Extended IP Access Lists
| Extended IP access lists provide far more flexibility in the specification of what is to be filtered. The basic format of the extended IP access list line is access-list access-list-number { deny permit } protocol source source-wildcard destination destination-wildcard [ precedence precedence ][ tos tos][ log ] Some of the features here are familiar, and some are new.
An example of an extended IP access list is:
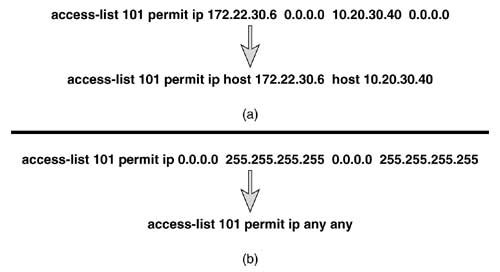
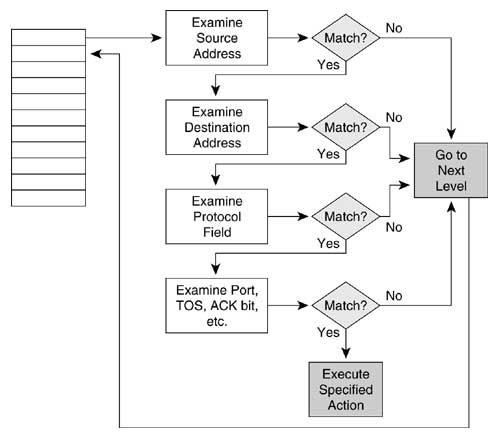
Line 1: IP packets with a source address of 172.22.30.6 and with a destination address that belongs to network 10.0.0.0 are permitted. Line 2: IP packets with a source address of 172.22.30.95 and with a destination address that belongs to subnet 10.11.12.0/24 are permitted. Line 3: IP packets with a source address that belongs to subnet 172.22.30.0/24 and with a destination address of 192.168.18.27 are dropped. Line 4: IP packets with source addresses between 172.22.0.0 and 172.22.31.255 and with a destination address that belongs to network 192.168.18.0 are permitted. Line 5: IP packets with a source address that belongs to network 172.22.0.0 and with a destination address whose first 26 bits are 192.168.18.64 are dropped. Line 6: IP packets from any source to any destination are permitted. Figure B.7 shows two shortcuts that may be used when writing extended IP access lists. Recall that standard IP access lists have a default mask of 0.0.0.0. This default does not apply to extended access lists; there would be no way for the router to interpret it correctly. An alternative exists for extended lists, however. In Figure B.7(a), packets are permitted if their source is host 172.22.30.6 and their destination is host 10.20.30.40. Any time the mask in an extended IP access list is 0.0.0.0, it may be replaced by adding the keyword host before the address. Figure B.7. Two shortcuts may be used when writing extended IP access lists. The example in Figure B.7(b) permits any IP packets from any source to any destination. Just as with standard access lists, the any keyword may be used in place of the 0.0.0.0 255.255.255.255 address/inverse mask combination for the source, the destination, or both. Extended access lists may be more powerful than standard access lists because the former examine more than the packet's source address, but everything has a price. The price you pay with extended lists is increased processing (Figure B.8). Because each line of the access list is examining multiple fields within the packet, multiple CPU interrupts can occur. If the access list is very large or the router is very busy, this requirement may affect performance adversely. Figure B.8. The decision flow of an extended IP access list. Keeping access lists as small as possible reduces the processing burden on the router. Also notice that when a match occurs, the specified action is invoked and processing stops. Therefore, if you can write your lists so that most matches occur in the first few lines, performance will be improved. This approach isn't always feasible , but it is something to keep in mind when designing access lists. As an exercise, try making the access list given as an example at the beginning of this section more elegant. That is, rewrite the list with as few lines as possible without losing any of its functionality. (Hint: A list with the same functionality can be written with only three lines.) TCP Access ListsThe format for an extended access list line that examines a TCP segment is: access-list access-list-number { deny permit } tcp source source-wildcard [ operator port [ port ]] destination destination-wildcard [ operator port [ port ]] [ established ][ precedence precedence ][ tos tos][ log ] Notice that the protocol variable is tcp . Probably the most significant feature here is that the access list can examine the source and destination port numbers in the TCP segment header. As a result, you have the option of filtering packets not only to and from a particular address but also to and from a particular socket (an IP address/application port combination).
An example of a TCP access list line is:
Line 1: Permit TCP packets from any source to network 172.22.0.0 if the connection was established from that network. Line 2: Permit TCP packets from any source if the destination is port 25 (SMTP) of host 172.22.15.83. Line 3: Allow any TCP packet with a source address from network 10.0.0.0 to telnet (port 23) to any address on subnet 172.22.114.0/24. All other packets will be dropped by the implicit deny any . UDP Access ListsThe format for an extended access list line that examines a UDP segment is: access-list access-list-number { deny permit } udp source source-wildcard [ operator port [ port ]] destination destination-wildcard [ operator port [ port ]] [ precedence precedence ][ tos tos][ log ] This format is very similar to the TCP format, except that the protocol variable now is udp . The other difference is that there is no established keyword. The reason is that UDP is a connectionless transport service, and no connections are established between hosts . In the following example, three lines have been added to the previous TCP example:
Line 4: Permit UDP packets from subnet 10.64.32.0/24 to the TFTP port (69) on host 172.22.15.87. Line 5: Permit UDP packets from any source to the Domain Name Server (port 53) on host 172.22.15.85. Line 6: Permit all SNMP packets (port 161) from any source to any destination. The implicit deny any still drops all packets not finding a match in the list. ICMP Access ListsThe format for an extended access list line that examines an ICMP packet is: access-list access-list-number { deny permit } icmp source source-wildcard destination destination-wildcard [ icmp-type [ icmp-code ]][ precedence precedence ][ tos tos][ log ] icmp is now in the protocol field. Notice that there are no source or destination ports here; ICMP is a network layer protocol. This line can be used to filter all ICMP messages, or you can use the following options to filter specific ICMP messages:
An example of an ICMP access list is:
Line 1: Deny ICMP ping responses (Echo Reply, ICMP type 0) from network 172.22.0.0 to any destination. Line 2: Deny ICMP destination unreachable packets (type 3) with a code number of 9 (Network Administratively Prohibited) from network 172.22.0.0 to any destination. Line 3: Deny ICMP destination unreachable packets (type 3) with a code number of 10 (Host Administratively Prohibited) from network 172.22.0.0 to any destination. Line 4: Permit all other IP packets. |