Justifying the Need for VLANs
The previous section described the technical definition of a VLAN. This section describes practical answers. In a legacy network, administrators assign users to networks based on geography. The administrator attaches the user's workstation to the nearest network cable. If the user belongs to the engineering department and sits next to someone from the accounting department, they both belong to the same network because they attach to the same cable. This creates some interesting network issues. Discussing these issues highlights reasons for using VLANs. VLANs help to resolve many of the problems associated with legacy network designs. The sections that follow examine the five issues that warrant implementation of a VLAN.
Problem 1: Network Security
The first issue is the shared media nature of legacy networks. Whenever a station transmits in a shared network such as a legacy half-duplex 10BaseT system, all stations attached to the segment receive a copy of the frame, even if they are not the intended recipient. This does not prevent the network from functioning, but software packages to monitor network traffic are readily available and run on a number of workstation platforms. Anyone with such a package can capture passwords, sensitive e-mail (or embarrassing e-mail) and any other traffic on the network.
If the users on the network belong to the same department, this might not be disastrous, but when users from mixed departments share a segment, undesirable information captures can occur. If someone from human resources or accounting sends sensitive data such as salaries, stock options, or health records on the shared network, anyone with a network monitoring package can decode the information.
Neither of these scenarios are constrained to a single segment. These problems can occur in multisegment environments interconnected with routers. In Figure 5-9, accounting resides on two isolated segments. For users on one segment to transmit to users on the other segment, the frames must cross the engineering network. When they cross the engineering segment, they can be intercepted and misused.
Figure 5-9. Security Problems in a Legacy Network
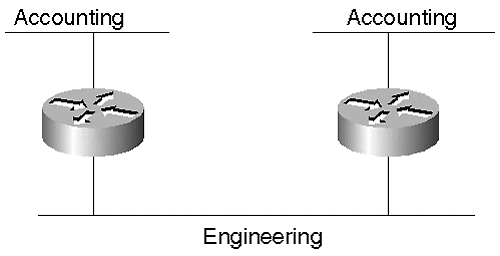
One way to eliminate the problem is to move all accounting users onto the same segment. This is not always possible because there might be space limitations preventing all accountants from sharing a common part of the building. Another reason might be due to geography. Users on one segment might be a considerable distance from users on the other segment. To move the users to a common location might mean moving the employee's household from one city to another.
A second method is to replace accounting with marketing. Who really wants to look at marketing data anyway, except for a good laugh? But accounting cannot distribute pay checks, and marketing tries to get our money. Clearly this is not a good solution.
A third approach is through the use of VLANs. VLANs enable you to place all process-related users in the same broadcast domain and isolate them from users in other broadcast domains. You can assign all accounting users to the same VLAN regardless of their physical location in the facility. You no longer have to place them in a network based upon their location. You can assign users to a VLAN based upon their function. Keep all of the accounting users on one VLAN, the marketing users on another VLAN, and engineering in yet a third.
By creating VLANs with switched network devices, you create another level of protection. Switches bridge traffic within a VLAN. When a station transmits, the frame goes to the intended destination. As long as it is a known unicast frame, the switch does not distribute the frame to all users in the VLAN (see Figure 5-10).
Figure 5-10. A Known Unicast Frame in a Switched Network
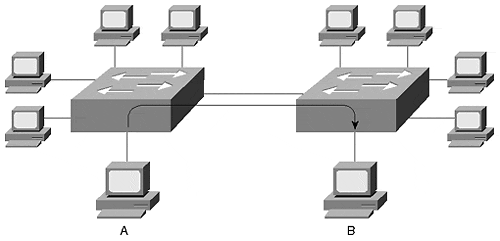
Station A in Figure 5-10 transmitted a frame to Station B attached to another Catalyst. Although the frame crosses through a Catalyst, only the destination receives a copy of the frame. The switch filters the frame from the other stations, whether they belong to a different VLAN or the same VLAN. This switch feature limits the opportunity for someone to promiscuously obtain traffic, thereby increasing the effectiveness of network security. What kind of traffic can be captured? Any traffic flooded within the VLAN is susceptible to capture. Flooded traffic includes broadcast, multicast, and unknown unicast. Note that a Catalyst feature Cisco Group Management Protocol (CGMP), if enabled, can restrict multicast flooding. This is discussed in Chapter 13, "Multicast and Broadcast Services."
