4.10. Firewalls
| | ||
| | ||
| | ||
4.10. Firewalls
I have considered controlling file access in sufficient detail, but there are other areas, in which access rights have to be controlled. Nowadays, computer operations are impossible without connecting to a local network or to the Internet. Consequently, before putting your server into operation, you have to limit outside access to the computer and to some of its ports.
Computers are protected from attacks originating on the network by firewalls. Some Linux services can also be configured to control network access, but they will be considered separately for each individual service. I would not recommend relying exclusively on a service's network access control capabilities. As you should remember, there are bugs in all software, and if a service's network access control feature is backed up by a firewall, it will not become the worse for it.
A firewall is the foundation of the network security and the first line of defense from external invasion. When a firewall is installed, hackers trying to break into the computer through the network will have to pass through the firewall first, and only after they succeed can they move on and try to enter the file system. At this point, they will have to penetrate the second line of defense: the file and directory access permissions.
Why, then, do I consider the first line of defense after the second? Because a firewall protects only against network attacks, whereas proper regulation of access rights protects against both local hackers and unscrupulous users that have direct access to the computer. Both defense lines are important. Every little thing counts where security is concerned , and you should pay attention to all seemingly-insignificant details.
A firewall can prevent access both to the computer as a whole and to its individual ports used by services. It is not, however, a 100% guarantee against a successful break-in. It just checks that the network packets meet certain requirements; it cannot guarantee that a right packet was sent by the right person.
The simplest way of bypassing a firewall is to use a fake IP address. Once I worked with a company where regular users were forbidden to use the Simple Mail Transfer Protocol (SMTP) and Post Office Protocol (POP3) (connected to ports 25 and 110, respectively). I belonged to this category of users and could not receive or send email. My boss, however, belonged to the privileged class and had this access. Neither could the Web interface be used to access mail services; this capability was blocked at the proxy-server level. But all these security measures did not prevent me from sending an email when I really had to. Here is how I did this:
-
Waited for my boss to leave his office
-
Turned off his computer
-
Changed my IP address to the IP address on his computer
-
Sent the email and changed my IP address back to what it was supposed to be
When my boss came back, he did not make much of his computer being off; he thought that is simply hung and did not suspect a thing. So I used the service I was not supposed to use without any adverse consequences for having done this.
Although there are many ways to bypass a firewall (not counting those made available by bugs), a properly-configured firewall will make the lives of the administrator and the security specialist much easier.
In Linux, the firewall function is performed by a program that filters information based on a set of certain rules clearly prescribing, which packets can be processed or sent onto the network and which cannot. This makes most attacks fail without even having entered the computer, because the firewall does not let the services even see potentially dangerous packets.
A firewall can be installed on each individual computer (to provide protection according to the tasks performed) or at the network entrance (Fig. 4.2). In the latter case, the firewall provides common protection for all of the network's computers.
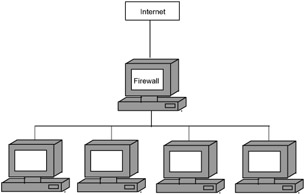
Figure 4.2: A network firewall
If there are many computers in a network, installing a firewall on all of them and configuring, updating, and maintaining the numerous firewalls will be quite difficult. Using a single server as a dedicated firewall for the entire network makes this task easier. Better still, if this computer also acts as a gateway or a proxy server for the rest of the network's computers. In this case, any hackers trying to penetrate the network will only see this computer, with the rest of the machines hidden behind the firewall it provides. To break into any of the other network's computer, hackers will have to break into the firewall computer first. This makes the task of protecting the network much easier. Proxy servers are covered in more detail in Chapter 9 .
But there is one weak link in all firewalls: They are software-implemented and use resources of the server they are installed on. Modern routers can also provide many functions performed by Linux firewalls. On the other hand, Linux systems are often used as routers to keep the cost of the system low by putting to use old computers that cannot be used for any other contemporary task.
