How to Avoid Becoming a Victim
| The first thing a person can do to help himself/herself is be suspicious of any e-mail stating that an account, or any other information, is needed, even (or especially) when it looks legitimate. The bottom line is that if a company you do business with needs to contact you, someone, somewhere will pick up the phone and call you. (If you are suspicious about the call, call them back using the phone number listed on your bill.) This may not be the case 100 percent of the time, but always be suspicious of these types of e-mails. Healthy paranoia is a good thing. As we have stated in our previous books, if you think your credit card company has really lost or forgotten your account number, go shopping. That is exactly what the identity thieves who sent you the e-mail will do if you "verify" the number via the e-mail. At least this way you can get some new stuff. Very Important Some of the scams include a working pay or toll-free number. If you want to call to verify whether an issue exists, do not call the number posted in the e-mail. Use the one in the phone book or on your bill. For those who do not want to just delete every suspicious e-mail, here are some things to look for: Do you actually do business or have an account with the company or institution in question? This one would seem like a no-brainer, but there are many known cases of people getting burned by e-mails that should have been deleted as soon as the name or logo appeared on the screen because they should know it does not concern them, legitimate or otherwise. As far as we can reason, people must just feel a sense of obligation to right a perceived error or respond to something that seems authoritative. Don't do it! The scams rely on people doing what they think is the right thing to do. This is how most social engineering scams work. Figure 7-5 shows an example of an e-mail we received. Neither of us bank with this institution. Figure 7-5. Account Verification E-Mail Phishing Example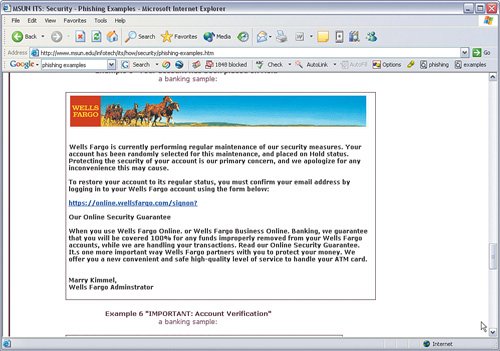 Is the e-mail addressed to a generic title? If the e-mail begins with a greeting such as "Dear account holder" or "Dear business name member" or any other greeting that does not use your full name or login ID, it is probably a phishing attempt. Even if it does use your full name or login ID, it might be a scam; if not, however, it should be dismissed outright. In the examples shown (most of the figures in this chapter have generic titles), if the bank knows that all this activity took place on your account, shouldn't they know your name? Is the e-mail from a strange sender? If the e-mail is from a strange-looking e-mail address (much like spam), ask yourself why your bank does not have a more normal address? If you get an e-mail from MyBank, it is a good bet that the person sending it should have an e-mail address ending in @mybank.com. Does the e-mail sound urgent, threatening to close an account if you do not take action? The faster you act, the less time you have to think. The people who run these scams want you to move fast so that you give them your personal info before you figure out the scam. Figure 7-6 shows an example of the urgency scam. Figure 7-6. Urgent Expiration Scam Example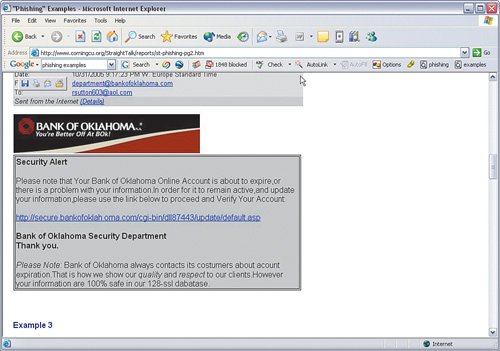 Does the e-mail have misspelled words or poor grammar or sentence structure? Many phishing scams originate overseas or in countries with loose copyright and extradition laws. Although the scammers are talented at creating logos and web pages, they seem to have all skipped language lessons. That is not to say that a perfectly structured e-mail is legitimate. To be sure, however, a poorly written one is a trap. Does the e-mail ask for charitable donations (often in the wake of a disaster)? The American Red Cross and just about every other reputable charity all have policies in place stating that they do not solicit for donations via e-mail. If you get an e-mail asking for donations, assume it is a scam. If an e-mail alerts you to a relief effort that you want to support, delete the e-mail, open a browser, and go to the official site of the charity you want to support. Do not click any links within the e-mail. This is one of the most insidious forms of phishing, preying on good-intending people and diverting funds from those who would have received additional help. Never respond to an e-mail asking for charitable donations. Does the e-mail state that you have won a contest or prize that you did not even enter for? It is fake! The previous example showed how scammers prey on people's charity; this type plays on greed. Unless you have specifically entered a contest, do not reply to this type of e-mail. In fact, even if you did enter a contest, do not reply to the e-mail. Call the phone number on the ticket or entry form. Figure 7-7 shows an example of this scam. Figure 7-7. You Won! Scam Example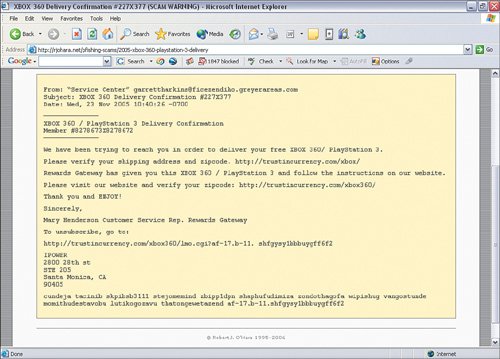 Is the e-mail regarding a transfer of funds from a bank in Nigeria? Delete Delete Delete! (also read Chapter 10, "Tip 10: Use Common Sense"). Is the e-mail regarding a recently deceased, wealthy, long-lost relative and you are the only family member they can find? Forward these to your dumb cousin whom you don't like anyway. Really, this has got to be one of the worst scams ever, and yet somehow people fall for it. The e-mail asks for your account information so that they can transfer your inheritance into it. The only transfer that will happen will not be in your favor. Is the e-mail offering security services through a bank or other type of institution? This is a new version of the confidence schemes. Telemarketers used to do something similar by going back to people they had previously ripped off, offering to track down the stolen money for a fee (thereby ripping them off a second time). In this scheme, people who have been burned, or who are afraid to get burned, are enticed to provide credit card data to pay for bogus services. Figure 7-8 shows an example of this. Figure 7-8. Security Services Scam Example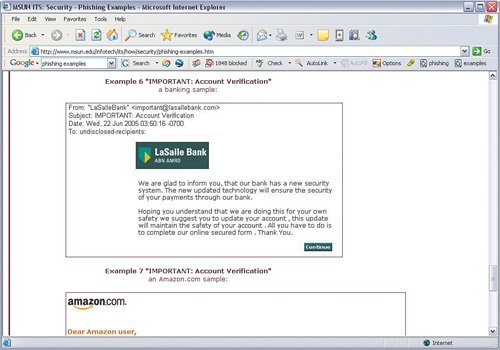 These are just some examples of many types of phishing scams out there. The scammers are getting bolder, smarter, and more clever with each scam. So, be on the look out as they are sure to invent new ones every day that do not follow the common examples in this chapter. Unfortunately, most of the security measures we talk about in this book do not catch or otherwise deter phishing scams (other than spam filters, but those are not 100 percent effective in blocking these types of e-mails). The next section covers what to do if you get an e-mail you suspect as fraudulent. The short answer is if it looks suspicious, delete. You are the best filter. |
EAN: 2147483647
Pages: 130