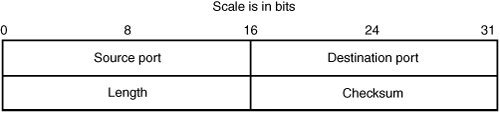
User Datagram Protocol
| User Datagram Protocol (UDP) is a connectionless transport-layer protocol that rests on top of IP. As you can probably tell from the header shown in Figure 14-9, it's intended to be a lightweight protocol. It adds the abstraction of ports, which allows multiple clients and servers to multiplex data using the same client-server IP address pair, and adds optional checksums for UDP data to verify that a packet hasn't been corrupted en route. Beyond that, it provides none of the services that TCP does, such as flow control and reliable delivery. UDP is typically used for protocols that require low latency but can tolerate losses. The most popular use of UDP is for Domain Name System (DNS), which provides name resolution for the Internet. Figure 14-9. UDP header The following list describes the header fields in a UDP packet:
Basic UDP Header ValidationThe UDP header is fairly straightforward, but there's still room for processing code to misstep, as described in the following sections. Is the UDP Length Field Correct?The length field specifies the length of the UDP header and the data in the datagram. You've seen situations in which processing code ignores this field and instead honors lengths coming from the IP header or device driver. If the length field is too large, it could lead to numeric overflow or underflow situations. Likewise, the minimum value for the UDP length field is 8 bytes. If the field is below 8 bytes and it's honored, a numeric underflow situation could occur. A length of 8 bytes means there's no UDP data in the packet. Is the UDP Checksum Correct?The UDP checksum is optional. If it's set to zero, the checksum is not calculated. However, if it's set and the checksum is incorrect, end hosts likely disregard the packet. Any system attempting to interpret UDP packets should be aware of these possible outcomes. UDP IssuesUDP can be spoofed easily, unlike TCP, where establishing a connection with a forged source IP address is much harder. UDP data can also be sent over broadcast and multicast addresses that aren't appropriate for TCP data. The bottom line is that sensitive code shouldn't rely on source IP addresses for purposes of authentication with UDP. Firewalls and packet filters can find UDP particularly troublesome for this reason. |
EAN: 2147483647
Pages: 194