Problem 2: Broadcast Distribution
Unfortunately, many, if not all, protocols create broadcasts. Some protocols create more than others. I happen to be particularly fond of Macintosh computers. Network administrators, however, despise AppleTalk due to the amount of broadcast traffic it generates. Every ten seconds, AppleTalk routers send routing updates that are broadcast frames in the network. Broadcasts go to all devices in the broadcast domain and must be processed by the receiving devices.
Other protocols share in the guilt. NetBEUI creates many broadcast frames, even when stations perform few network activities. TCP/IP stations create broadcasts for routing updates, ARP, and other processes. IPX generates broadcasts for SAP and GNS frames.
To add to the mix, many multimedia applications create broadcast and multicast frames that get distributed within a broadcast domain.
Why are broadcasts bad? Broadcasts are necessary to support protocol operations and are, therefore, overhead frames in the network. Broadcast frames rarely transport user data. (The exception might be for multimedia applications.) Because they carry no user data, they consume bandwidth in the network, reducing the effective available bandwidth for productive transfers.
Broadcasts also affect the performance of workstations. Any broadcast received by a workstation interrupts the CPU preventing it from working on user applications. As the number of broadcasts per second increases at the interface, effective CPU utilization diminishes. The actual level of degradation depends upon the applications running in the workstation, the type of network interface card and drivers, the operating system, and the workstation platform.
Tip
If broadcasts are a problem in your network, you might mitigate the effect by creating smaller broadcast domains. This was described in Chapter 2. In VLANs, this means creating additional VLANs and attaching fewer devices to each. The effectiveness of this action depends upon the source of the broadcast. If your broadcasts come from a localized server, you might simply need to isolate the server in another domain. If your broadcasts come from stations, creating multiple domains might help to reduce the number of broadcasts in each domain.
Problem 3: Bandwidth Utilization
When users attach to the same shared segment, they share the bandwidth of the segment. The more users that attach to the shared cable means less average bandwidth for each user. If the sharing becomes too great, user applications start to suffer. You start to suffer too, because users harass you for more bandwidth. VLANs, which are usually created with LAN switch equipment, can offer more bandwidth to users than is inherent in a shared network.
Each port in a Catalyst behaves like a port on a legacy bridge. Bridges filter traffic that does not need to go to segments other than the source. If a frame needs to cross the bridge, the bridge forwards the frame to the correct interface and to no others. If the bridge (switch) does not know where the destination resides, it floods the frame to all ports in the broadcast domain (VLAN).
Note
Although each port of a Catalyst behaves like a port on a bridge, there is an exception. The Catalyst family has group switch modules where ports on the module behave like a shared hub. When devices attach to ports on this module, they share bandwidth like a legacy network. Use this module when you have high density requirements, and where the devices have low bandwidth requirements, yet need connectivity to a VLAN.
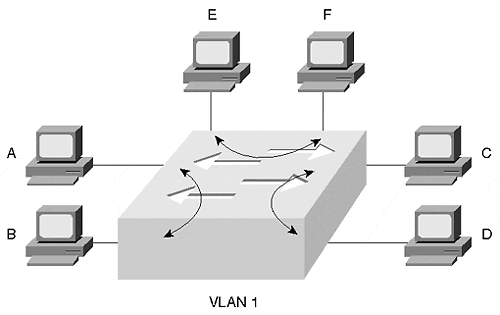
In most normal situations, then, a station only sees traffic destined specifically for it. The switch filters most other background traffic in the network. This allows the workstation to have full dedicated bandwidth for sending and/or receiving frames interesting traffic.Unlike a shared hub system where only one station can transmit at a time, the switched network in Figure 5-11 allows many concurrent transmissions within a broadcast domain without directly affecting other stations inside or outside of the broadcast domain. Station pairs A/B, C/D, and E/F can all communicate with each other without affecting the other station pairs.
