11.1. The Internet Protocol IP is the dominant network standard in use today because its namesake, the Internet, was successful in connecting the world's various networks together. IP is built on a set of assumptions that break the problem of networking into a set of layers, as shown in Figure 11-1. Each layer acts independently of the ones above and below it, allowing flexibility in how each layer is implemented.  | Figure 11-1 is actually a simplified view of the abstract seven-layer networking model that you'll find in many books on IP networking. In practice, however, most people usually simplify things to the four-layer view presented here. |
|
Figure 11-1. A conceptual view of the networking stack 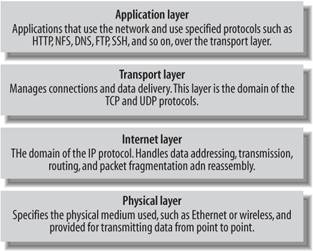
In addition to this layered approach, IP breaks data into separate self-contained pieces, known as packets , which are transmitted individually from their point of origin to their destination. Each packet can, if needed, take a different route from its origin to its destination. This lets information flow even in the face of changing network topologies. The connections between networks can go down or change, but as long as the network can find a new route, the packets eventually find their way through. By using a layered model, and by using packets that flow over virtually any kind of transmission infrastructure, IP runs over a variety of media including wired Ethernet, wireless 802.11, fiber-optic lines, FireWire, and more. It's been joked that IP would work just fine over slips of paper carried by carrier pigeon (you can read the full joke at http://www.ietf.org/rfc/rfc1149.txt). IP is also routable, which means multiple networks can connect to each other and that packets can be routed across those networks to reach their final destination. This is how the Internet was built in the first place: as a collection of networks at universities and government laboratories that had interconnections placed between them. Above IP are two protocols that the applications on your machines use to access the network:
Transmission Control Protocol (TCP) Known as TCP/IP, or TCP over IP, this protocol specifies how packets of data should be transmitted over IP in a reliable fashion. TCP makes sure that all the data transmitted between two machines is presented to an application in the order in which it was transmitted and received. This is very important because IP doesn't guarantee that packets will be transmitted in any particular order; usually they are sent in the order in which they are generated, but because of changing network conditions, they may arrive in any order. TCP also performs error checking. If a packet is corrupted or doesn't arrive, TCP automatically requests retransmission of the data from the sender without intervention of the application. This means application writers don't have to worry about the way in which data is transported across the network. To an application, a network connection can be regarded as a consistent stream of data when in fact that data is being split into several parts and moved across the network in individual units.
User Datagram Protocol (UDP) UDP sends data between computers with a minimum of overhead. Unlike TCP, it doesn't guarantee that the order in which packets arrive is the same as when they were transmitted, and it doesn't request redelivery of bad packets. Because of this, UDP is considered an unreliable protocol, but don't let the negative connotation of the word unreliable fool you. UDP is used extensively where performance needs are paramount and the data errors being transmitted can be worked around or even ignored. For example, UDP is used by many video conferencing applications, such as iChat AV. Because of its low overhead and the fact that if a data frame representing a moment in time isn't received, there is no need to retransmit it as it is no longer valid.
In conjunction with IP, two other important protocols work at the lower layers of the protocol stack:
Internet Control Message Protocol (ICMP) ICMP is used by the network, at the Internet layer, to send messages to itself. For example, the various parts of a network can inform each other that errors have occurred or that a particular network segment is congested with too much traffic. It can also determine whether a particular network address is being used. In addition, ICMP is often used to test the connections between networks.
Address Resolution Protocol (ARP) At the physical layer, an entirely different set of network addresses is used. For example, each Ethernet card has a unique Media Access Control (MAC) address to identify it. ARP is used to map the IP addresses used by the Internet layer of the network stack into the physical addresses used by the equipment on the local network segment.
11.1.1. Network Addressing and Masks Every device, or host, that uses the IP networking stack has an address so that packets can be sent to it. This address has to be unique to the network that the computer is part of. A traditional Internet network address (also known as an IPv4 address) is a sequence of 32 bits (4 bytes), usually written as a series of four dot-separated values in the form #.#.#.#, where each # is a decimal integer between 0 and 255 representing one of the four bytes of the address. For example, 66.93.174.29 is a valid IP address. An IPv4 address is also composed of two parts, albeit indirectly. The first part identifies the local network while the second part identifies the host in that network. Confusingly, the boundary between these two parts in an IPv4 address varies depending on the network. A network mask is used to delineate between the network and host parts of the address. Network masks can come in many forms, but typically, you'll see the following three network masks in use (listed both in dotted notation and in the hexadecimal form that you'll see in some of the command-line utilities):
255.255.255.0 or 0xffffff00 Known as a Class C mask, this indicates that the first three bytes of the address are the network address. There can be 254 hosts on a Class C network. This is the most common mask you'll see in day-to-day use.
