Chapter 10: Fighting Malware-Protecting Against Spyware, Adware, and Browser Hijackers
Imagine a world where your every move was being watched-your comings and goings tracked, your telephone calls recorded, and all messages sent or received monitored by some nameless and faceless person or corporation. Sounds a little scary, doesn't it? The worst part is that this world already exists, and it's probably sitting right on your desk.
Malware-often referred to as spyware-is the latest in a breed of almost virus-like pests that have taken to infecting computers at an alarming rate. Unlike viruses, however, these new strains of infection are less concerned with spreading and more interested in keeping tabs on you. From tracking your online wanderings to collecting details of every key you press, there's literally an army of malware threats quietly infiltrating computers and stripping away the privacy of Windows users worldwide. Unfortunately, most people still have no idea what malware threats are, the dangers they pose, or the fact that their computer is (more than likely) already infected.
Thankfully, all is not lost. Although malware represents one of the largest and most wide-scale threats to PC security and personal privacy that the world has ever known, you can nurse even a badly infected Windows Vista system back to a clean bill of health with the right knowledge and tools. In this chapter you learn about what malware is, the different types of threats that exist, the real dangers that these threats pose, and finally the tools and techniques you can use to clean up your system and keep it protected from future threats.
Understanding Malware
Back in the good ol' days, viruses represented the most clear and present danger to a computer's security. As long as you were geared up with antivirus software and the latest virus definition files, you could consider your PC to be adequately protected. Unfortunately, times have changed and a whole new breed of pests is now infecting computers at an alarming rate. The last few years have seen the rise of an entirely new set of threats broadly known as malware, and it's been estimated that as many as 8 out of every 10 Windows computers are already infected by malware in one form or other.
Strictly speaking, malware and viruses are different beasts. Malware isn't nearly as concerned with propagating itself from computer to computer in the manner of a virus or worm, so much as it's interested in infecting your computer to spy on you. It often tracks your web surfing habits or logs all of your PC activities silently in the background. Other forms of malware are designed to mine your computer for useful bits of information, or hijack your web browser's configuration so that your home page and search settings are no longer under your control. Still others install dialers that use your modem to call exotic locales, resulting in hundreds to thousands of dollars of long-distance charges to your monthly phone bill. Although originally seen as little more than an annoyance, malware is arguably the most prevalent and under-recognized threat in the PC world today.
Types of Malware
In much the same way that the term virus generically describes a group of threats that includes viruses, worms, and Trojan horses, malware is the umbrella term that describes different security and privacy risks that include spyware, adware, and browser hijackers. Although each of these threats is technically a little different, the line between what constitutes spyware and adware is blurry and subject to interpretation-quite simply, a given malware threat might be best described as adware based on how it behaves, but also include components that are more commonly associated with spyware. This lack of a clear definition means that many people generically refer to all malware threats as malware, spyware, or adware. You can expect to see any of these terms used to describe the new breed of pests that infect millions of PCs in a virtually silent assault.
SPYWARE
Objects deemed to be spyware include malicious programs or bits of code designed to spy on you and your PC-related activities. Some spyware objects silently track your Internet activities in the background, collecting details like the sites you've visited and then forwarding them along to a server on the Internet. Others are more insidious, designed to steal personal information like usernames and passwords, files, e-mail messages, and more. Unfortunately, the sky is the limit when it comes to what available spyware can accomplish on a computer that you have not properly secured, and the spyware infection problem is getting worse every day.
Most people have a fundamental problem understanding why anyone would want to spy on them specifically. The truth is that spyware developers are seldom after any specific person, but rather aim at having their spyware component infect as many computers as possible-often with a profit motive. Some spyware developers use the information collected from your PC for web marketing purposes, whereas others are after usernames and passwords for your Internet banking account. It's a safe bet to assume that one day the information that spyware objects collect will be used for purposes, such as blackmail, impersonation, and identity theft-if they're not already being used for those purposes.
Some of the more common types of spyware include:
-
Keyloggers. A keylogger is a malware program designed to capture keystrokes, mouse clicks, and screenshots of your computer activities. After they collect this information and save it to a file, keyloggers typically forward it to a server on the Internet. In some cases, this information is mined for details like username and password combinations, but key-loggers can also spy on correspondence like e-mail, IM chats, and more.
-
Dialers. A dialer is a particularly nasty breed of pest that uses your modem to place long distance or toll calls to overseas locations for the purpose of racking up charges on your phone bill. For a dialer to function, your modem must be connected to a phone line, so dialup Internet users are particularly at risk. Don't expect to discover a dialer by those familiar modem sounds either-dialers typically work in the background, silently inflating the charges on your phone bill to astronomical levels.
-
Data miners. A data miner is a pest designed to mine your PC for all sorts of useful information. The most common types of data miners are ones designed to track your web surfing or PC usage habits, and then use this information for marketing purposes (such as displaying targeted advertisements as you browse the web). Some data miners collect personal information about you (such as your name and address), or even lists of the programs installed on your PC. Although they may not represent a major security risk in the same manner as keyloggers or dialers, data miners are definitely a threat to your privacy-the ones that collect information about your surfing habits today could easily be redesigned to harvest e-mail addresses or dig through the contents of your personal files tomorrow.
