Cisco Security Agent
| The Cisco Security Agent sits directly on the end station. The Cisco Security Agent is often identified by an icon of a red flag at the bottom of the desktop. A waving red flag notifies the user of suspicious behavior that could be indicative of an attack. The Cisco Security Agent Panel is composed of the following categories:
Figure 8-9 provides an example of the Cisco Security Agent Panel. Figure 8-9. Cisco Security Agent Panel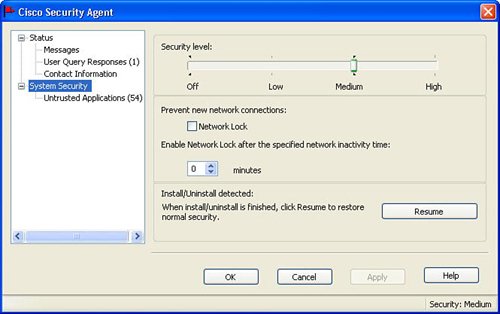 StatusThe Status area of the Cisco Security Agent panel provides information to the end user on what the Cisco Security Agent is doing. This status feedback on the Cisco Security Agent Panel is important because the end user typically does not have any direct access to the Management Center for Cisco Security Agents. The main Status area provides several items of important information about the Cisco Security Agent including the following:
The following subcategories are available in the Status category:
System SecurityThe System Security area provides a mechanism where certain users can specify a default security policy (high, medium, low) if this option is allowed by the Management Center. The System Security area also provides an option to restrict new network connections after a certain network inactivity timeout. The System Security area also provides a vehicle to display to the user which applications are natively untrusted by the Cisco Security Agent. These untrusted applications can result in the user being queried about permission to use the application if the application attempts to modify critical system resources. The Cisco Security Agent panel also provides an option to remove applications for the untrusted list, if this option is enabled by the Management Center. Figure 8-10 displays a sample of the display of a few of the untrusted applications on the Cisco Security Agent Panel. Figure 8-10. Untrusted Applications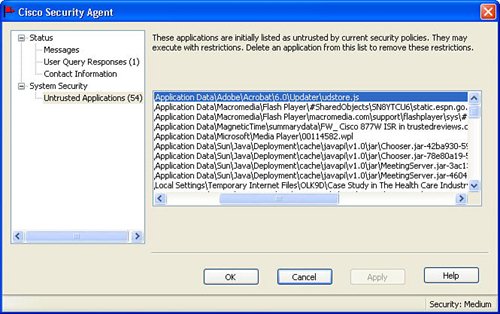 |
EAN: 2147483647
Pages: 112