ARP
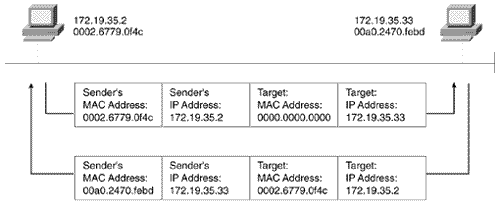
| Chapter 1 explained that routers pass packets across a logical path , composed of multiple data links, by reading and acting on the network addresses in the packets. The packets are passed across the individual data links by encapsulating the packets in frames, which use data link identifiers (MAC addresses, for example) to get the frame from source to destination on the link. One of the major topics of this book concerns the mechanisms by which routers discover and share information about network addresses so that routing may take place. Similarly, devices on a data link need a way to discover their neighbors' data link identifiers so that frames may be transmitted to the correct destination. Several mechanisms can provide this information; [9] IP uses the Address Resolution Protocol (ARP), described in RFC 826. Figure 2.20 shows how ARP works. A device needing to discover the data link identifier of another device will create an ARP Request packet. This request will contain the IP address of the device in question (the target) and the source IP address and data link identifier (MAC address) of the device making the request (the sender). The ARP Request packet is then encapsulated in a frame with the sender's MAC address as the source and a broadcast address for the destination (Figure 2.21). [10]
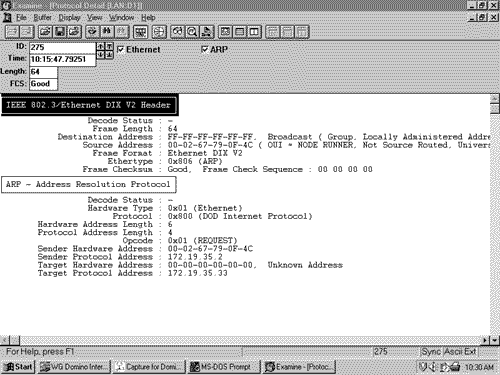
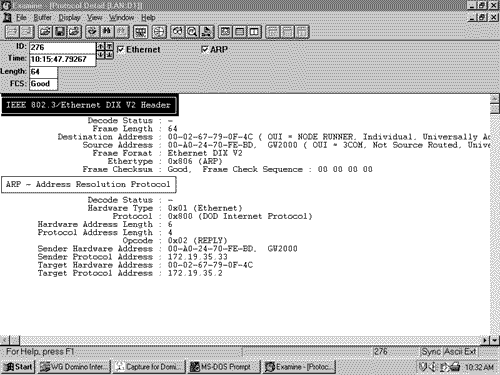
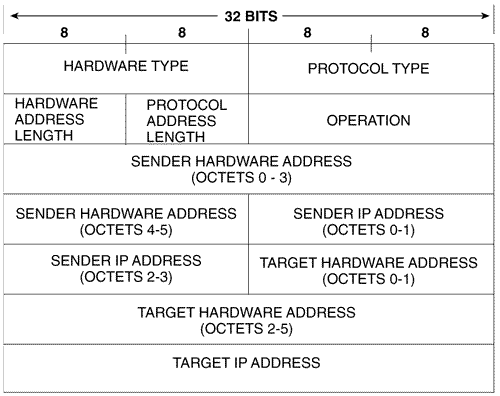
Figure 2.20. ARP is used to map a device's data link identifier to its IP address. Figure 2.21. An analyzer capture of the ARP Request depicted in Figure 2.20, with its encapsulating frame. The broadcast address means that all devices on the data link will receive the frame and examine the encapsulated packet. All devices except the target will recognize that the packet is not for them and will drop the packet. The target will send an ARP Reply to the source address, supplying its MAC address (Figure 2.22) Figure 2.22. An analyzer capture of the ARP Reply depicted in Figure 2.20. Cisco routers will display ARP activity when the debug function debug arp is invoked, as shown in Figure 2.23. Figure 2.23. Router Aretha (172.21.5.1) responds to an ARP request from host 172.19.35.2. Figure 2.24 shows the ARP packet format. As the fields are described, compare them with the ARP packets in Figures 2.21 and 2.22. Figure 2.24. The ARP packet format. Hardware Type specifies the type of hardware, as described in RFC 1700. [11] Examples of some of the more common type numbers are shown in Table 2.4.
Table 2.4. Common hardware type codes.
