Understanding Spam
Spam e-mail messages all start innocently enough, usually with a single message hawking some silly product or service. It doesn't take long, however, for that one message to be quickly followed by another 2, then 4, and then perhaps 10 or more per day. Within a few months, junk e-mail messages can literally overwhelm your inbox, to the point where you don't even want to check your e-mail anymore. To understand (and ultimately fight) spam, it's important to be familiar with the following concepts:
-
How spam finds you
-
Why spam can be a security threat
You learn more about these important concepts in the following sections.
How Spam Finds You
If junk e-mail messages are finding their way into your inbox, it's happening for one of two reasons. The first (and most common) is that someone has managed to obtain your e-mail address. The second is that the spammer has actually guessed your address, adding your name or a popular term to common domain names like @hotmail.com, for example.
Spammers typically acquire your e-mail address by one of the following methods:
-
Harvesting
-
Web site registrations
-
Viruses
The following sections explore each of these techniques in more detail.
HARVESTING
Harvesting is the process by which most e-mail addresses are acquired by spammers. In a nutshell, any time that you post your e-mail address online - be it to a public web site or Usenet newsgroup - it becomes susceptible to programs (known as e-mail address harvesters) designed to traverse the Internet, collecting addresses along the way.
To avoid having your e-mail address harvested and used as a destination for spam, never post your address online. For cases where you do need to post an address for others to contact you, never use your primary address. Instead, set up a secondary account (with a free web mail service, for example) to use as your public e-mail address, and submit this address as required.
Unfortunately, you can expect your secondary address to be a major target for spam, along with legitimate messages. However, that's still better than dealing with large numbers of junk mail messages in the account used to correspond with friends, family, and business associates.
| Caution | Many people recommend alternate techniques of posting your e-mail address online to avoid spam. Common examples include replacing the @ symbol with (at), or including the term nospam within your address and reminding senders to remove this term to send you a message. Although these techniques may fool very primitive harvesting programs, don't expect them to keep you spam-free. Any harvesting program that can recognize an e-mail address can also be programmed to detect and collect addresses that are masked using these techniques. |
WEB SITE REGISTRATIONS
Another popular way for spammers to obtain your e-mail address is by getting you to supply it through a web site registration form of some sort. Although most reputable web sites never resell or give away your e-mail address under any circumstances, there's really nothing stopping other sites from doing with your address as they please. As such, spammers commonly purchase lists of addresses from various sources online, including companies that buy valid lists of addresses from other sites.
As with posting your e-mail address online, avoid submitting your primary e-mail address when completing web-based registration forms. Instead, set up a secondary address for this purpose.
| Note | Not every web site to which you submit your e-mail address is unscrupulous enough to sell your address and other personal information, but many do. Most sites spell out exactly what they do or do not do with your information as part of their terms of service disclaimer, making it well worth at least a quick glance - especially for phrases like third parties. In addition to disclaimers, many sites also include a dedicated privacy policy page that outlines how they use the information you submit, how it is stored, and so on. The World Wide Web Consortium has developed a standard that deals with the use of personal information by web sites. For more information on the standard known as the Platform for Privacy Preferences Project (P3P), visit http://www.w3.org/P3P. |
VIRUSES
Over the past few years, viruses and other pests have become an exceedingly popular way for spammers to obtain e-mail addresses. Although the methodology varies from virus to virus, the general idea is that a virus infects a computer, and then scans that system for e-mail addresses. In most cases, the virus immediately begins searching the users' address books and contact lists, harvests all addresses into a file, and then sends the file on to an Internet server.
Ultimately, this means that your e-mail address can end up in the hands of spammers through no fault of your own. All it takes is for a harvesting virus to infect a computer where your e-mail address is in the user's address book or contact list. Although you obviously can't control what other people do with their own computers, it doesn't hurt to remind friends and family members about the importance of running antivirus software, keeping it up-to-date, and scanning for viruses frequently. Of course, in the same way that a virus on a friend's computer can lead to more spam for you, the reverse is also true - when a harvesting virus infects your PC, it may be people in your address book who end up on the wrong end of the spam town.
Why Spam Can Be a Security Threat
Normally seen as little more than an annoyance, spam messages are becoming more of a threat to security and privacy every day. Where once their objectives were relatively limited to profit motives, the spam messages of today not only try to sell to, but also infect, steal from, and even scam the recipient. Some of the primary security and privacy threats associated with spam include:
-
Viruses
-
Beacons
-
Phishing
-
Scams
Each of these threats is looked at in more detail in the following sections.
VIRUSES
Many viruses are designed to harvest e-mail addresses, but it's also not uncommon for spam e-mail messages to contain virus-laden attachments as well. In some cases, this is the result of a virus infecting one PC and then mailing itself out to all the addresses in the infected computer's contact list. In others, a spammer knowingly sends out an infected e-mail attachment to a list of users, hoping that at least a few users will open the attachment, become infected, and in turn propagate the virus even further.
Your best protection against e-mail–based viruses is to install anti-virus software that includes real-time scanning of all incoming and outgoing e-mail messages. These programs typically quarantine infected attachments automatically, but for them to be truly effective you must be diligent about keeping your virus definition files up-to-date.
BEACONS
The most common problems a spammer faces determining whether the e-mail addresses on his lists are valid. In the eyes of the spammer, a known good e-mail address is much more valuable than addresses where the validity of the address is suspect. Spammers rely on their messages reaching a functioning and in-use mailbox, and they take steps to confirm whether a given address is in use.