4.10.1. Filtering Packets
The main, but not the only, task of a firewall is filtering packets. There is already a firewall built into Linux, and you do not have to install it separately. In fact, there are two firewalls: iptables and ipchains . They make it possible to control the Transmission Control Protocol (TCP), User Data Protocol (UDP), and Internet Control Message Protocol (ICMP) traffic going through the computer. Because TCP is the main transport for all other main Internet protocols FTP, HTTP, and POP3 filtering TCP traffic allows all these services to be protected.
All requests from or to the Internet must pass through the firewall, which examines them for compliance with the specified rules. Packets in full compliance are let through. But if at least one of the rules is not met, the offending packet may be deleted in one of the following two ways:
-
Denied Without informing the sending party about this
-
Rejected Informing the sending party about this
I would not configure my firewall in the latter way; doing so would provide hackers with extra information. It is better to delete offending packets without informing the sending party and have it think that the service is simply unavailable. But this is fraught with the danger of legitimate users experiencing problems in case of incorrect firewall configuration. Suppose that you mistakenly blocked access to port 80, used by the Web service. If a client program tries to access the Web server behind the firewall and does not receive an answer, it will wait until the timeout. The timeout value can be infinite for some programs, and they will hang. You will have to correct the firewall configuration error to let the user work trouble-free.
Moreover, package-rejection messages are sent using ICMP and increase channel traffic. A hacker can take advantage of this to carry out a denial-of-service (DoS) attack to flood your channel with superfluous package-rejection messages. DoS attacks can be directed not only against traffic but also against computer resources. A hacker can run a program repeatedly asking to establish a connection with a disabled port, which will cause your computer to waste resources (processor time, memory, etc.) examining the packets and sending rejection messages. If packets arrive at a fast rate, the server may not be able to handle the load and may stop answering requests from the legitimate users.
Firewall filters can be configured using one of the following two principles:
-
Everything that is not forbidden is permitted.
-
Everything that is not permitted is forbidden.
The latter way is more secure, because you start by forbidding everything. Then, as a need arises, you can allow access for specific users to specific services. You should adhere to this policy when configuring your firewall filters for incoming packets.
When starting with everyone being permitted everything, it is easy for the administrator to simply forget to limit some access rights and discover the oversight only when the system is penetrated and damage has been inflicted.
4.10.2. Filter Parameters
Packet filtration is performed by the following main packet parameters: the source or destination port number, the sender or recipient address, and the protocol used. As you already know, firewalls supports three main protocols (TCP, UDP, and ICMP) that form the foundation for all services (FTP, HTTP, POP3, and others).
Note that filtration can be bidirectional. Filtering incoming packets allows any attempts to break into the server to be fended off at the earliest stage.
But why filter outgoing traffic? At first it may seem senseless, but there are important reasons for this. Outgoing traffic can be less innocent than you may think. It may be generated by Trojan horse programs sending confidential information gathered on your hard drive to some email address, or connecting with the author's server to download further instructions from there.
Some specialized programs generate outgoing traffic to bypass the firewall. Suppose you disabled some port for incoming traffic. A hacker can bypass this prohibition by infiltrating a program onto the server that will redirect traffic from the disabled port to an enabled one, similar to OpenSSL tunneling.
It will take a professional all but 5 minutes to write such a program.
There are many loopholes to penetrate your computers, and your task is to close as many of them as possible. Consequently, you must control traffic going in both directions.
Protocols
The base data transfer protocol for HTTP, FTP, and other protocols is TCP. It will make no sense to prohibit it, because this will deprive you of all the niceties of the World Wide Web. TCP transmits data by first establishing a connection with the remote host and only then conducting data exchange. This makes faking the IP address of any of the connection parties more difficult and sometimes even impossible.
UDP is the same level protocol as TCP, but it transmits data without establishing a connection. This means that the protocol simply sends its data onto the network to a specified address without ensuring that this address is reachable first. In this case, there is no protection against faking the IP address, because the attacker may specify any address as the source and the receiving side will see nothing suspicious. Unless there is a justifiable need, I prohibit UDP packets in both directions.
