About Hostnames
Connecting to another machine over a network requires that you have some way of identifying the remote machine.
All of the tools covered in this chapter use the TCP/IP (Transmission Control Protocol/Internet Protocol) suite of protocols to communicate across networks, and thus we refer to them generally as Internet tools .
When you use the Internet, there are two ways to identify another machine. One is to use an IP (Internet Protocol) address, and the other is to use a hostname . Data sent over the Internet always uses IP addresses, but IP addresses are hard for humans to remember. This is where hostnames and domain names come in.
An IP address looks like this: 192.168.23.45. Every computer's numbers are different, but IP addresses always have four parts separated by dots (but see the sidebar "The Next Version of IP Addresses"). Each part is a value between 0 and 255. In fact, each part is actually an 8-bit binary number, from 00000000 (0 in base 10) to 11111111 (255 in base 10). Every machine on the Internet must have at least one unique IP addressit's like its telephone number. You can always use an IP address to connect to another machine over the Internet, but usually you will want to use a more user -friendly text-based domain name .
The familiar format of www.something.com is called a fully qualified domain name (FQDN). Your computer translates FQDNs into IP addresses through a process of asking other computers on the Internet for the translation, sort of like using directory assistance for telephone numbers. The most common system for doing this translation is the Domain Name System (DNS), but there are others. You can find a bit more about DNS in "Setting Your Machine's Hostname" in Chapter 14, "Installing and Configuring Servers." FQDNs consist of a top-level domain (.com, .edu, .int, .us, and so on) on the right-hand end, and then any number of sub-domains on the left, with the leftmost item being the name of one specific computer inside the preceding sub-domain. So in this example,
us.rd.yahoo.com
.com is the top-level domain, yahoo is a sub-domain (a sub-domain of .com), rd is also a sub-domain (of yahoo.com), and us is a hostname. The whole thing, us.rd.yahoo.com , is a fully qualified domain name and can be translated by your computer into an IP address. Because "fully qualified domain name" or even "FQDN" is such a mouthful, it is common practice to say "domain name" or "hostname" when what is really meant is "fully qualified domain name." Technically, domain names and the hostname are just parts of an FQDN, but people are sloppy , what can we say?
The Next Version of IP AddressesThe IP addresses described in this book meet a standard called Internet Protocol version 4, or IPv4. The next version of the standard for IP addresses is Internet Protocol Version 6, or IPv6, which allows for much longer addresses. (IPv4 addresses are 32 bits long. IPv6 addresses are four times that size128 bits long.) See the IPv6 Information Page (www.ipv6.org) for more information. Mac OS X has built-in support for IPv6. |
Authenticity of Hosts and SSHWhen you use SSH to connect to another machine, the SSH software on your end (the "client" software) and the sshd daemon on the other end (the "server") exchange information about each other. One of the things the client asks for is the "identity" of the remote host. If you already have the remote machine's encrypted identity stored in your ~/.ssh/known_hosts or ~/.ssh/known_hosts2 file (depending on which version of the SSH protocol the client and server have agreed to use), the client trusts the server's identity; otherwise , you get the prompt shown in Figure 10.1. If you say "yes" to the prompt, then the client adds the encrypted identity supplied by the server to your ~/.ssh/known_hosts or known_hosts2 file. Figure 10.1. Diagram showing the use of ssh to connect to a remote machine.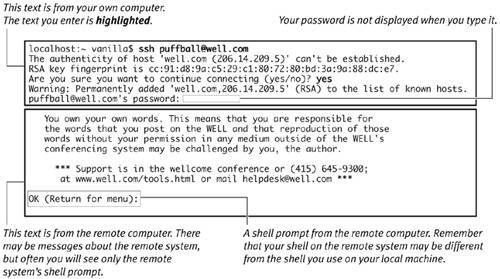 The most secure way of establishing the identity of the remote host is to obtain the remote host's identity file from that machine and manually add it to your ~/.ssh/known_hosts or known_hosts2 file. One way of doing this is to have the remote machine's administrator e-mail the file to you. Because there are variations in how different versions of the SSH software work, you need to get help from the remote machine's administrator to make sure you add the host-identity information in the proper format. In practice this is rarely done, and people simply answer "yes" to the prompt shown in Figure 10.1 the first time they connect to a machine using SSH. |
EAN: 2147483647
Pages: 161