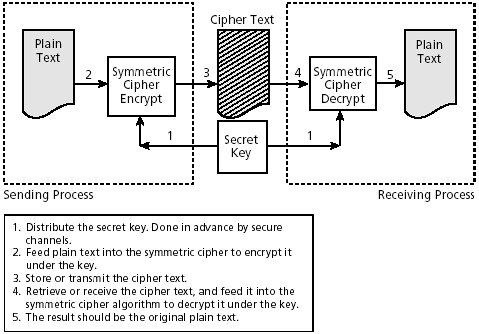
2.3 Secret or Symmetric Key Ciphers
| Secret key ciphers have been known for centuries, although the oldest were weak and had no key. Today's modern ciphers involve a reversible data scrambling system such that it is computationally infeasible to recover the unscrambled data without knowledge of the secret key used to scramble that data. See Figure 2-3. The original version is called the plain text; the scrambled version is called the cipher text. Figure 2-3. Secret key encryption
Perhaps the best-known symmetric cipher is the Data Encryption Standard (DES [FIPS 186-2]). With 56 bits of actual key and a number of weaknesses, DES is not considered strong by current standards. In addition, it was designed for hardware efficiency, not software efficiency. Triple DES is a popular stronger symmetric cipher consisting of three applications of DES with different keys. Of course, it is also three times slower than DES. Recently, NIST (see Appendix D) ran an extensive public process to select a successor to DES. They eventually chose the submission called Rijndael, now known as the Advanced Encryption Standard (AES [FIPS 197]). This encryption method has three variations with different key sizes and strengths. AES is generally believed, even in its weakest variation, to be stronger than Triple DES and faster in software than DES. For an ideal symmetric cipher with an N-bit key, no method should be able to find the plain text with an expected effort significantly less than trying 2N-1 key values. In reality, symmetric ciphers often fall short of this ideal. That is, although they have an N-bit key, due to some systematic weakness, there is some technique to crack the code with less expected effort than trying 2N-1 key values. As long as the weaknesses are known and the cipher remains strong enough, this shortcoming is acceptable. Symmetric ciphers among multiple entities have the same security problems as message authentication codes. It may be logistically impractical to have a separate secret key pair between all pairs of entities and insecure for all of them to share the same secret key. "Enveloped encryption," as discussed in Section 2.8, may represent a superior alternative. If the system includes a centralized trusted server, it is also possible to use a secret key distribution system such as [Kerberos]. Kerberos is not covered in this book. In real systems, further complexities arise. Many symmetric ciphers are "block ciphers" that work on blocks of data significantly larger than an eight-bit byte or octet. Thus they commonly require a "padding" method to match the data to an exact multiple of the block size before encryption and a corresponding unpadding after decryption. In addition, algorithms can be used in a variety of "modes," such as "electronic codebook mode," "cipher feedback chaining mode," and "output feedback chaining mode." See [Schneier], [FIPS 46-3, FIPS 81], or similar references for information on these topics. For the particular block cipher algorithms described in Chapter 18, the chaining and padding methods are described or referenced there. |
EAN: 2147483647
Pages: 186