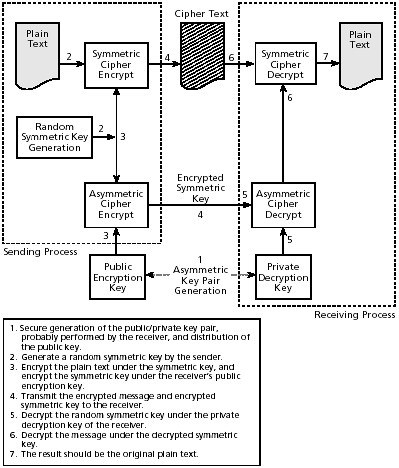
2.8 Enveloped Encryption
| Modern public key encryption systems that encrypt arbitrary-size messages use a combination of secret key and public key ciphers. Stated more precisely, they generate a random symmetric key to encrypt each message and then encrypt that key with a public encryption key of the intended recipient. The symmetrically encrypted message is then sent along with the asymmetrically encrypted random key. See Figure 2-9. Figure 2-9. Enveloped encryption
This type of encryption takes advantage of the more efficient symmetric cipher, avoiding the problem of the slowness of public key systems for large messages, while still gaining the more convenient key distribution model of public key cryptography. Of course, you must still ensure that you are really using the public key of the intended recipient of the encrypted messages, an issue that is commonly addressed through certificates. If a message is sent confidentially to more than one recipient, the sender can transmit separate enveloped encryptions to each one. More commonly, senders create one enveloped encryption employing only one cipher text and symmetric key. That symmetric key then appears several times encrypted under a public encryption key of each intended recipient. These public keys need not be the same size or even use the same public key algorithm. Intended recipients use their own private keys to decrypt the appropriate public key encrypted copy of the symmetric key. They can then use the symmetric key to decrypt the confidential information. Enveloped encryption does not authenticate the message's originator. If that service is desired, it is usually combined with a digital signature (Section 2.6). Such a digital signature can appear either inside or outside the encryption (or you can use two signatures, one in each place). "Outside the encryption" means that the signature appears over the entire enveloped encryption structure and the signature takes the form of plain text. As a consequence, the recipient can first test the signature before decrypting the message. Depending on the exact presentation of the keying information for the signature, this process can also reveal the identity of the originator. Furthermore, the signature will not be useful without the cipher text. The recipient cannot demonstrate the validity of the signature in connection with the plain text to a third party without giving the cipher text and revealing the recipient's private decryption key, which may compromise many other messages. Placing the signature "inside the encryption," so the plain text of the confidential information together with the signature is encrypted, is generally preferable. This strategy assures that the signature is not visible in the cipher text and so cannot reveal the originator's identity. Furthermore, the signature is valid after decryption and so can be demonstrated to a third party without compromise of any recipient private decryption key. For further discussion of these issues, see Chapter 16. |
EAN: 2147483647
Pages: 186