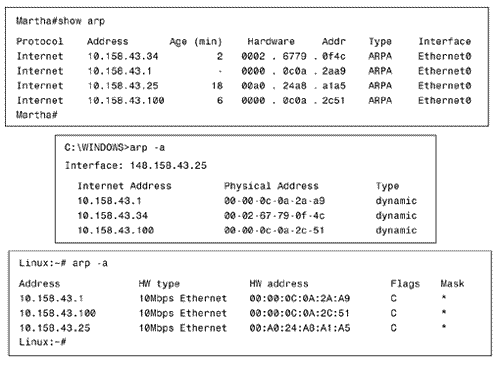
Protocol Type specifies the type of network-level protocol the sender is mapping to the data link identifier; IP is 0x0800. Hardware Address Length specifies the length, in octets, of the data link identifiers. MAC addresses would be 6. Protocol Address Length specifies the length, in octets, of the network-level address. IP would be 4. Operation specifies whether the packet is an ARP Request (1) or an ARP Reply (2). Other values may also be found here, indicating other uses for the ARP packet. Examples are Reverse ARP Request (4), Reverse ARP Reply (5), Inverse ARP Request (8), and Inverse ARP Reply (9). The final 20 octets are the fields for the sender's and target's data link identifiers and IP addresses. In the top screen in Figure 2.25, the command show arp is used to examine the ARP table in a Cisco router. Notice the Age column. As this column would indicate , ARP information is removed from the table after a certain time to prevent the table from becoming congested with old information. Cisco routers hold ARP entries for four hours (14,400 seconds); this default can be changed. The following example changes the ARP timeout to 30 minutes (1,800 seconds): Figure 2.25. The ARP table for three devices connected to the same network: a Cisco router, a Windows 95 host, and a Linux host.
The middle screen of Figure 2.25 shows the ARP table of a Windows 95 PC, and the bottom shows the ARP table from a Linux machine. Although the format is different from the Cisco display, the essential information is the same in all three tables. ARP entries may also be permanently placed in the table. To statically map 172.21.5.131 to hardware address 0000.00a4.b74c, with a SNAP encapsulation type, use the following:
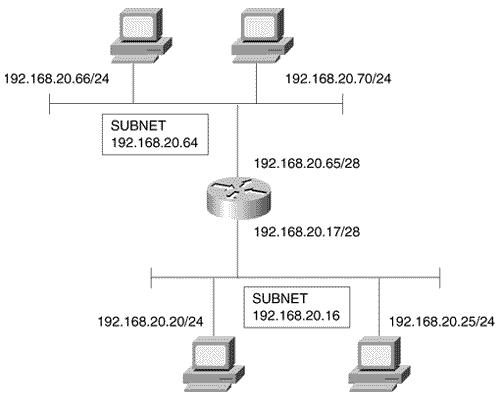
The command clear arp-cache forces a deletion of all dynamic entries from the ARP table. It also clears the fast-switching cache and the IP route cache. Several variations of ARP exist; at least one, proxy ARP, is important to routing. Proxy ARPSometimes called promiscuous ARP and described in RFCs 925 and 1027, proxy ARP is a method by which routers may make themselves available to hosts . For example, a host 192.168.12.5/24 needs to send a packet to 192.168.20.101/24, but it is not configured with default gateway information and therefore does not know how to reach a router. It may issue an ARP Request for 192.168.20.101; the local router, receiving the request and knowing how to reach network 192.168.20.0, will issue an ARP Reply with its own data link identifier in the hardware address field. In effect, the router has tricked the local host into thinking that the router's interface is the interface of 192.168.20.101. All packets destined for that address will be sent to the router. Figure 2.26 shows another use for proxy ARP. Of particular interest here are the address masks. The router is configured with a 28-bit mask (four bits of subnetting for the class C address), but the hosts are all configured with 24-bit, default class C mask. As a result, the hosts will not be aware that subnets exist. Host 192.168.20.66, wanting to send a packet to 192.168.20.25, will issue an ARP Request. The router, recognizing that the target address is on another subnet, will respond with its own hardware address. Proxy ARP makes the subnetted network topology transparent to the hosts. Figure 2.26. Proxy ARP enables the use of transparent subnets. The ARP cache in Figure 2.27 gives a hint that proxy ARP is in use. Notice that multiple IP addresses are mapped to a single MAC identifier; the addresses are for hosts, but the hardware MAC identifier belongs to the router interface. Figure 2.27. This ARP table from host 192.168.20.66 in Figure 2.26 shows multiple IP addresses mapped to one MAC identifier, indicating that proxy ARP is in use. Proxy ARP is enabled by default on Cisco routers and may be disabled on a per interface basis with the command no ip proxy-arp . Gratuitous ARPA host may occasionally issue an ARP Request with its own IP address as the target address. These ARP Requests, known as gratuitous ARPs, have two uses:
Many IP implementations do not use gratuitous ARP, but you should be aware of its existence. Reverse ARPInstead of mapping a hardwar e address to a known IP address, Reverse ARP (RARP) maps an IP address to a known hardware address. Some devices, such as diskless workstations, may not know their IP address at startup. RARP may be programmed into firmware on these devices, allowing them to issue an ARP Request that has their burned-in hardware address. The reply from a RARP server will supply the appropriate IP address. RARP is being largely supplanted by Bootstrap Protocol (BOOTP) and its extension Dynamic Host Configuration Protocol (DHCP), both of which can provide more information than the IP address, and which, unlike RARP, can be routed off the local data link. |