Setting Up a Container Policy Package
| To have a container policy package affect the policies, you must first create the policy package. To create a Container Policy Package, do the following:
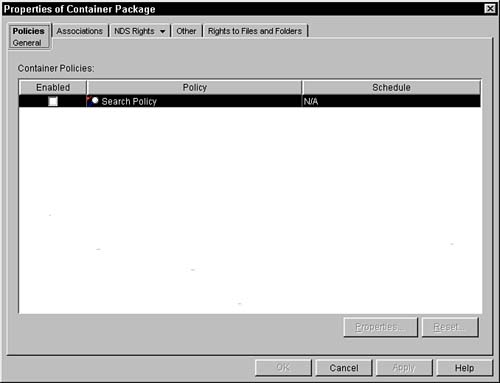
The following subsections describe each of the fields and property pages that are available in the Container Policy package. Introducing the Policies PageThe Policies page lists the set of available policies and those that are active. Figure 5.1 shows this policy page. Because no platform-specific policies are currently in the Container package, only the General page of the Policies tab is available. Figure 5.1. The Container Package policy page.
After you create a Container Package, you can activate policies. When you click the check box to the left of a policy within the policy package, that policy becomes active. An active policy is designated by a check in the check box. You can modify the details of any particular policy by selecting the policy and clicking the Properties button. The Reset button on the Policies page resets the selected policy back to the system defaults for that policy. Understanding the Associations Property PageThe Associations page of the Container Policy Package displays all the locations in the tree (containers) where the policy package has been associated. These associations do not necessarily reflect where the policy package is located in the directory. The agents that are associated with servers that are in or below those containers have this policy package enforced. Clicking the Add or Remove buttons enables you to add or remove containers in the list that are associated with this policy package. Defining the NDS Rights Property PagesThe eDirectory Rights property page is made up of three pages. You can get to each of the pages by clicking the small triangle to the right of the page name and then selecting the page you want to be displayed. These pages enable you to specify the rights that users have to this object in the directory. The following subsections briefly discuss each of these pages. These eDirectory Rights pages are displayed for every object in the tree. Trustees of This Object PageOn the This Object page you can assign objects as trustees of the Container Policy Package. These trustees have rights to this object or to attributes within this object. If the user admin.novell has been added to the trustee list, this user has some rights to this object. To get into the details of any trustee assignment (to modify the assignment), you need to click the Assigned Rights button. When you click the Assigned Rights button, after selecting the user you want to modify, a dialog box appears that enables you to select either [All Attribute Rights] (meaning all the attributes of the object) or [Entry Rights] (meaning the object, not implying rights to the attributes). From within the Assigned Rights dialog box, you may set the rights the object may have on this package. You can set those rights on the object as well as any individual property in the object. The rights that are possible are the following:
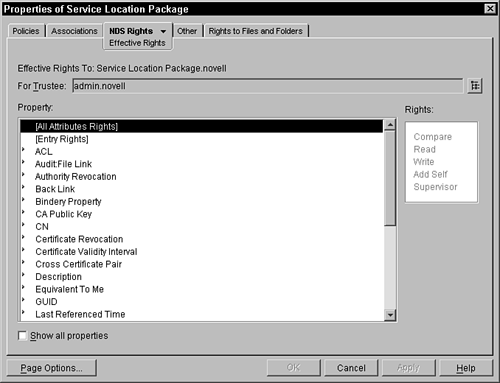
If you want to add the object as a trustee to an attribute, you need to click the Add Property button to bring up a list of properties or attributes that are available for this object. From this list, you can select a single attribute. This attribute is then displayed in the Assigned Rights dialog box. From there, you can select the attribute and then set the rights you want the trustee to have for that property. A user does not require object rights to have rights on a single attribute in the object. Remember that rights flow down in the tree, and if you give a user or an object rights at a container level, those rights continue down into that container and any subcontainers until that branch is exhausted or another explicit assignment is given for that user in a subcontainer or on an object. An explicit assignment changes the rights for the user at that point in the tree. Inheritance rights filters may also be placed to restrict this flow of rights down into the tree. Inherited Rights Filters PageThe Inherited Rights Filters page enables you to set the inherited rights filter (IRF) for this object. This filter restricts the rights of any user that accesses this object, unless that user has an explicit trustee assignment for this object. You can think of the IRF as a filter that lets only checked items pass through unaltered. Rights that bump up against an IRF are blocked and discarded if the item is not checked. If, for example, a user who had write privileges inherited at some point above (they were explicitly granted that right at some container at or above the one they're in) were to run into an IRF for an object or attribute that has the write privilege revoked (that is, unchecked), when the user got to that object his write privilege would be gone for that object. If the object were a container, he would lose write privileges for all objects in that container and subcontainers. You can effectively remove supervisor privileges from a portion of the tree by setting an IRF with the supervisor privilege turned off. You must be careful not to ever do this without someone being assigned as the supervisor of that branch of the tree (given an explicit supervisor trustee assignment at the container where the IRF is done), or you will make that part of the tree permanent (that is, you will never be able to delete any objects in that branch of the tree). ConsoleOne helps to keep you from performing this mistake by giving you an Error dialog box that keeps you from putting an IRF on the [Entry Rights] of the object with the supervisor right filtered away without having first given an explicit supervisor assignment on the same object. Effective Rights PageThe Effective Rights property page enables you to query the system to discover the rights that selected objects have on the object that you are administering. Within this page (see Figure 5.2) you are presented with the distinguished name (DN) of the object whose rights you want to observe. Initially, this is your currently logged-in user running ConsoleOne. You can click the Browse button to the right of the Trustee field and browse throughout the tree to select any object. Figure 5.2. Effective Rights page.