ICMP is used to exchange control messages. It is used by the ping command to check the connection with the remote computer and by hardware and software components to inform each other of errors. This protocol is handy, and if it were only used as intended there would not be problems with it. But nothing is perfect in this life, and ICMP has often been used to perpetrate DoS attacks. Forbid this protocol by any means. If exchanging control messages cannot be avoided, try to find another program to do this, but do get rid of ICMP.
Port Filtration
The first thing that you have to pay close attention to is ports. Suppose that your Web server is open to all users. Also suppose that it serves absolutely safe scripts (this is from the realm of fantasy, but suppose this for the example's sake) and/or static HyperText Markup Language (HTML) documents. Moreover, all software is current on updates and has no vulnerabilities. Does all this make the server really secure? Yes, but only for the time being. Sooner or later, you will have to update your absolutely secure scripts (dream on) and static HTML documents. It is doubtful that you will use diskettes as the update vehicle and will need some other way to upload the update. Most often, files are transferred using an FTP service, and this is where you breach a hole in the impenetrable wall of your server fortress.
Only the most secure programs should use the FTP access and the strongest passwords; nevertheless, sooner or later hackers will break into this service. Passwords can be picked, stolen from some user's computer, tricked out of some gullible employee with the help of social engineering, or obtained in other countless ways. If there is a channel leading into the system, it is vulnerable, because hackers will not be trying to break in through nonexistent channels but will concentrate their efforts on something that will eventually yield to their relentless digging. Although the first one to try to break in may walk away with nothing to show for his or her pains, the second, the third, or the hundredth may get lucky, break in on the first try, and destroy everything he can lay his hands on.
So you should establish a policy on the server, according to which port 80 will accept all connections but port 21 (the FTP service) will only accept connections from a certain IP address. Then, unless the would-be computer burglar knows this IP address, all of his traffic will be cut off at the port and he will spend years trying to pick the password.
You should first disable all ports and then start enabling those that are necessary. This advice, however, is difficult to follow for a server that runs a firewall for the entire network, because different computers require different services. Opening all ports on the firewall server would be the same as opening all ports on all of the network's computers. You could use IP addresses to form the rules for the dedicated server firewall, but using a firewall on each of the network's computers would be more practical. In this case, the firewall on each of the computers can be configured to provide the protection required by the particular tasks executed on them. Only port 80 will be seen from the Internet for Web servers, and only port 21 will be visible for FTP servers.
Address Filtration
Based on the preceding information, you can see that IP address can also be used for traffic filtering, although the maximum effect is achieved by combining the port and address filtering.
Suppose that there are two Web servers on your network, which happens quite often. One of the servers is made available for all Internet visitors , and the other services only company users (an intracompany site). In this case, it will be logical to divide the information into two categories: one for internal use and the other for external. Then the closed server can service only the local network traffic regardless of what port it passes through.
The inside server should be isolated from the Internet altogether.
Consider another example. Suppose you have an Internet store and you sell only within your city or town. In this case, you should only allow access to the server from IP addresses within your city and disallow access to all others. But this task is rather difficult to implement.
Filtering Out Undesirable IP Addresses
A few years ago, the RegNow ( www.regnow.com ) service (which offers middleman services for developers of shareware programs, providing secure payment services and collecting money from the purchasers ) attempted to restrict access from suspicious IP addresses. This was a fully logical step. Some countries , on one hand, teem with hackers and, on the other hand, experience an extreme scarcity of honest software buyers . The executives at RegNow placed African and some eastern European countries including, because of its penchant for free stuff, Russia into this category.
This step was justified because carding was flourishing in many of those countries. (Carding is when stolen credit-card information is used to purchase merchandise on the Internet.) To fight this evil, at least the greater part of it perpetrated by the citizens of those countries, the service disallowed access to their server from whole batches of IP addresses. The effect was nil, because the prohibition turned out to be easy to bypass. All that a lover of free stuff had to do to break through the barrier was use one of the anonymous proxy servers in the United States or Canada. The bona fide customers from the banned countries, on the other hand, experienced serious problems and were not able to use the service to get paid for the services they had provided.
The serious shortcomings of this filter resulted in it being removed shortly after it was put in place, and the RegNow service has not tried to use it since. It is too difficult to filter out all possible proxy servers, and the effect of this filtering is negligible. The problems it causes respectable users, however, may well cost a company its good reputation forever. Thus, sometimes you have to make a choice between security and convenience, and the perfect balance between the two is quite difficult to strike.
Filtering out Incorrect IP Addresses
There was another real-life case, in which a server was stumped by the source IP address. When this server received an invalid data packet, it would issue the sender a message about the data being wrong. The problem was that the attackers were sending packets, in which the source IP address was the same as the destination IP address; that is, both addresses were those of the server the packets were sent to. When the server sent the error message to a packet's sender, it would send the message to itself and would receive the invalid packet again. In this way, the packet would enter an endless loop. Sending thousands of such packets, the malefactors turned the server into a full-time wrong-packet answering machine.
I have not heard of such attacks for a long time, but it cannot be ruled out they will not happen. There are numerous IP addresses that should be filtered out and not let into your network.
Moreover, I recommend filtering out packets from reserved addresses or addresses that cannot be used on the Internet. The following are descriptions of such addresses:
-
127.0.0.1 This address is used to specify the local machine (local host); consequently, no packet can originate from this address on the Internet.
-
10.0.0.0 to 10.255.255.255 This range of IP addresses is used for private networks.
-
172.16.0.0 to 172.31.255.255 This range of IP addresses is used for private networks.
-
192.168.0.0 to 192.168.255.255 This range of IP addresses is used for private networks.
-
224.0.0.0 to 239.255.255.255 This range of IP addresses is used for broadcasting purposes and is not assigned to computers; consequently, no packets can originate from them.
-
240.0.0.0 to 247.255.255.255 This range is reserved for future Internet use.
All of the preceding addresses are invalid for Internet use, and you should not let packets from these addresses breach your firewall.
Linux Filtration Features
The Linux kernel already has built-in functions for filtering packets according to specified rules. But these functions provide bare-bones functionality and require a tool to configure the rules.
Linux offers two application packages for this: iptables and ipchains . Deciding which of them is better is a close call, because they offer similar functionalities. But many professionals choose ipchains . What you choose is up to you.
The Linux kernel contains the following three main rule chains:
-
Input For incoming packets
-
Output For outgoing packets
-
Forward For transiting packets
Users can create their own chains linked to a certain policy; this subject, however, is beyond the scope of this book.
Linux checks all rules in the chain, which is selected depending on the direction of the transfer. A packet is examined for meeting each rule in the chain. If it does not meet at least one rule, the system decides whether to let the packet through and carries out one of the actions specified for this rule: deny, reject, or accept.
This means that if a packet is found not to conform to one of the rules, it is no longer checked for conforming to the following rules in the chain. For example, suppose that you want to open port 21 for yourself only. This can be done by the following chain of two rules:
-
Prohibit all incoming packets on port 21.
-
Allow packets originating from address 192.168.1.1 to port 21.
At first glance, everything seems to be right: Access to port 21 is closed to all packets except those originating from address 192.168.1.1. The problem is that a packet arriving to port 21 from address 192.168.1.1 is processed in compliance with rule 1 first, and because "all packets" includes those packets arriving from address 192.168.1.1, the system rejects it and never evaluates it against the second rule.
For the policy to work, the places of the rules have to be swapped. Then an arriving packet is first checked for originating from address 192.168.1.1 and is let through if it is. If it is not, it is evaluated against the second rule, triggering the prohibition for all packets to enter port 21.
Packets routed to other ports do not meet the criteria for the rules and will be processed in the default order.
4.10.3. Firewall: Not a Heal-All
Don't be lulled into a false feeling of security after having installed a firewall: There are many ways to circumvent not just a specific firewall but all of them.
Any firewall is just a security guy at the front door. But the front door is never the first choice as a point of entry for a burglar. Burglars usually opt for the back door or a window. For example, Fig. 4.2 shows a protected network and the front door: the Internet connection through a dedicated computer running a firewall. But if one of the network's computers happens to be equipped with a modem but without a firewall, this will create a back door to the network, without any doorman standing guard around the clock
I have seen servers, for which Internet access was permitted from only a certain list of IP addresses. The administrators believed that this measure would protect them from hackers. They are mistaken here, because an IP address is easy to fake.
At one time, I worked with a company where Internet access was controlled by IP addresses. My monthly Internet traffic was limited to 100 MB, while my neighbor had unlimited access. To conserve my traffic, I did not use my quota to download large files but only to view Web pages. When I needed to download something, I did the following:
-
Waited until the neighbor's computer was not in use, for example, when the owner went to lunch .
-
Slightly pulled the network cable on the neighbor's computer out of the network card socket to break the connection.
-
Assigned my computer the IP address of my neighbor and downloaded all that I wanted to download.
-
Having finished, returned the IP addresses and the network cable to their regular places.
In this way I was able to download all I needed over a month.
I then upgraded the process by installing a proxy server on my neighbor's computer and did all of my downloading through it. I was not selfish, so I shared this good thing with my coworkers, and we all connected to the Internet through this IP address with unlimited traffic.
With modern firewalls, simply switching the IP address will not help you enter the system. The identification techniques they use now are much more sophisticated than simple IP-address checking. Switching the IP address may only provide more privileges within the system, and even this is only the case if the network is not configured properly. But administrators worth their salt will not allow such machinations even within the network, using MAC addresses and access passwords to assign access rights.
A firewall is a program that runs on a computer under the control of the operating system (a software firewall) or on a physical device (a hardware firewall). But, in either case, this program is written by humans who, as we all well know, are prone to error. Just like with the operating system, the firewall needs to be updated regularly to repair the programming bugs that are inevitably present in all software.
Consider the port protection. Suppose your Web server is protected by a firewall with only port 80 enabled. Well, that's all the ports that a Web server needs! But this does not mean that other protocols cannot be used. A technique called tunneling can be used to create a tunnel to transfer data of one protocol within another protocol. This was the technique used by the famous Loki attack, which makes it possible to send executable commands to the server within ICMP packets of the echo request type (this is a regular ping query) and to return responses within ICMP packets of the echo reply type ( ping reply).
A firewall is a tool for protecting data, but the main protector is the administrator, who must constantly keep watch over the system security and prevent, detect, and ward off any attack. A new type of attack can penetrate the firewall because the firewall can only recognize those attacks, for which it has algorithm samples in its database. To be able to process a nonstandard attack, the system must be monitored by the administrator, who will be able to notice and react to any unusual changes in the main parameters.
A password or a device like touch memory or smart card is often needed to pass through a firewall. But if the password is not protected, all of the money invested in the firewall will be wasted . Hackers can obtain the password in one of a number of ways and use it to penetrate the firewall. Many systems have been broken into in this manner.
Passwords must be strictly controlled. You must control each user account. For example, if an employee with high system privileges quits, his or her account must be disabled immediately and all passwords, to which the employee had access, must be changed.
I was once called to a company to restore data on its server after they fired the administrator. He considered the termination of his employment unfair and, a few days later, destroyed all information contained on the main server without any problems. Even the well-configured firewall did not stop him. This happened because the firewall was configured by the malefactor himself. This type of thing should never be allowed to happen, and the firewall must be configured so that not even a network administrator can break through.
