3.2 Trust properties and types
Trust relationships in a Windows environment can be classified based on the following properties: the way they are created (implicitly or explicitly), whether they are one- or two-way trust relationships, and whether they are transitive or not. The different trust types and their properties are listed in Table 3.1. They are illustrated in Figure 3.3.
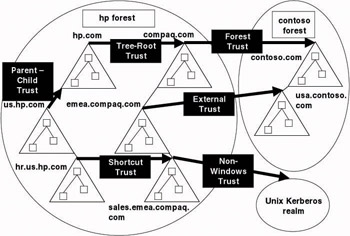
Figure 3.3: Windows trust types.
A Windows Server 2003 administrator can view trust relationships and their properties through each domain object’s properties in the AD Domains and Trusts MMC snap-in, or by using the netdom.exe or nltest.exe command prompt utilities (these utilities will be explained later on in this chapter). Figure 3.4 shows the trusts tab in the properties of a domain as you can see it from the AD Domains and Trusts MMC snap-in. If you open the properties of a particular trust relationship, you get more detailed information on the specific properties of that particular trust relationship (as shown in Figure 3.5).
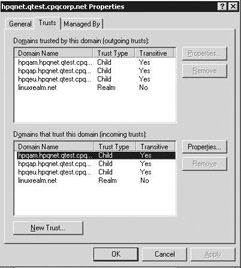
Figure 3.4: Trusts tab.
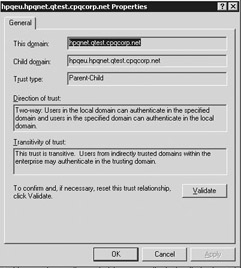
Figure 3.5: Trust properties.
| Trust Type | Default Properties |
|---|---|
| Tree-Root Trust | Implicitly created, transitive, two-way |
| Parent-Child Trust | Implicitly created, transitive, two-way |
| Shortcut Trust | Explicitly created, transitive, one- or two-way |
| Forest Trust | Explicitly created, transitive, one- or two-way |
| External Trust | Explicitly created, nontransitive, one- or two-way |
| Non-Windows Trust | Explicitly created, nontransitive, one- or two-way |
Implicitly created trust relationships are created as part of the dcpromo process. Dcpromo—the process that installs an AD instance and domain controller—can automatically create trust relationships between AD parent and child domains and between the top-level domains of an AD tree and the root domain of the forest. All the other trust relationship types are created explicitly by domain administrators.
All implicitly created AD trust relationships are two-way transitive trust relationships. In other words, running dcpromo automatically defines two trust relationships. Also, in this case each domain is both a trusting and a trusted domain. All explicitly created AD trust relationships can be either one- or two-way trust relationships—depending on the administrators’ decisions.
In Windows Server 2003 (and beginning with Windows 2000), Microsoft simplified trust creation and management by letting you create trusts automatically as part of the domain hierarchy building process and by allowing transitive trust relationships. Before, in NT4 and earlier Windows versions, all trust relationships had to be created manually and were non- transitive.
Transitive means that the trust extends beyond the trusted and the trusting domain. For example, if both the europe.hp.com and the us.hp.com domains trust the hp.com domain, then the europe.hp.com domain implicitly trusts the us.hp.com domain. Transitive trust reduces the number of trusts that are needed for authentication interoperability between different domains. In Figure 3.6, only four trusts are needed (between each parent and child domain) to obtain authentication interoperability between all three domains. In an NT4 setup we would have needed six trust relationships to do the same thing.
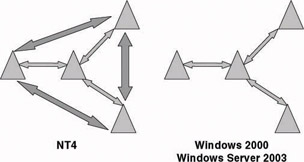
Figure 3.6: Number of trust relationships required in Windows Server 2003 and NT4.
Users working from Windows 2000 or later workstations can see the effect of transitive trusts when they log on. They can choose every domain with which their domain has a direct trust or an indirect trust. An NT 4.0 end user sees only the direct trusts of his or her domain.
Transitive trust is only a logical concept—there is no shared secret between the domain controllers of the domains that share a transitive trust. This means that for authentication to occur between entities on opposite ends of a transitive trust, the authentication process will not flow across the transitive trust but along a path that is known as the trust path. This concept will be explained in more detail in Chapter 5 of this book.
EAN: 2147483647
Pages: 137