Where Modern Vulnerabilities Exist
| Security vulnerabilities are everywhere and in everything. Have you ever wondered why there are so many successful hackers breaking into systems? Do we really believe that every 17-year-old that breaks into a nuclear power plant is a super-genius? The fact of the matter is that you can't toss a pebble without striking an object that is vulnerable. The average hacker has only to sip a cup of hot cocoa while a scanning application looks across thousands of organizations for well-known vulnerabilities. The hacker may not even know what the vulnerability is or why it exists, but the newly downloaded scanner is pre-programmed with thousands of wiz-bang gadgets and exploits. Given a few hours, the hacker will find more vulnerable systems than he or she knows what to do with. What Do I Mean by "Vulnerable?"When an object is vulnerable, it simply means that the object can be affected in an undesirable way or allow for access to information and services without consent or control. When an exploit like a new buffer overflow attack is combined with a corresponding vulnerability like an unpatched Windows NT server, then "something bad happens." A system without a UPS/battery backup is vulnerable to power outages, just as an unpatched Linux box sitting on the Internet is vulnerable to a multitude of hacker tools. The most common vulnerabilities are related to DoS threats, meaning given a specific set of conditions, a system or service will become unavailable for its normal use. An example would be a network-based overflow attack that stops email services from running, or an unexpected string of variables that causes a Web server to reboot. These incidents result in lost time, lost customers, and lost money. On the more intense side, a vulnerability can also allow someone to gain access to read, modify, execute, or delete actual data on your system. Penetration attacks involve hackers attempting to gain access to systems, networks, and resources they are not authorized to access. The Origin of VulnerabilitiesVulnerabilities can come from anywhere or result from any number of circumstances. There are, however, two factors that seem to account for the majority of vulnerabilities: buggy software and human beings.
Vulnerable Operating SystemsIf anyone in your organization is using a workstation or server that is running any version of Windows, UNIX, or MacOS, then you have vulnerabilities; it's that simple. Perhaps these vulnerabilities have not yet been discovered, but every significant operating system is full of features that can be exploited to make the system act in an undesirable manner. The thousands of vulnerabilities we have today existed long before we even knew about them! Vulnerabilities that will be discovered next year are actually in our systems today. It is important to understand that when we hear about a new vulnerability being discovered, the vulnerability is not really "new," just "newly discovered." Someone may have known about it several years before and has been using it to silently sneak into systems around the world. Writing an operating system requires a large staff of programmers who create millions of lines of code under a tight business-driven deadline. Mainstream operating systems like Windows and Solaris are full of millions of lines of hidden code that the public will most likely never have access to. This code is full of thousands of flaws that are nearly impossible to find, even for the handful of people who have access to view the code. Windows 2000, for example, has more than 35 million lines of code in it, developed by multiple teams within multiple organizations. It would be quite impossible to make a profit if the staff was expected to fully test every line of code under every possible combination and event. It is also extremely difficult to ensure that the programming staff has not inserted its own intentional back doors into the code. Some organizations are better than others at avoiding vulnerabilities and malicious coding, but in reality, it is the general public who is truly expected to put the software to the ultimate test.
Significance of Operating System VulnerabilitiesThe operating system should be viewed as the foundation on which the entire castle is built. If someone tunnels under the walls and takes out a support beam, then the walls will come crumbling down no matter how high they are. Likewise, if someone gains access to the operating system, it will be difficult to prevent him or her from gaining access to the rest of the system and the rest of the network. One important task in information security is to keep operating systems from being hacked. Remember, an operating system controls the basic functionality of everything that is on a computer. The operating system typically has access to every file, every application, every user, and quite often, the history of all actions. The operating system also has the final say in many security-related decisions. If you can can control the operating system, you control just about every application and piece of data on the device. Vulnerable ApplicationsApplications are very similar to operating systems. After all, what is an operating system but a giant application? Application vulnerabilities are very common, and most major applications on the market have vulnerabilities in them. The important difference between these vulnerabilities and operating system vulnerabilities has to do with the significance of the threat, which we will discuss in a moment. The origin of most application vulnerabilities is somewhat similar to that of operating system vulnerabilities. Multiple programmers, working under a deadline, fail to place precautionary checks, and at the same time, make simple errors in the code. Applications are often written with standard programming languages and precompiled toolsets. A precompiled toolset is a part of the program that someone else developed; the application developer is simply including it in his or her application. For example, to make an application play music, the application programmer normally would not want to go through all the trouble of writing hundreds of lines of code when a standard music function has already been written by someone else. Thus, the programmer will pay a fee and insert someone else's code (which they cannot read) into the application and continue on with life. Sadly, such code often has flaws and vulnerabilities that the programmer is unaware of. Subsequently, the programmer has just introduced vulnerabilities into the application, vulnerabilities that the developer has no chance of ever seeing or fixing. Significance of Application VulnerabilitiesWhen considering the significance of an application vulnerability, it is important to think in terms of relational security and avoid focusing on just the application itself. Applications have several significant security relations that extend beyond functionality and services. The application has a relationship with its hosting computer, the network it is on, the data it processes, and the clients that access it.
