Configuring, Managing, and Troubleshooting Internet Explorer Security Settings
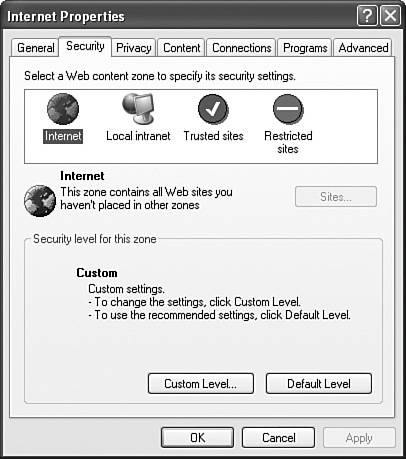
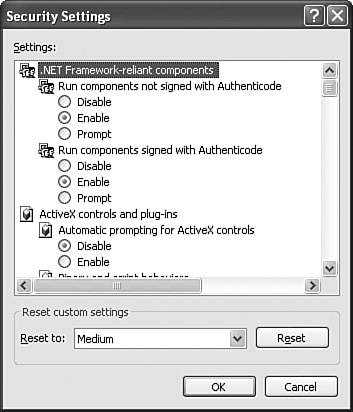
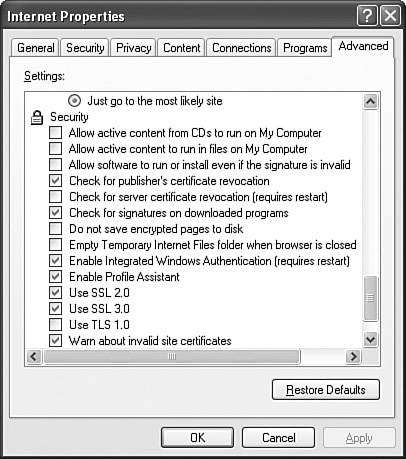
| Objective: Configure, manage, and troubleshoot Internet Explorer security settings. You can configure your Internet Explorer's security settings in the Internet Options console. This console is available in Control Panel, as well as on the Tools menu in Internet Explorer. The Security tab displays a list of website types called Internet zones, as shown in Figure 12.12. Figure 12.12. Security settings are established separately to each type of website location. To configure the security settings for an Internet zone, click the zone to select it and then click the Custom Level button. The Security Settings dialog box opens, as shown in Figure 12.13, where you can select each individual security setting or set an Internet zone to a pre-defined group of security settings that range from Low, to Medium-Low, to Medium, to High. Figure 12.13. Individual security settings apply to an Internet zone for a custom security definition. To establish the privacy settings, click the Privacy tab. Here you can select a preset level for handling cookies. If you click the Sites button, you can block or allow privacy information to be exchanged with specific websites. To establish a different method for handling cookies in the Internet zone, click the Advanced button and select your preferred settings. For security settings that govern specific behaviors in Internet Explorer, click the Advanced tab and scroll down the window to the Security category. You see a screen similar to Figure 12.14. Here, you can set options such as reducing problems caused by software downloaded and run from the Internet (do this by clearing the Allow Software to Run or Install Even if the Signature Is Invalid check box). Figure 12.14. The Advanced tab of Internet Options contains additional security settings. One of the ways that you can secure Internet Explorer is to ensure that it is updated with the latest patches and service packs available. Microsoft is constantly providing new security updates. To look for these updates, open Internet Explorer, click the Tools menu and select Windows Update. This will take you to windowsupdate.microsoft.com, where you can download and install all types of updates for Windows XP. When you are troubleshooting security or privacy problems with Internet Explorer, click Start, Open text, and type msinfo32 in the Run box and press Enter. This opens the System Information utility, which you can navigate to Internet Settings, Internet Explorer, and then Security. You can also view the Content settings to look at certificates and publishers. If you are concerned that there is a security problem with the protocol, you should navigate to Components, Network, and then Protocol to see the configuration that is running on your computer.
Service Pack 2 (SP2) for Windows XP Professional was introduced with a focus on proactive security. It includes the following security features, tools, and settings:
|
EAN: 2147483647
Pages: 193
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XII Web Design and E-Commerce
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment