Standard IP Access Lists
| The format of a standard access list line is: access-list access-list-number { deny permit } source [ source-wildcard ] This command specifies the access list number, which according to Table B.1 is between 1 and 99; the action (permit or deny); a source IP address; and the wildcard (or inverse) mask. An example of a standard IP access list is:
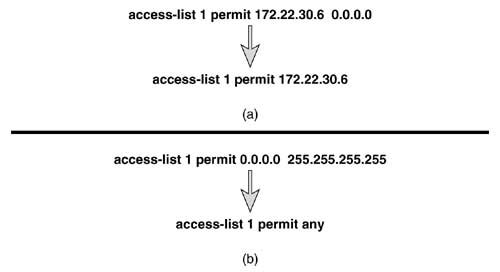
The first two lines of the example permit passage of packets whose source addresses belong to two specific hosts, 172.22.30.6 and 172.22.30.95. This seems pretty obvious from looking at the lines, although the inverse mask of 0.0.0.0 may not make sense yet. The third line denies all other hosts on subnet 172.22.30.0. Again, it's fairly intuitive. The purpose of the fourth line is not so obvious. It permits all hosts with addresses in the range of 172.22.0.1 to 172.22.31.255. The inverse mask is what allows the specification of this range of addresses with a single line. The fifth line denies all other subnets of the Class B network 172.22.0.0, and the last line permits all other addresses. To fully understand this access list, you need to understand inverse masks. Recall how IP address masks function: To derive a network or subnet address from a host address, a one is set in the mask corresponding to each bit of the network address, and a zero is set for each bit of the host address. A Boolean AND is performed on each bit, and the result is the network or subnet number. Figure B.5(a) includes a truth table for the AND function; in English, the function states: Figure B.5. Truth tables and examples of a Boolean AND (a) and a Boolean OR (b). Compare two bits. The result is one if and only if both bits are one. A Boolean OR is the inverse of this function, as its truth table in Figure B.5(b) shows: Compare two bits. The result is zero if and only if both bits are zero. An inverse mask (Cisco prefers the term wildcard mask ) sets a zero for each bit of the address that should be exactly matched and a one for each bit where anything will match ”the one bits are frequently referred to as "don't care" bits. The inverse mask is then ORed with the address. Notice the result of the OR example in Figure B.5(b), 172.22.30.255. In IP terms this result means "all host addresses on subnet 172.22.30.0." Any specific address from 172.22.30.0 will match this address/inverse mask combination. Figure B.6 shows two shortcuts that may be used when writing standard IP access lists. Figure B.6(a) shows an inverse mask of all zeroes to indicate that all 32 bits of the address in question must match 172.22.30.6 exactly. The default mask for a standard IP access list is 0.0.0.0. So the alternative statement shown, with no mask specified, is the same as the first statement. Note that this default does not apply to extended IP access lists, which are covered in the following section. Figure B.6. Two shortcuts may be used when writing standard IP access lists. Figure B.6(b) shows the permit anything address/inverse mask combination. The address of 0.0.0.0 is actually just a placeholder; the mask, 255.255.255.255, actually does all the work. By placing a one in all 32 bit positions , this mask will match anything. The alternative statement shown uses the keyword any , which has the same meaning as the first statement. |