Logical Access Controls
| As described earlier, logical access controls are security features that control how users and systems communicate and interact with other users or systems. These are often the primary safeguards for systems software and data. Three main components of access control exist:
A subject's access rights should be based on the level of trust a company has in a subject and the subject's need to know (principle of least privilege). As a rule, access-control mechanisms should default to "no access," to provide intentional (explicit) access and to ensure that security holes do not go unnoticed. The access-control model is a framework that dictates how subjects can access objects and defines three types of access:
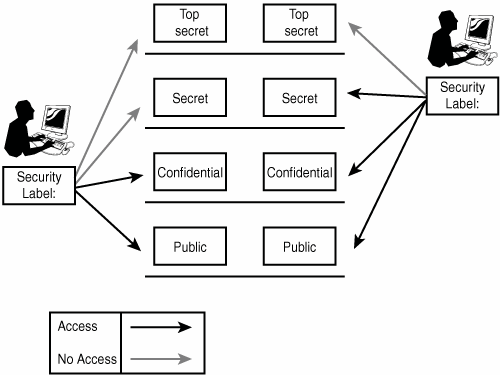
In implementing mandatory access control (MAC), every subject and object has a sensitivity label (security label). A mandatory access system is commonly used within the federal government to define access to objects. If a document is assigned a label of top secret, all subjects requesting access to the document must contain a clearance of top-secret or above to view the document. Those containing a lower security label (such as secret or confidential) are denied access to the object. In mandatory access control, all subjects and objects have security labels, and the decision for access is determined by the operating or security system. Mandatory access control is used in organizations where confidentiality is of the utmost concern. Nondiscretionary access control can use different mechanisms based on the needs of the organization. The first is role-based access, in which access to an object(s) is based on the role of the user in the company. In other words, a data entry operator should have create access to a particular database. All data entry operators should have create access based on their role (data entry operator). This type of access is commonly used in environments with high turnover because the access rights apply to a subject's role, not the subject. Task-based access control is determined by which tasks are assigned to a user. In this scenario, a user is assigned a task and given access to the information system to perform that task. When the task is complete, the access is revoked; if a new task is assigned, the access is granted for the new task. Lattice-based access is determined by the sensitivity or security label assigned to the user's role. This scenario provides for an upper and lower bound of access capabilities for every subject and object relationship. Consider, for example, that the role of our user is assigned an access level of secret. That user may view all objects that are public (lower bound) and secret (upper bound), as well as those that are confidential (which falls between public and secret). This user's role would not be able to view top-secret documents because they exceed the upper bound of the lattice. Figure 4.1 depicts this access. Figure 4.1. Lattice-based access control. Another method of access control is rule-based access. The previous discussion of firewalls in Chapter 3, "Technical Infrastructure and Operational Practices and Infrastructure," demonstrated the use of rule-based access implemented through access control lists (ACLs). Rule-based access is generally used between networks or applications. It involves a set of rules from which incoming requests can be matched and either accepted or rejected. Rule-based controls are considered nondiscretionary access controls because the administrator of the system sets the controls rather than the information users.
IS auditors should review access control lists (ACL) to determine user permissions that have been granted for a particular resource. Restricted interfaces are used to control access to both functions and data within applications and through the use of restricted menus or shells. They are commonly used in database views. The database view should be configured so that only that data for which the user is authorized is presented on the screen. A good example of a restricted interface is an Automatic Teller Machine (ATM). When you access your bank account via an ATM, you can perform only certain functions (such as withdraw funds or check an account balance); all of those functions are restricted so that transactions are applied to only your account. An access-control matrix is a single table used to cross-reference rights that have been assigned by subject (subject capabilities) with access rights that are assigned by object (access-control list). The matrix is essentially a combination of a capabilities table and access control list(s). The capability table specifies the rights a subject possesses pertaining to specific objects, bound by subject. The capability corresponds to the subject's row in the access-control matrix. The access-control list (ACL) is a list of subjects that are authorized to access a specific object. The rights are bound by object. The ACL corresponds to a column of the access-control matrix. Figure 4.2 outlines a simple access-control matrix for a single database and a group of users. It is important to keep in mind that ACLs are generally more granular than the figure. Figure 4.2. Access control list. In Figure 4.2, John, who is a data entry operator, is responsible for address updates within the test database. He is allowed access to read and update records but does not have access to create new records. Jane is responsible for entering new customers in the database and, therefore, has the capability to read and create new records. Neither John nor Jane can delete records within the database. The administration of access control can be either centralized or decentralized and should support the policy, procedures, and standards for the organization. In a centralized access control administration system, a single entity or system is responsible for granting access to all users. In decentralized or distributed administration, the access is given by individuals who are closer to the resources. As an IS auditor, you will most likely see a combination of access-control and administration methods. It is important to understand what type of access methods and administration are being used within the organization, to determine whether they are providing the necessary control over information resources. In gaining an understanding of the methods used, you will be able to determine the access paths to computerized information. An access path is the logical route an end user or system takes to get to the information resource. A normal access path can include several software and hardware components, which might implement access controls differently. Per ISACA, the IS auditor should evaluate each component for proper implementation and proper physical and logical security. Logical access controls should also be reviewed to ensure that access is granted on a least-privilege basis per the organization's data owners. Techniques for Identification and AuthenticationIn gaining access to information resources, the system must know who you are (identification) and verify that you are who you say you are (authentication). As a user gaining access, you provide a claimed identity (credentials), and the system authenticates those credentials before you have authorization to utilize the requested object. The most common form of identification is a login ID, in conjunction with a password (authentication), which is used to validate your (subject's) identity. When you provide your credentials (login ID and password), the system can check you (subject) against the system or network you are trying to access (object) and verify that you are allowed access (authorization). The IT organization also should have a method of logging user actions while accessing objects within the information system, to establish accountability (linking individuals to their activities).