Vulnerable NetworksOur networks are the series of roads, paths, and tunnels that connect our kingdoms to the rest of the world. Some of these roads are wide, clean, and well-lit, while others are narrow, dark, and cross through the backyards of some very questionable characters. Down these roads come many travelers, seeking information and services. These travelers come from unknown locations and can provide little in the way of identification or proof of intent. The requirements for protecting the castle are multiplied by the number of roads that lead to it. Where Are the Network Vulnerabilities?The average network consists of many components. Telecommunication lines connect buildings around the world. Routers work to direct communications to and from the proper parties. Hubs and switches distribute communications across numerous devices. Networks also include the desktops, servers, operating systems, and applications connected to them. Therefore, we must widen our focus a bit when considering where a network can be vulnerable. A vulnerable network is simply a network that can be accessed or manipulated without consent. This means that if any device on a network, including the routers, switches, servers, workstations, or even the wires themselves is compromised, the network itself is compromised. Therefore, the network shares its vulnerabilities with all devices attached to it. Significance of Network VulnerabilitiesA vulnerability in a network is simply a door through which an attacker can attempt to gain access to communications and devices. Once access is obtained, the hacker can steal information and services, or simply stop them from functioning. The two common concerns with network vulnerabilities have to do with vulnerable access points and communications.
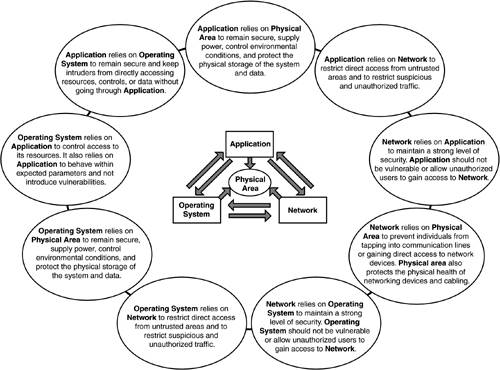
Network sniffing is a very common method through which hackers can gain amazing results. Through a network, an attacker can listen to email communications, gather passwords, obtain files, and discover many things about an organization. Since sniffing only requires the hacker to listen somewhere in the line of communication, there are many hidden areas where an attacker could passively exist. Communications are also subject to manipulation. A hacker attempting to gain access to a resource may wait for a valid communication to take place and then take control of that communication. A hacker can also wait for a valid user to access his or her account, record the authentication process, and then replay this authentication process later to gain access (a replay attack). Special Considerations for Network CommunicationsSimilar to a phone call, when we communicate with various parties on the Internet, through WANs or over direct modem dialing, information is traversing devices over which we have little or no control. Take the case of dialing with a modem between two computers. The data communication between these systems is pushed through miles of wires and several phone switches before being received. This information must be considered vulnerable at every point from where the communication left the first modem and entered the second. On an Ethernet network, the vulnerability is even more severe. Tapping into a local area network (LAN), WAN, or Internet communication exchange simply requires free hacking tools and a computer or device that exists somewhere in the path of the communication. Send an email from anywhere to anywhere and you can be sure there are several people that have the opportunity to intercept it. Physical VulnerabilitiesPhysical vulnerabilities are often overlooked when an organization considers security. What many people don't realize, however, is that operating systems, applications, and networks all rely on the physical security of the devices themselves. How can we secure data or services if the systems on which they exist are not secure? Where Are the Physical Vulnerabilities?Physical vulnerabilities include any physical component of a system or device that could be exploited for an attack. They comprise everything from the keyboard attached to a server to the power plug behind it. To properly operate and maintain a system, there must be some form of physical access to it, and by physically being able to touch a computer, one has a great deal of control over it. A hacker, for example, could bang away on a keyboard trying to gain access, or he or she could simply unplug the machine and cart it off the premises. Commonly, a system or device can be fully compromised by physically accessing it. Many organizations, for example, do not configure passwords for the physical connection (console) port on routers. This means that in many environments, a hacker could simply walk in with a laptop and plug into a router to perform basic configuration options. Even simpler, a hacker could stroll casually into the average server room and will often find unattended systems that have been logged in as root or administrator. In such cases, the hacker could simply take a few moments to create an account that will give total control of the system, and then leave to perform the rest of the hacking remotely. Significance of Physical VulnerabilitiesSimilar to how operating system vulnerabilities can affect the security of applications, a physical vulnerability can affect the security of everything in the area. A hacker with access to someone's workstation has many options that would otherwise be unavailable. Likewise, an attacker that can physically plug into an internal Ethernet port has the unlimited potential to compromise every system, device, and link connected to that network. When such physical vulnerabilities are allowed to exist, it greatly diminishes the security of every system, device, and network communication within the organization. Chained VulnerabilitiesVulnerabilities should not be seen independently, but as an interlinking chain of dependence such as is illustrated in Figure 7.1. Holes in security are most often formed through a series of minor vulnerabilities that, considered individually, appear to have no major effect on an organization's security. However, by chaining two or more of these minor vulnerabilities together, hackers frequently find ways of compromising security. Likewise, major security violations are most often composed of small events, which would independently be considered "normal" and not raise any flags. It is by forming a series of normal events into a malicious chain that many attacks actually occur. Because we make ourselves vulnerable through a series of chains, it would only be logical that hackers could attack us by reverse-engineering such chains. We must be certain to be conscious of the chain of events surrounding any given situation, thus we should widen our focus in accordance with the virtues and rules of security. Figure 7.1. Security Dependencies.
It is extremely important for those associated with the security of an organization to be constantly thinking about chains. All too often, a security administrator will open a port on the firewall or make an exception to the security rules simply because it seems like a minor vulnerability. Unfortunately, it is often difficult to comprehend the complete chain of vulnerabilities that are related to everyday actions. This is another reason why it is vital that organizations focus on the rules and higher security principles, and avoid making numerous exceptions. This makes it important to follow the concept of "creating stillness" by having filtered logs for a clear understanding and an unfiltered backup for following seemingly unimportant events (see Chapter 5, Developing a Higher Security Mind). Many successful attacks go unnoticed simply because the hacker used a chain of seemingly unimportant events that were never investigated. |
EAN: 2147483647
Pages: 119