When the trustee object is selected, you may then move to the properties table on the lower half of the screen. As you select the property, the rights box to the right changes its text to reflect the rights that the trustee has on that property. These rights may be via an explicit assignment or through inheritance. Looking at the Other Property PageThis page may or may not be displayed for you, depending on your rights to the plug-in that now comes with ConsoleOne. This page is particularly powerful and should not be used by those who do not have an intimate knowledge of the schema of the object in question and its relationships with other objects in the directory. The intention of this property page is to give you generic access to properties that you cannot modify or view via the other plugged-in pages. The attributes and their values are displayed in a tree structure, allowing for those attributes that have multiple types (are compound types that consist of, say, an integer and a distinguished name, or a postal code that has three separate address fields). Every attribute in eDirectory is defined by one of a specified set of syntaxes. These syntaxes identify how the data is stored in NDS. For this page, ConsoleOne has developed an editor for each of the different syntaxes that are currently available in eDirectory. When an attribute is displayed on this page, the editor is invoked to display the data and then modify it should the user click a specific attribute. If the syntax for an attribute were a string or an integer, for example, an inline editor is launched enabling the administrator to modify the string or the integer value on the screen. More abstract syntaxes such as an octet string require that an octet editor be launched, giving the administrator access to each of the bytes in the string, without interpretation of the data. The danger with this screen is that some applications require that there be a coordination of attribute values between two attributes within the same object or across multiple objects. Additionally, many applications assume that the data in the attribute is valid, because the normal user interface checks for invalid entries and would not allow them to be stored in the attribute. If you should change a data value in the Other page, no knowledge of related attributes, objects, or valid data values is checked because the generic editors know nothing about the intention of the field. Should you change a value without making all the other appropriate changes or without putting in a valid value, some programs and the system could be adversely affected. Rights are still in effect in the Other property page and you are not allowed to change any attribute values that are read-only or that you do not have rights to modify. Using the Rights to Files and Folders Property PageThis page in the property book is present in all objects in the directory. This property page enables you to view and set rights for this object onto the volumes and specific files and folders on that volume. You must first select the volume that contains the files and folders in which you are interested. You can do this by clicking the Show button on the right and then browsing the directory to the volume object. Selecting the volume object places it in the window labeled Volumes. When that volume is selected, you can then go to the Add button to add a file or folder of interest. This brings up a dialog box enabling you to browse to the volume object; then clicking the volume object moves you into the file system. You can continue browsing that volume until you select the file or directory for which you are interested in granting rights. Selecting the file or folder in the lower pane displays the rights that the object has been granted on that file or folder. To modify the rights, simply click on or off the rights that you want to have explicitly granted for the object. You can also see the effective rights that the object has on the files by clicking the Effective Rights button. This displays a dialog box, allowing you to browse to any file in the volume and have the effective rights displayed (in bold) for the object. These effective rights include any explicit plus inherited rights from folders higher in the file system tree. Remember that any user who has supervisor rights to the server or volume objects automatically gets supervisor rights in the file system. |
EAN: N/A
Pages: 137
 Policy Package or by selecting the Policy Package icon on the toolbar.
Policy Package or by selecting the Policy Package icon on the toolbar.