255.255.0.0 or 0xffff0000 Known as a Class B mask, this indicates that the first two bytes of the address are the network address. There can be up to 65,000 hosts on a Class B network.
255.0.0.0 or 0xff000000 Known as a Class A mask, this indicates that the first byte of the address is the network address and the remaining bytes identify the host on the network. There can be up to 16.7 million hosts on a Class A network.
Network addresses for hosts connected directly to the Internet must always come from an official source, your Internet Service Provider (ISP). Your ISP owns the rights to use a block of addresses on the Internet and assigns your computer an IP address, or block of IP addresses, as part of your connection to the Internet. 11.1.2. Examining Network Settings There are several ways to see what IP address (or addresses, if you have multiple interfaces active) you are using. The first, but not the most convenient, place most people go to find this information is the Network preference panel (System Preferences  Network), shown in Figure 11-2. When you first open the Network panel, youre given a quick heads-up of the various network settings and the order in which network connections are attempted. In this panel, you'll see one of three colored dots next to the network connections on your system: Network), shown in Figure 11-2. When you first open the Network panel, youre given a quick heads-up of the various network settings and the order in which network connections are attempted. In this panel, you'll see one of three colored dots next to the network connections on your system: Green dots indicate a working network connection Red dots indicate a service that is currently off or not yet configured Yellow dots indicate a service that is set up, but is not able to connect for some reason
For example, if your PowerBook is connected to an AirPort or wireless network, you'll see a green dot next to AirPort in the Network Status view of the Network panel. Likewise, if your PowerBook is attempting to connect to an unknown AirPort network, you'll see a yellow dot next to AirPort. IPv6 Addresses The IPv4 addressing scheme was created at a time when there were relatively few computers running TCP/IP. The original designers didn't imagine that the Internet would expand to the point it has today, where you can easily access it from most of the countries on the planet. Because of this expansion, as well as the anticipation that in the near future there will be an explosion of devices such as mobile phones and home entertainment centers that will access the Internet, a new addressing scheme known as IPv6 is starting to be deployed. IPv6 addresses are 128 bits long and are written as a series of eight colon-separated, 16-bit values written in hexadecimal form, such as the following: fe80:0000:0000:0000:0203:93ff:feef:baa5
Unlike IPv4 addresses, IPv6 addresses don't require a separate network mask. IPv6 isn't in wide use yet, at least in most of the networks that you are likely to find yourself using. But due to the limited number of IPv4 addresses, many networks, especially in Asia where the IPv4 address allocations have already run out, are starting to move to IPv6. In addition, many of the primary Internet backbone service providers are moving their networks to IPv6 in preparation for a full deployment. Mac OS X natively supports IPv6 addresses and, even though you might not be using an IPv6 network for a few more years, you'll see these addresses as you work with the various network tools. |
A better place to look is the Network Utility (/Applications/Utilities) application, as shown in Figure 11-3. Network Utility displays the information about the network interface that is currently being used to connect to the network, also known as the default interface. You can select from the various network interfaces by using the pop-up menu. The information you'll see in the Network Utility's display consists of the following:
Hardware Address Displays the physical MAC address of the interface. This is the address used at the physical layer to move data to and from the network.
IP Address Displays the IP address of the interface.
Link Speed and Link Status Provides the speed of the connection as well as whether it is active.
Vendor and Model Version Provides the maker of the physical interface as well as any version information in the firmware of the interface. Figure 11-2. Network preference panel's Network Status display 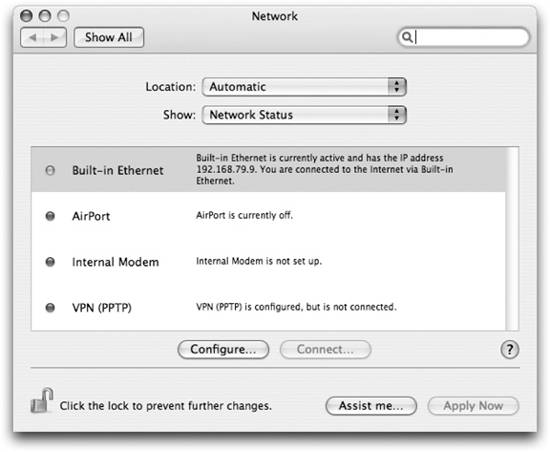
Transfer Statistics Provides some information on how the interface is performing. Typically as you use the network, you'll see the sent and received packets counters increasing. You shouldn't see any errors or collisions unless something is wrong with your network.