I always recommend to my clients that only one person knows the highest level firewall password. In a corporation, this should be the chief of the information-processing department. In no case should it be a regular administrator. Administrators come and go, and there is a chance of forgetting to change some password after the next administrator leaves .
4.10.4. Firewall: As Close to Heal-All as You Can Get
From the preceding section, you may get the impression that firewalls are a waste of money. This is not the case. If the firewall is properly configured, is constantly monitored, and uses protected passwords, it can protect your computer or network from most problems.
A quality firewall provides many levels of checking access rights, and a good administrator should never be limited to using just one. If you use only the IP address check to control Internet access, you can start looking for a bank loan to pay your Internet bill, because this address can be easily faked. But a system, to which the access is controlled by the IP address, MAC address, and password, is much more difficult to compromise. Yes, both MAC and IP addresses can be faked. To make sure that they are not, individual computers can be tied to specific port switches. In this case, even if the hacker learns the password, he or she will have to use it at the computer, to which it is assigned. This may require some ingenuity.
The protection can, and must, be multilevel. If you have data that need protecting, use the maximum number of protection levels. There is no such thing as too much security.
Imagine your average bank. Its entrance door will be much stronger than your average house or apartment door and equipped with an alarm system to boot. But if someone comes to do his or her banking in a tank, these protections will be of little use.
A firewall is akin to such an improved door protecting against small-fry hackers, which is what most hackers are. But it will not protect against a professional hacker, or at least not for long.
In addition to protecting the premises with a good door, banks keep their money in safes, which are themselves are placed into vaults. Money kept in a bank can be compared to secret information stored on a server, and it must be provided with maximum protection. This is why banks keep their money in safes equipped with sophisticated locks that take thieves a long time to open. While they are at it, there's more than enough time for the cops to arrive on the scene.
To extend the bank safe analogy to servers, here the role of the safe is played by encryption. So, even if a hacker bypasses the firewall and reach the data on the server, it will take too much time to decrypt them. He or she can be nabbed while still sitting at the desk. But even if the hacker carries the safe away to crack at his or her leisure, meaning downloading the data to decrypt them without being bothered, the chances are great that the information will become obsolete by the time it can be decrypted. The important thing here is that the encryption algorithm and the key are sufficiently sophisticated.
4.10.5. Configuring a Firewall
The easiest way to configure the Linux firewall is to use the built-in graphical utility. Load the KDE graphical shell and select the Main Menu/System/Firewall Configuration menu sequence. This will open the Firewall Configuration dialog window with two tabs on it: Rules and Options .
First, open the Options tab (Fig. 4.3). Here you can specify default actions for each of the packet types and restrict ICMP packet transit.
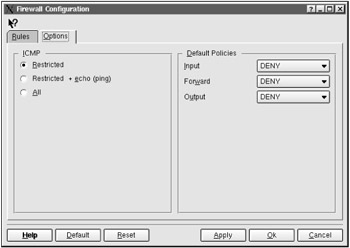
Figure 4.3: The Options tab
On the Rules tab (Fig. 4.4), filtration rules can be created, deleted, or edited. A rule is created by clicking the Add button. This will open the dialog window shown in Fig. 4.5.
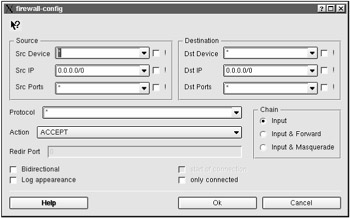
Figure 4.4: The Rules tab
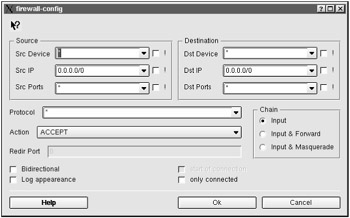
Figure 4.5: The dialog window for adding new rules
Do not change any settings for now. Just familiarize yourself with the appearance of the Firewall Configuration utility and its capabilities. You can engage in configuration activities later, when you learn how to work with using the ipchains program, which is used to configure the firewall from the command line.