Assessing the Risks
| Blogs offer an environment where people can share their ideas and feelings with friends and family or with others who have similar interests, or even with the public at large. They encourage creativity, expression, and interaction. Blogs enable people to get involved and have a voice in politics and news reporting and other forms of participatory citizenship. They enable people to meet new friends and expand their horizons. So what makes people anxious about blogs? The Blogging PhenomenonThere are more than 70 million blogs online today (www.blogherald.com). I've talked about blogs frequently throughout this book, in part because they are a relatively new tool for the general public and have become a wildly popular trend that is often in the headlines, usually because of abuses. Unfortunately, a small segment of the population uses blogs in hurtful and illegal ways. Predators and bullies use the information that was intended to allow expression and inspire contact to spam, con, stalk, harass, and groom victims of every age. In a microcosm, blogging reinforces the point that anything new and popular, such as the Internet itself, poses problems in part just because it is new. People simply haven't learned about the potential risks and don't know how to blog safely. Criminals and BlogsAs I mentioned in Chapter 1, "The Landscape of Risk," about half of all those who blog use their blogs as a form of emotional therapy. Because the blog format often is geared toward enabling people to reveal their attitudes, feelings, and personal information in a public way, they are attracting predators and criminals who hunt for the emotionally vulnerable or unwary. As in the real world, where you're advised against looking distracted or passive when walking alone, projecting an emotionally vulnerable face to the general public in a blog is an invitation to cybercriminals and predators. Think About It According to WiredSafety (www.wiredsafety.org), in 2005 about one-third of students in the United States had Internet blogs, although only about 5 percent of parents were aware of that fact. Remember, the creators of the Internet didn't invent criminals or predators. The people who commit crimes online are the same people who commit crimes in the physical world. The Internet and the services enabled by it, such as blogs and social networks, are just new tools for them to use. The Information ConnectionAll types of cybercriminals leverage information posted online to help them identify opportunities. Identity thieves look for identifying information, robbers look for items to steal, scam artists target people who seem susceptible to scams, and sexual predators search for victims. Middlemen aid these criminals by building catalogs of people and items that might be of interest: information about children, identities, addresses of homes whose owners are away, and locations of valuable cars. A lot of the leveraged information is gleaned from publicly accessible blogs, where people unthinkingly post all kinds of data about themselves. While much of this information is provided by the victims themselves, sometimes it is unintentionally provided by friends or family members. It is the cybercriminal's ability to find in one place pieces of information that have been left over time by multiple people that gives him or her an advantage over other criminals, who have no such repository of information to sift through. What You Expose About Yourself and OthersBloggers expose their information in a variety of formsfrom text descriptions of their feelings to photos and videos, music preferences, voice clips, lists of favorites, and maps. A blog's topics can also reveal personal information. For example, adult and older bloggers are often interested in their family tree and genealogy research and frequently post all this information online (see Figure 9-1 on the next page), providing full names, mother's maiden name (a frequent password prompt used by online sites and financial institutions), birth dates, locations, marriage information, and so on, going back several generations. This is an identity thief's dream come true. Figure 9-1. A genealogy blog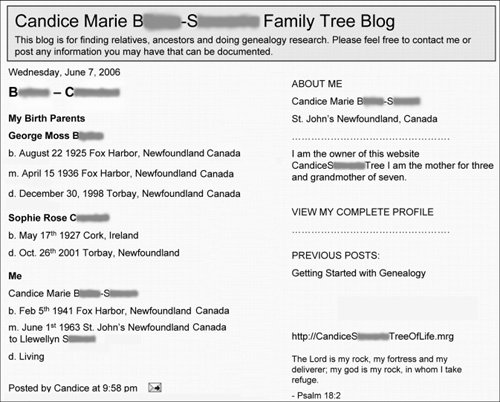 Information can also be discerned from a blog's background motif, a blogger's nickname, a Web URL (www.blogsite.Cecil24livin'thelifein-Victoria or www.blogsite.RobWalters26, for example), emoticons displayed, quotes, address field information, relationship status, or a biography. Figure 9-2 on page 77 shows a typical blog that provides a lot of information about its owner and is publicly posted. Figure 9-2. A blog that reveals too much to predators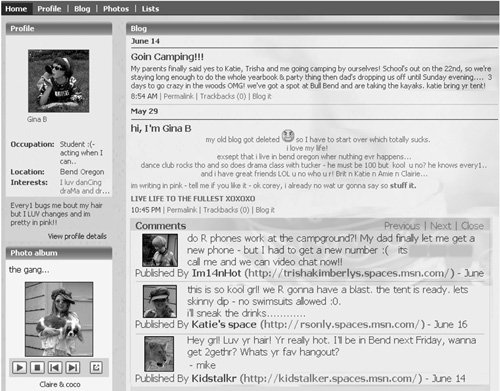 Many people provide contact information, such as IM and e-mail accounts, phone numbers, and full street addresses. Many bloggers fill out one of the myriad surveys people can post about themselves, thinking that a flirty answer about their personal life is just fun, until a predator latches on to their answer and targets his next victim. Surveys and profiles are particularly high-risk collections of information. I found answers such as these to a survey on a 17-year-old girl's site (I've inserted the categories of answers):
Find Out More Find out about the risks of sharing information in Chapter 5, the risks of sharing photos and other visual clues in Chapter 4, and how predators prey on the emotionally vulnerable in Chapter 6. For information about the risks involved in blogging when you're grieving, refer to www.look-both-ways.com. Who's Most at Risk?According to David Huffaker's analysis and FBI data, at particularly high risk are young people between the ages of 13 and 15, when they make their blogs available to the public instead of to a limited group of friends and family. This is a time when teens are reaching out for new identities, friends, and validation. At the same time, they are often struggling with their existing relationships with their current friends, with their girlfriend or boyfriend, with family members (especially parents), and with teachers, as well as with their own unstable emotions. Also at higher risk are young people who live in rural areas or suburbs (Wolak et al., 2004). They have a greater need to meet new people (they probably already know everyone in town) and tend to be more trusting of strangers than are kids in urban environments.
But people of any age who are looking for new friends, have low self-esteem, or who are suffering from depression, grieving, or otherwise emotionally vulnerable are also likely victims. In less than nine minutes on average, I can locate adults, as well as teens, through the information they've put in their public blogs. Ironically, some of the worst examples of adults providing too much information in public blogs are individuals whose jobs are computer related. Although they might be confident techsperts (technical + expert = techspert) who can avoid technical issues such as viruses and spyware, they are often no more likely to understand human predators and the risks they pose than the average 13-year-old. |
EAN: 2147483647
Pages: 157