Figure 5-11. Concurrent Transmissions in a Catalyst
Problem 4: Network Latency from Routers
In the legacy network of Figure 5-9, accounting users on the two segments had to cross the engineering segment to transfer any data. The frames had to pass through two routers. Older software-based routers tend to be comparatively slower than other internetworking products such as a Layer 2 bridge or switch. As a frame passes through a router, the router introduces latency the amount of time necessary to transport a frame from the ingress port to the egress port. Every router that the frame transits increases the end-to-end latency. Further, every congested segment that a frame must cross increases latency. By moving all of the accounting users into one VLAN, the need to cross through multiple routers and segments is eliminated. This reduces latency in a network that might improve performance for your users, especially if they use a send-acknowledge protocol. Send-acknowledge protocols do not send more data until an acknowledgement is received about the previous data. Network latency dramatically reduces the effective throughput for send-acknowledge protocols. If you can eliminate the need for user traffic to pass through a router by placing users in the same VLAN, you can eliminate cumulative router latency. If frames must pass through routers, enabling Layer 3 switching reduces router transit latencies, too.
VLANs help to reduce latency by reducing segment congestion. This can be a dramatic improvement if the workstations' connections originally attached to congested shared segments and the workstations' new connections all have dedicated switch ports.
Problem 5: Complex Access Lists
Cisco routers allow administrators to introduce policies controlling the flow of traffic in the network. Access lists control traffic flow and provide varied degrees of policy granularity. Through the implementation of access lists, you can prevent a specific user from communicating with another user or network, or you can prevent an entire network from accessing a user or network. You might exercise these capabilities for security reasons, or you might elect to prevent traffic from flowing through a segment to protect local bandwidth.
In any case, the management of access lists is cumbersome. You must develop the access list according to a set of rules designed by Cisco for the access list to correctly filter traffic.
In the network example of Figure 5-9, filters in the routers attached to the engineering segment can include access lists allowing the accounting traffic to pass through the engineering segment, but to never talk to any engineering devices. That does not prevent engineers from monitoring the traffic, but does prevent direct communication between the engineering and accounting devices. Accounting never sees the engineering traffic, but engineering sees all of the accounting transit traffic. (Accounting yells, "That hardly seems fair!")
VLANs can help by allowing you to keep all accounting users in one VLAN. Then their traffic does not need to pass through a router to get to peers of the VLAN. This can simplify your access list design because you can treat networks as groups with similar or equal access requirements.
Wrong Motives for Using VLANs
One common motivation for using VLANs tends to get network administrators excited about VLANs. Unfortunately, reality quickly meets enthusiasm revealing errors in motivation. The advent of VLANs led many to believe that life as a network administrator would simplify. They thought that VLANs would eliminate the need for routers, everyone could be placed in one giant flat network, and they could go home at 5:00 PM each evening like everyone else in their office. Wrong. VLANs do not eliminate Layer 3 issues. They might allow you to more easily perform some Layer 3 tasks such as developing simpler access lists. But Layer 3 routing still exists.
If anything, VLANs make networks more complex due to the introduction of the Spanning-Tree Protocol in the system and the dispersed nature of broadcast domains. Spanning Tree (discussed in Chapters 6 and 7) adds additional background traffic to your network by flooding "hello packets" (BPDUs) throughout the system every two seconds. Although hello messages do not consume significant bandwidth on segments, it does make use of a network analyzer more challenging. You might need to filter out the hello messages to find the interesting traffic that you are trying to troubleshoot. A more significant Spanning Tree element making VLANs complex is the selection of a Root Bridge. Spanning Tree participants elect a Root Bridge around which the rest of the network revolves. Depending upon the location of the Root Bridge in the network, traffic flow might not always pass through the most desirable links. Traffic might flow through less desirable links with lower bandwidth or might require more hops to reach the destination. The network administrator might need to tweak Spanning Tree default values to select a more appropriate Root Bridge. The default selection of a root bridge is not arbitrary, but is based upon the MAC address of the bridge. The bridge with the lowest MAC address becomes the Root Bridge. This means the Root Bridge selection is repeatable every time the system powers up, as long as no other bridges are introduced to the system with a lower MAC address, or other default values are changed. See Chapters 6 and 7 for more detailed information.
This discussion does not imply that you should not use VLANs. Rather, it raises the point that you need to consider not just why, but also how you plan to deploy VLANs. All networks are candidates for VLANs and switches. Your network might have one VLAN with switches, but it is still a VLAN. However, you should consider limiting the size or extent of the VLAN. As mentioned, a single VLAN extending throughout the entire network usually defies practicality and scalability. Smaller VLAN islands interconnected with Layer 3 devices typically deploy much more easily in a large scale, while allowing you to take advantage of Layer 2 VLANs within a workgroup area.
EAN: N/A
Pages: 223