One of the most popular methods that spammers use to confirm an address is through beacons. In the world of e-mail, a beacon signals that your address is good, and that the spammer's message was at least opened. Although different beaconing methods exist, the most popular is to send e-mail messages in HTML format (messages with different fonts, colors, images, and so forth). When these messages are opened, a request is sent from your computer to download any images the message includes from a web server. The web server then tracks that the request came from the message sent to you, through a unique code in the specific message you received. Ultimately, the beacon tells the spammer not only that your address is valid, but also that you read (or briefly opened) the message.
| Caution | If a spam e-mail message that you receive includes a link that you can click to remove yourself from the spammers list, never click it. Although a small percentage of spammers might actually remove you from their list, the vast majority simply use your click as yet another type of beacon signaling that your e-mail address is valid. In most cases, clicking these links and submitting your e-mail address for removal actually results in you receiving even more spam. |
Windows Mail automatically prevents beacons from functioning by not allowing any requests to web sources to be processed when you open an e-mail message. Figure 11-1 provides an example of how a message that includes beacons may appear when opened with Windows Mail.
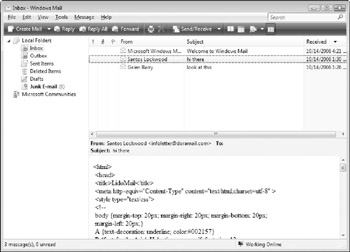
Figure 11-1: Windows Mail automatically protects against message beacons and code embedded in HTML-based e-mail messages.
If you're using an e-mail client program other than Windows Mail, it may or may not include a specific feature for dealing with beacons. However, almost every e-mail client program includes an option to view all messages as plain text, which eliminates the possibility of the message attempting to contact the Internet. To determine how to view all e-mail messages you receive as plain text in your e-mail client, consult the program's Help system. You learn more about configuring Windows Mail to open messages as plain text later in this chapter.
| Caution | Although opening a spam e-mail message can signal that your e-mail address is valid, spammers also rely on another technique in their quest to find valid addresses - the seemingly harmless out-of-office reply. Also referred to as an autoresponder, this is the message that you typically configure when you're away from e-mail for a few days. When enabled, every e-mail message that you receive from another user results in an automatic reply being sent back to the sender. Although legitimate senders usually appreciate out-of-office replies (because they'll know you're away and not ignoring them), they're also a boon to spammers who use the replies to determine that your address is valid. If you plan to use out-of-office replies, create a rule that only sends these messages to people already in your address book or contact list. You learn more about creating e-mail message rules later in this chapter. |
PHISHING
The spelling may be different, but persons engaging in phishing are definitely looking to hook something - usually sensitive personal information like username and password information for online banking or auction web sites.
In its most common form, phishing involves a spammer sending you an e-mail message that looks as if it was sent from a bank or payment service or a popular online auction web site. The message usually states that the web site needs you to log on to confirm your username and password, and provides you with a link to submit your information. When you click the link (which may appear 100 percent legitimate), your web browser opens and displays a page that may look identical to the site suggested in the message. In reality, the site is a fake. If you submit your information, it's actually sent to the spammer/scammer who originally sent the message, giving him full and unrestricted access to your account. It's not uncommon for phishing victims to find that funds have been transferred from their accounts, or that high-priced auctions have been set up under their username. In the case of the auction, the scammer sets up the auction using your username, sells the item to the highest bidder, and then collects the winner's money. When the scam is complete, the scammer and the money are long gone, and you're left on the hook to deal with the aftermath.
Ultimately, the best way to ensure that you're never a phishing victim is to ignore and delete any e-mail messages stating that you need to supply information about your account. If you do receive such a message and believe it to be legitimate, contact the company who sent the message by phone, or by visiting its web site directly. Most legitimate companies (and especially those involved in financial transactions) never ask for your personal account details in an e-mail message. If you believe that you have been tricked into supplying your username and password as a result of a phishing scam, contact the company in question, or log on to your account and change your password immediately.
With the release of Windows Vista and IE7, Windows Mail (formerly Outlook Express) now includes built-in anti-phishing technology to help warn you against detected phishing attempts.
| Note | For more details on phishing and phishing-related scams, visit http://www.antiphishing.org. |
SCAMS
Although they've received a fair amount of press coverage over the past few years, many e-mail users continue to fall for a variety of scam messages received by e-mail. The most popular of these are the so-called 419 messages, named after a related section of the Nigerian criminal code (the country where the scam is purported to have originated). These particular messages ask you to help someone transfer money out of the sender's country for a portion of the proceeds, but a number of related scams exist - for example, some inform you that you've won the lottery or a certain prize. In all cases, you must pay a transfer fee or supply your banking details to claim your bounty, which is effectively the scam. As unbelievable as it sounds, some individuals are duped out of tens of thousands of dollars (and more) after falling for this trickery.
Although you might be tempted to reply to the sender of these messages, don't. If you do want to take action, visit the Spam Reporting Addresses web site at http://www.banspam.javawoman.com/report3/scam1.html for details on contacting the appropriate authorities in your locale.
| Note | For some good reading on 419 and related Internet scams, visit the 419 Coalition web site at http://www.home.rica.net/alphae/419coal/index.htm. |
EAN: 2147483647
Pages: 135