On the menu, you'll notice designators like (en0), (en1), or (fw0). The operating system uses these internal identifiers to track the various interfaces. The identifiers you might see are:
lo0 This is the loopback interface , which allows network-aware programs to communicate with other programs on the system without sending packets onto the network. This interface always has the IPv4 (inet) address of 127.0.0.1 and the IPv6 (inet6) address of ::1.
en0 The primary Ethernet interface of your machine. This is always the built-in Ethernet controller for your Mac. Figure 11-3. Network Utility showing information on an active network interface 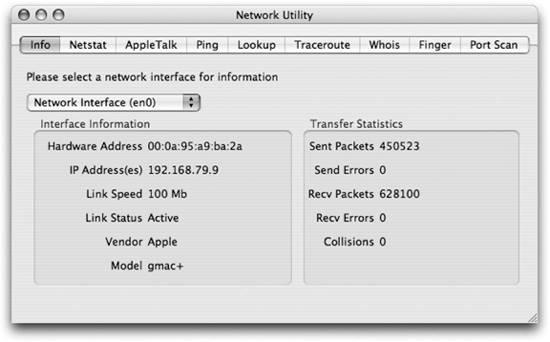
en1 An Ethernet interface. Typically en1 is an AirPort card in your computer (if you have one) or a second Ethernet card. In addition to the IPv6 (inet6) and IPv4 (inet) addresses, the MAC address is given using the ether parameter.
fw0 The FireWire interface for your machine. This interface is disabled until you manually turn on FireWire as a networking option in the Network preference panel.
gif0 This is the generic interface tunnel , used to tunnel network packets from one machine to another, most often to connect two IPv6 networks over a link that uses the IPv4 protocol or to connect two IPv4 networks over a link that uses the IPv6 protocol. By default, this interface is not active. See man gif for more information.
stf0 The 6to4 tunnel interface allows IPv6 hosts on one network communicate transparently with IPv6 hosts on another network over an IPv4 link. By default, this interface is not enabled and is used only when a machine is used as a router between an IPv6 and an IPv4 network. See man stf for more information.
To get more detailed information about the current state of all the network adapters connected to your Mac, use the ifconfig command-line tool, as shown in Example 11-1. Example 11-1. Using ifconfig to look at network connection status $ ifconfig lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> mtu 16384 inet 127.0.0.1 netmask 0xff000000 inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x1 gif0: flags=8010<POINTOPOINT,MULTICAST> mtu 1280 stf0: flags=0<> mtu 1280 en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500 inet 192.168.79.9 netmask 0xffffff00 broadcast 192.168.79.255 ether 00:0a:95:a9:ba:2a media: autoselect (100baseTX <full-duplex>) status: active supported media: none autoselect 10baseT/UTP <half-duplex> 10baseT/UTP <full-duplex> 10baseT/UTP <full-duplex,hw-loopback> 100baseTX <half-duplex> 100baseTX <full-duplex> 100baseTX <full-duplex,hw-loopback> en1: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500 ether 00:0d:93:7f:42:48 media: autoselect (<unknown type>) status: inactive supported media: autoselect fw0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 2030 lladdr 00:0a:95:ff:fe:a9:ba:2a media: autoselect <full-duplex> status: inactive supported media: autoselect <full-duplex>
The output from ifconfig lists the information for each interface using its identifier. 11.1.2.1. Looking at addresses on the local network The system keeps a table of the MAC addresses of the various computers that are on the local network segment and their IP addresses. To see this table, use the arp -a command, as shown in Example 11-2. Example 11-2. Using arp to display host information for your local network $ arp -a gateway.example.com (192.168.79.1) at 0:0:d1:f0:67:9 on en0 [ethernet] ronin.example.com (192.168.79.5) at 0:3:93:d7:3d:c0 on en0 [ethernet] ? (192.168.79.255) at ff:ff:ff:ff:ff:ff on en0 [ethernet]
There are three lines in arp's output in Example 11-2. The first two are hosts, showing the name of the network, the network's IP and MAC addresses, and the port on which the hosts are connected (en0, or Ethernet). The third item in arp -a's output is special because the IP address ends with 255. This means that this is the broadcast address and is primarily used to send packets to all the hosts on a network. Since it is a network address and isn't associated with a host, there isn't a MAC address that corresponds to it (as indicated by ff:ff:ff:ff:ff:ff). |


 Network), shown in Figure 11-2. When you first open the Network panel, youre given a quick heads-up of the various network settings and the order in which network connections are attempted. In this panel, you'll see one of three colored dots next to the network connections on your system:
Network), shown in Figure 11-2. When you first open the Network panel, youre given a quick heads-up of the various network settings and the order in which network connections are attempted. In this panel, you'll see one of three colored dots next to the network connections on your system:
