Designing Internet Connectivity for a Company
| In today's interconnected world, most businesses require a connection to the Internet. The greatest challenge for a network administrator is to provide a connection that is transparent to a user while at the same time secure for the organization. There are many components from which we can choose to provide this connection. The components we choose will largely depend on the needs of the users and the number of users who are served by that component. In this section, we examine the most common components used to provide secure Internet access. These are the following:
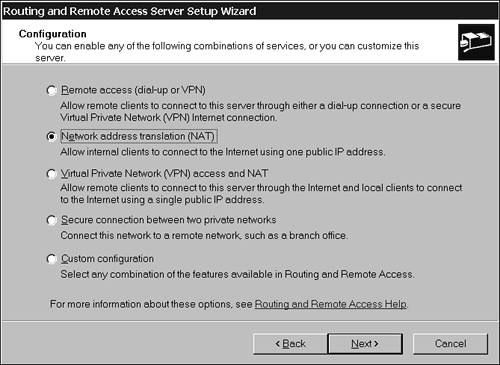
Let's now examine each of these components and their relationship to the physical design of our network infrastructure. Internet Connection SharingInternet Connection Sharing (ICS) is built into all Windows 2000 and Windows Server 2003 operating systems, including Windows 2000 Professional and Windows XP Professional. It provides an Internet connection hosted by one machine that can be used by many machines. This connection provides automatic address assignment and name resolution options. You can configure Internet Connection Sharing through Routing and Remote Access on a server or through Network Connections on a client. The only additional hardware required is another network interface card for the computer hosting the ICS. Clients of ICS can be configured to obtain their IP addresses automatically, just as if they were getting them from a DHCP server. When you configure the ICS host, the system sets up a private network with its IP address as 192.168.0.1/16. All clients set to obtain an address automatically will then receive an address in the 192.168.0.0/16 network. One of the host network interfaces will have the private address, and the other will have the address obtained from the Internet service provider (ISP). Although ICS can be used with your server, it was designed for use when you have a small group of clients and no server, such as in a small remote office. In this case, one client hosts the connection to the Internet that all clients use. In a larger environment with a server, you would probably use a different component. Network Address TranslationSmall- to medium-sized networks use network address translation (NAT) services to provide users with access to the Internet. These services are transparent to the user. Their main benefit is that they hide the addresses used in the private network by translating every address that goes through them to an address that will be used on the Internet. This protects a network from spoofing. Another benefit is that the organization can have fewer registered IP addresses. This saves the organization money and saves IP addresses. You can actually have hundreds of private IP addresses translated to one registered address and give those hundreds of users simultaneous and separate access to the Internet. Network address translation can be performed by many different components. Windows Server 2003 has NAT services built into Routing and Remote Access. When you use a Windows Server 2003 computer as a router, you can easily add the NAT services. You can find this selection by right-clicking on the server and then selecting Configure and Enable Routing and Remote Access. Figure 6.4 illustrates this configuration setting. You can also set up network address translation on firewalls, routers, and even some hubs. Figure 6.4. You can set a routing and remote access server for network address translation.
Proxy ServerLarger organizations generally use a proxy server to provide Internet access for their users. A proxy server performs network address translation by making the request for an address on behalf of the client, but can also provide more granular control of which users or user groups have access to the Internet and when they have access. In addition, a proxy server can be configured to filter and control access to certain Internet sites or groups of sites. Finally, proxy servers can cache the Internet requests from users. This cache can be used for greater security and control as well as to provide faster response to users seeking a frequently used site. Microsoft and many other software development companies offer proxy server products. FirewallAs its name implies, a firewall provides a separation between two things or places. In this case, the firewall provides a separation of two networks. Typically, one of the networks is the Internet, but firewalls can be used between two private networks as well. There are basically two types of firewalls:
We now discuss each of these and their effect on the physical design of our network. Packet FilteringPacket filtering is letting some packets go through the firewall while discarding (destroying) others. This can be performed in either direction (in or out) or in both directions at once. Some packet-filtering firewalls use software to make decisions, whereas others use hardware that is specifically designed for this purpose. Firewalls typically filter by IP address, protocol, and port. For example, a firewall could be used to filter all ICMP (ping) traffic from entering your network and/or to filter all FTP (file transfer) traffic from leaving you network. The first example would protect the network from a denial of service attack using pings. The second example would protect you from a user sending valuable company information to some other company. In either case, the firewall examines each packet to make its decisions on whether to let the packet through or to discard it. Stateful inspection is a firewall architecture that works at the network layer. Unlike static packet filtering, which examines a packet based on the information in its header, stateful inspection tracks each connection traversing all interfaces of the firewall and makes sure it is valid. This is also referred to as dynamic packet filtering. Servers, as their name implies, are generally meant to serve! They are therefore vulnerable because they generally come out of the box with many services and ports open and ready for business. The Web Edition of Windows Server 2003 addresses this issue by closing many of these vulnerabilities during a default installation. A firewall is a server that is physically located between the Internet and the other servers in a network and provides the required security for the network. It makes sure that the packets that enter and leave the network are there for good reason, and it generally records everything that happens. A firewall can provide an additional authentication service for users attempting to send packets through it. The main benefit of a firewall is that it enables you to leave the services and ports on the servers on the inside of the network in their active and ready status. Because a firewall is used to separate your network from other networks, it should be located on the perimeter of the network. In fact, all traffic in and out of the network should be routed through the firewall. Any traffic that can go around the firewall represents a security risk that should be avoided. That means the firewall must be able to perform at a pace that is fast and efficient, so as not to create a bottleneck. This should be taken into consideration when you choose between the many types of firewall hardware and software on the market. |
EAN: 2147483647
Pages: 152
- The Four Keys to Lean Six Sigma
- Beyond the Basics: The Five Laws of Lean Six Sigma
- Making Improvements That Last: An Illustrated Guide to DMAIC and the Lean Six Sigma Toolkit
- The Experience of Making Improvements: What Its Like to Work on Lean Six Sigma Projects
- Six Things Managers Must Do: How to Support Lean Six Sigma