Chapter 10. Securing and Sharing Information
10. Securing and Sharing InformationChapter at a Glance 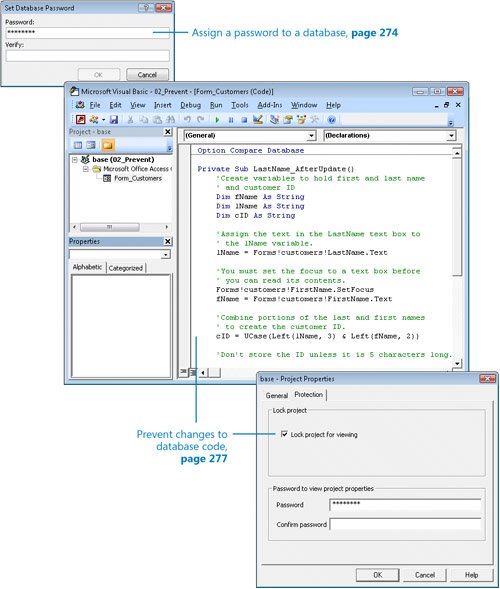
The need for database security is an unfortunate fact of life. As with your house, car, office, or briefcase, the level of security required for your database depends on the value of what you have and whether you are trying to protect it from curious eyes, accidental damage, malicious destruction, or theft. The security of a company's business information can be critical to its survival. For example, you might not be too concerned if a person gained unauthorized access to your products list, but you would be very concerned if a competitor managed to seeor worse, stealyour customer list. And it would be a disaster if someone destroyed your critical order information. Your goal as a database developer is to provide adequate protection without imposing unnecessary restrictions on the people who should have access to your database. The type of security required to protect a database depends to a large extent on how many people are using it and where it is stored. If your database will never be opened by more than one person at a time, you don't have to worry about the potential for corruption caused by several people trying to update the same information at the same time. If your database is sold outside of your organization as part of an application, you will want to take steps to prevent it from being misused in any way. Tip In previous versions of Access you could set up workgroups and assign permissions to restrict the information available to members of each group and the actions they can perform. Access 2007 doesn't offer this feature. Another way to protect a database is by securing the distribution channel; for example, by making it available from a password-protected Web site. In this chapter, you will explore ways to protect data from accidental or intentional corruption, and ways to make it difficult for unauthorized people to gain access to private information. Then you will learn about ways of sharing databases among team members and backing up a shared database. See Also Do you need only a quick refresher on the topics in this chapter? See the Quick Reference entries on pages xxxixlxv. Important
Troubleshooting Graphics and operating systemrelated instructions in this book reflect the Windows Vista user interface. If your computer is running Microsoft Windows XP and you experience trouble following the instructions as written, please refer to the "Information for Readers Running Windows XP" section at the beginning of this book. | ||||||||||