Chapter 7. Tip 7: Recognize and Avoid Phishing Scams
|
Phishing is a relatively new social engineering scam that has become one of the most popular tactics used by identity thieves. Phishing scams play on people's fear or sense of doing what is right by tricking victims into willingly supplying scammers with personal information, account numbers, passwords, and mothers' maiden names. Some thieves take it a step further with confidence scams that offer "identity security" to their former victims and then hit them again. Very Important For those unfamiliar with the concept of social engineering, Wikipedia.com defines it as the practice of obtaining confidential information by manipulation of legitimate users. A social engineer will commonly use the telephone or Internet to trick people into revealing sensitive information or get them to do something that is against typical policies. By this method, social engineers exploit the natural tendency of a person to trust his or her word, rather than exploiting computer security holes. It is generally agreed upon that users are the weak link in security, and this principle is what makes social engineering possible. 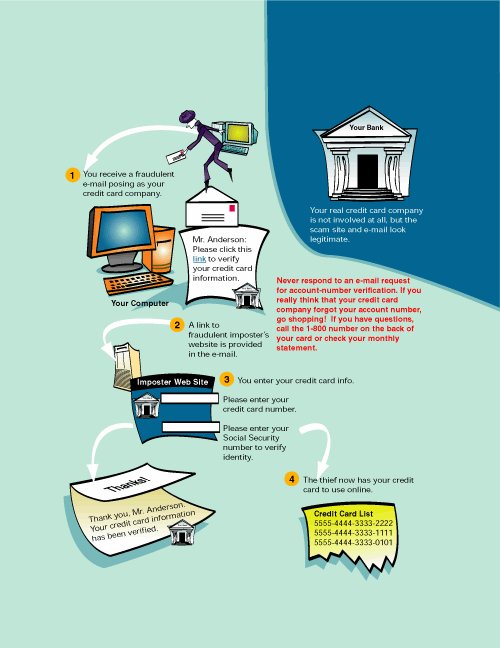 To give you an idea how widespread this problem has become, the following statistics were taken from http://www.mailfrontier.com (with the original source reference included). In 2005
In others words, this is a pretty big problem. If you fall for one of these scams, you could be looking at real financial losses, and potentially years to repair your credit rating. The key realization is that there would not be all this phishing activity going on if people were not falling for it. Figure 7-1 shows a typical sample phishing e-mail (provided by Wikipedia) and demonstrates exactly how legitimate they can appear. Figure 7-1. Phishing Example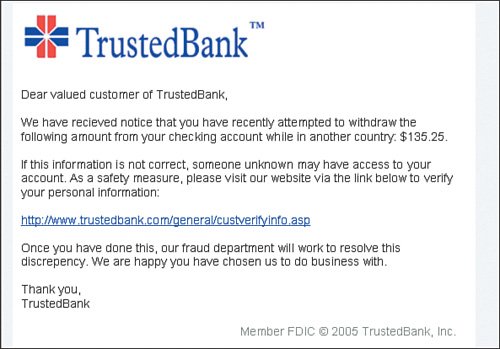 Very Important The term phishing is kind of a funny spelling of the word fishing, referring to fishing you for your identity. The ph instead of f in the spelling gets its origins from the term phreaking, which is a form of hacking into phone lines to get free long distance. There is still some debate on exactly how and when the use of the term got started, but most people assume it is a combination of the words phone and freak. This spelling convention has carried over to computer hackers for hacks such as pharming and phishing. |
EAN: 2147483647
Pages: 130