Access control involves these components:
The most common form of authentication includes the use of passwords, but authentication can take three forms:
These forms of authentication can be used together. If two or more are used together, this is known as strong authentication or two-factor authentication. Two-factor authentication is commonly used with ATMs. To access your account at an ATM, you need two of three forms of authentication. When you walk up to the ATM, you enter your ATM card (something you have); the ATM prompts you for your PIN (something you know). In this instance, you have used two-factor authentication to access your bank account.
Two-factor authentication requires authentication by two of the following three methods: something the user knows, something the user possesses, or something the user is. A smart card requiring the user's PIN is an example of two-factor authentication. As stated earlier, passwords are the most common form of authentication. Coincidentally, they are also the weakest. Passwords should be implemented in such a way that they are easily remembered but hard to guess. If passwords are initially allocated by an administrator or owner, they should be randomly generated and assigned on an individual basis. If user account and password information is shared between users, all individual accountability for any actions performed under the authority of a shared username has been lost. This is especially critical in a transaction-based environment, such as within financial institutions. In addition to using randomly generated passwords, administrators should implement alert thresholds within systems to detect and act upon failed login events. The implementation of alert thresholds ensures that if a password is entered incorrectly a predefined number of times, the login ID associated with the password automatically is disabled, either for a specific period of time or permanently. As an IS auditor, you will typically see such a threshold set to 3 (incorrect password attempts); the account will be disabled for a specific period of time (such as 30 minutes) or permanently, in which case the user must contact the security administrator to reactivate the account. Terminating access after three unsuccessful logon attempts is a common best practice for preventing unauthorized dial-up access. In generating user accounts and passwords, the administrator should have policies regarding password length, how often passwords are required to be changed, and the password lockout policies. As an example, administrators might create user accounts that automatically expire on a predetermined date. This is an effective control for granting temporary access to vendors and external support personnel. Administrators also should ensure that all passwords created are known only to the user. Users should have the authorization to create and change their own passwords. As a common form of authentication, passwords can be subject to attacks (either internal or external). A common form of password attacks is the dictionary attack, in which an individual uses a dictionary of common words and a program to guess passwords. The dictionaries and programs are widely available on the Internet and are easy to use. The program employed for attack uses each of the words from the dictionary in sequence to guess the password of the logon ID being attacked. Security administrators can mitigate the risk associated with dictionary attacks by enforcing password complexity in the creation of passwords, and also can enforce failed logon attempt password-lockout policies, password length, and periodic password changes. When enforcing password complexity, administrators should extend the required length of passwords (six or more characters) and require the use of numeric characters, upper and lower case, and special characters. Different types of passwords exist, depending on the implementation. In some systems, the passwords are user created; others use cognitive passwords. A cognitive password uses de facto or opinion-based information to verify an individual's identity. Cognitive passwords are commonly used today as security questions associated with an account, in case the user has forgotten the password. During the creation of the user account, a system that uses cognitive passwords might ask one or more security questions: What is your mother's maiden name? What is the name of your favorite pet? What is the elementary school you attended? The user chooses a question and provides the answer, which is stored in the system. If the user forgets the password, the system asks the security question. If it is answered correctly, the system resets the password or sends the existing password via email. Another type of password is a one-time, or dynamic, password. One-time passwords provide maximum security because a new password is required for each login. Conversely, a static password is the same for each login. One-time passwords are usually used in conjunction with a token device, which is essentially a password generator. The token can be either synchronous or asynchronous. When using a synchronous token, the generation of the password can be timed (the password changes every n seconds or minutes) or event driven (the password is generated on demand with a button). The use of token-based authentication generally incorporates something you know (password) combined with something you have (token) to authenticate. A token device that uses asynchronous authentication uses a challenge-response mechanism to authenticate. In this scenario, the system displays a challenge to the user, which the user then enters into the token device. The token device returns a different value. This value then is entered into the system as the response to be authenticated. Passwords are used to authenticate users to provide access and authorization. They are the mechanism that allows subjects to access objects within the system. To provide authorization to objects, those objects need to have defined owners that classify the objects or data. Establishing data ownership is an important first step for properly implementing data classification. The data owners are ultimately responsible and accountable for access control of data. Data owners should require written authorization for users to gain access to objects or data. Security administrators should work with the data owners to identify and implement access rules stipulating which users or group of users are authorized to access data or files, along with the level of authorized access (read or update). Information systems security policies are used as the framework for developing logical access controls. Information systems security policy should be developed and approved by the top management and then should be implemented utilizing access-control lists, password management, and systems configuration files. In addition, data owners might use file encryption to protect confidential data residing on a PC. As stated earlier, authorization of access to objects or data is based on least privilege (need to know) and should incorporate proper segregation of duties. As an example, if a programmer has update access to a live system, IS auditors are more concerned with the programmer's capability to initiate or modify transactions and the capability to access production than the programmer's capability to authorize transactions.
In a database, system integrity is most often ensured through table link verification and reference checks. |