-
Tracking cookies. Cookies are small text files that web sites and browsers use to keep track of personalized user settings, to customize content layout, and to reduce the need to enter username and password information each time you visit sites that require you to log on. When used judiciously, cookies typically don't represent a security threat and do little to put your personal privacy at risk-in fact, many sites (such as those associated with online banking) require your browser to accept their cookies as part of the connection process. Although cookies are not dangerous in the same manner as viruses or other malware threats, they do represent a potential threat to your personal privacy. This is especially true with tracking cookies, where the cookie's reason for being it to keep tabs on all of the web sites that you visit, and the ways in which you surf the Web. Ultimately, this information can be used to create a profile on your Internet activities or habits, and then used to display targeted advertisements based on your personal interests.
ADWARE
Software is distributed over the Internet in a number of different ways. Some of the programs that you download and install are licensed commercial programs that you must pay for. Others, known as shareware, enable you to try the program for free, but require you to purchase it if you intend to continue using it. Freeware is another popular type of software, where the developer grants you the right to use the program, free of charge.
Over the past few years, however, a new software distribution method has become increasingly popular. Adware, or advertising-supported software, provides a way for developers to release their software to the general public for free, while still making money. The idea is that an advertiser's banner, message, or even another program is bundled together with the adware program for a fee, which keeps the developer in business. In effect, the money made from advertising is the developer's payment for creating the program.
Where once adware-style programs did little more than include the advertiser's banner somewhere within a program window, today, adware is much more complex-and potentially dangerous. Many adware programs collect information about your PC or how you use the Internet, and then deliver targeted ads to you. Sometimes these ads display with the main program window, and sometimes they're of the pop-up variety-those annoying browser windows that literally open out of nowhere to display an advertisement as you're trying to accomplish another task.
Perhaps the most common examples of adware in action are the free versions of popular file sharing programs like Kazaa and BearShare. These programs typically install an adware component (a separate program in the case of BearShare, as shown in Figure 10-1) during the program installation process, and most users agree to allow this-while some adware programs let you know that an ad-related component is being installed on your PC, others simply bury this detail in the licensing agreement. In effect, you agree to install adware on your PC (and have different types of information about you collected) by accepting the license agreement-it's up to you to read the fine print, after all.
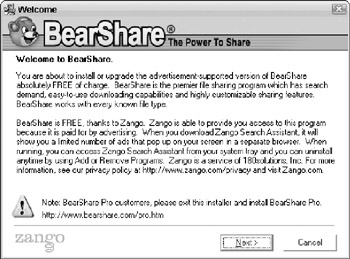
Figure 10-1: The free version of the popular BearShare file-sharing program informs you that adware will also be installed.
There's little question that adware has the potential to put your privacy and security at risk, but the extent to which this is true varies largely from program to program. Some people think that giving away details of their usage or surfing habits by using adware is a better deal than paying for the full version of a program. Others find the deluge of pop-up windows or integrated banners often associated with adware programs to be annoying and beyond reproach. Certainly, adware is a legitimate method for developers to be paid for their work, and not every adware program is dangerous. However, you should always take the time to read the licensing agreement associated with an adware program before you install it. If the program doesn't include details about what information is being collected about you (if any) and how this information will be used, you're always better off seeking out an alternative program.
BROWSER HIJACKERS
As the name suggests, browser hijackers are all about taking control of your web browser. Specifically, browser hijackers are a form of malware designed to replace your own web browser settings with new values that you typically cannot remove or change by traditional means. For example, a browser hijacker might change your browser's home page and search engine settings, or even add its own shortcut links to your Favorites or Bookmarks list. When you try to remove these entries and return to your original settings, a browser hijacker will almost always undo your changes and return to its own preferred settings.
Browser hijackers are without a doubt one of the most annoying types of malware, but also have the potential to be both offensive and dangerous. For example, it's not uncommon for a browser hijacker to replace your preferred home page with a pornographic or a gambling site. Similarly, browser hijackers are seldom interested in changing browser settings alone-although that may be the visual part of the equation, most also infect your PC with various spyware and related objects that may be a threat to your security and privacy.
The most common and dangerous browser hijacker making the rounds on the Internet is known as CoolWebSearch. The particular pest is among the worst of the worst (and most prevalent) in the malware world, and can be next to impossible to remove even with the help of anti-spyware software. You'll learn more about detecting and removing browser hijackers (and specifically CoolWebSearch) later in this chapter.
How Malware Infects Your PC
Malware typically infects PCs in a very different ways than viruses and worms. Viruses typically rely on the user opening an infected file, whereas worms can take advantage of operating system security holes that exists as a result of not applying patches and updates as they're released. Infecting a system with malware, on the other hand, often requires you to do nothing more than visit an infectious web page or even click a hyperlink.
Perhaps the primary reason why so many computers are infected by malware is a result of the sneaky nature of spyware developers. Some trick you into downloading malware objects by displaying misleading web pages suggesting that your computer is already infected. Others use pop-up ads that appear to be normal Windows dialog boxes that coax you into clicking what is actually a link. There are even web pages that download and install malware on your computer automatically when you do nothing more than visit a certain web address.
