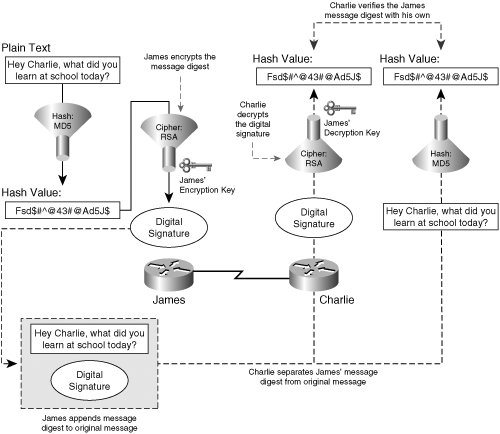 |
EAN: 2147483647
Pages: 113