Some of the most common ways through which malware infects PCs include:
-
Program installations. Malware is commonly bundled into seemingly legitimate programs, and installed on your system as part of the primary program's installation process. In some cases, the legitimate tool is designed with the purpose of distributing spyware. In others, a spyware developer has taking an existing program and recompiled it to include malware components.
-
Toolbar installations. You can greatly extend the capabilities of Internet Explorer and other web browsers by using legitimate third-party toolbars, like the ones that Google and Yahoo! offer. However, many third-party toolbars that appear to be loaded with useful features actually contain malware components. In some cases, toolbars are installed into web browsers like Internet Explorer when you do nothing more than visit an infectious site or click misleading links. Toolbars that extend the capabilities of browsers are commonly referred to as Browser Helper Objects (BHOs).
-
Surfing the Web. Some web sites are programmed by spyware developers to automatically download and install malware-related threats when you visit the site or a particular web page. These sites typically take advantage of low security restrictions in web browsers like Internet Explorer to download and install malware components using technologies like ActiveX or Java. Malware threats that are downloaded and installed in this fashion are often referred to as drive-by downloads.
-
Pop-up ads. Web browser pop-up windows are among the most notorious sources of malware infections. These smaller browser windows typically include an advertisement or warning message stating that your computer is already infected by spyware, or supposedly provide a link to a free spyware-removal tool. Others look like legitimate Windows dialog boxes, complete with Yes and No buttons. When used as a malware delivery vehicle, clicking these ads installs malware objects on your PC. It should be noted, however, that only a small percentage of pop-up ads relate to the installation of malware.
-
Cookies. As you surf the Internet, chances are good that most of the web sites you visit will place cookies on your PC, usually for legitimate purposes. However, many web sites display banners provided by web advertising services, which often track and collect visitor information via tracking cookies. Unless you've chosen to block all cookies or only allow ones from certain web sites, chances are good that one or more tracking cookies are already present on your computer.
| Cross Reference | For details on managing browser security settings-including disabling pop-up windows, configuring cookie settings, and managing browser add-ons-refer to Chapter 5. |
Signs of Infection
The best way to determine whether your computer is infected by malware-related threats is to complete a scan with a dedicated spyware detection and removal tool. However, you should also keep an eye open for the following warning signs, which often indicate that any number of different malware threats are infecting your computer:
-
One or more pop-up windows appear when you log on to Windows Vista or open your web browser.
-
Your computer is noticeably slower than in the past.
-
You're experiencing system errors or crashes with greater frequency.
-
You see unfamiliar icons in your system tray.
-
Your web browser's home page has been changed to a new web site.
-
You notice new and unfamiliar toolbars on your web browser.
-
Your computer is behaving strangely, or different than it normally does.
-
Your phone bill arrives and is loaded with charges for calls made to toll numbers or overseas locations.
| Note | If any of the warning signs outlined in the previous list describe your PC, it doesn't necessarily mean that your computer has a malware infection. It could be that your system is infected by a virus, or in need of maintenance tasks like removing unused programs and files or defragmenting your hard drive. Any time that you notice behavior outside of expected parameters, however, it's not a bad idea to scan your system for possible malware threats. |
Malware Risks
There's simply no shortage of ways in which malware can cause you or your computer harm, with new and even more dangerous methods being developed all the time. Some of the security risks and common types of damage caused by malware include:
-
Information or identity theft. Many malware threats are designed for the expressed purpose of stealing information from your PC. Items sought after can include virtually everything from username and password combinations to files to correspondence like e-mail messages or IM chats.
-
Internet tracking. A number of malware threats are aimed at tracking your Internet usage history and habits for the purpose of displaying targeted advertisements. Some of these objects track your Internet activities relatively anonymously, but others seek out personal details as well.
-
System stability issues. Just like any other piece of software, malware threats can be poorly programmed, and by extension lead to system stability issues or even crashes. Some malware objects are known to overwrite or replace important operating system files, whereas others disable security programs like antivirus or firewall software.
-
Inability to change web browser settings. Almost all browser hijackers lodge themselves onto your computer so that it's virtually impossible to return to your original settings without using anti-spyware software or a dedicated threat removal program. In some cases, completely reinstalling your system is the only way to remove these pests for good.
-
Inability to access certain web sites. Many malware threats are designed to stop you from accessing certain popular web sites, or to redirect you to other sites (typically carrying advertising) in cases where a page cannot be found.
-
Inability to use your computer reliably. From relentless pop-up ads to disabled software, there's no shortage of ways in which malware can harm your computer so that you cannot use it reliably. For example, a number of malware threats continuously open pop-up windows with banner ads regardless of whether you close existing windows or even stop underlying processes like Internet Explorer.
-
Financial costs. Some of the more advanced and extreme malware threats are designed to hit you where it hurts-right in the pocketbook. Dialers almost always lead to massive charges on your phone bill, but malware that steals credit card or banking information can also lead to financial losses, not to mention identity theft issues.
EAN: 2147483647
Pages: 135