Understanding Encryption
|
|
Occasionally company data has to be sent over public networks, such as the Internet, and just about anyone with the desire to do so (including a company’s competitors) can view the data in transit. Companies that want to ensure that their data is secure during transit encrypt their data before transmission. Encryption is the process that encodes and decodes data. The encrypted data is sent over the public network and is decrypted by the intended recipient. Generally speaking, encryption works by running the data (represented as numbers) through a special encryption formula (called a key). Both the sender and the receiver know the key. The key, generally speaking, is used to encrypt and decrypt the data.
The NSA has classified encryption tools and formulas as munitions since 1979 and therefore regulates them. The agency is concerned that unfriendly nations, terrorists, and criminals will use encrypted communications to plan crimes and go undetected. You can export weak encryption methods, but they cannot compete commercially with the tools designed overseas.
One way to measure an encryption algorithm is by its bit strength. Until 1998, only software with 40-bit strength and less could be exported. That limit has been increased to 56-bit, then 128-bit by special consideration of the U.S. Department of Commerce.
| Note | To ensure the security of monetary transfers, the NSA allows U.S. banks to use more secure encryption methods. Banks need to communicate with their overseas branches, customers, and affiliates. |
Uses for Encryption
In internal networks, some encryption is necessary, such as encrypting passwords that are being sent from workstation to server at login. This is done automatically by many modern network operating systems. Some older network utilities such as FTP and Telnet don’t have the ability to encrypt passwords. Encryption is also used by many e-mail systems, giving the user the option to encrypt individual or all e-mail messages. Third-party software packages, such as PGP, can provide data encryption for e-mail systems that don’t natively have the ability to encrypt. Encryption is also used for data transmission over VPNs, using the Internet to connect remote users securely to internal networks. Finally, encryption has become important with the advent of e-commerce, online banking, and online investing. Buying products and handling finances online would not be possible if the data sent between all involved parties over the Internet were not encrypted.
How Encryption Works
The encryption process involves taking each character of data and comparing it against a key. For example, you could encrypt the following string of data in any number of ways:
The quick brown fox
For sample purposes, let’s use a simple letter-number method. In this method, each letter in the alphabet corresponds to a particular number. (You may have used this method as a kid when you got a decoder wheel in your Cracker Jack or breakfast cereal box.) If you use a straight alphabetictonumber encryption (for example, A=1, B=2, C=3, and so on), the data translate into the following:
20 8 5 17 21 9 3 11 2 18 15 23 14 6 15 24
You can then transmit this series of numbers over a network, and the receiver can decrypt the string using the same key in reverse. From left to right, the number 20 translates to the letter T, 8 to H, 5 to E, and so on. Eventually, the receiver gets the entire message:
The quick brown fox
Most encryption methods use much more complex formulas and methods. Our sample key was about 8 bits long; some keys are extremely complex and can be a maximum of 128 bits. The larger the key (in bits), the more complex the encryption—and the more difficult it is to crack.
Encryption Keys
To encode a message and decode an encrypted message, you need the proper encryption key or keys. The encryption key is the table or formula that defines which character in the data translates to which encoded character. Encryption keys fall into two categories: public and private. Let’s look at how these two types of encryption keys are used.
Private Key Encryption
Private keys are known as symmetrical keys. In private key encryption technology, both the sender and receiver have the same key and use it to encrypt and decrypt all messages. This makes it difficult to initiate communication the first time. How do you securely transmit the single key to each user? You use public keys, which we’ll discuss shortly.
The Data Encryption Standard (DES)
International Business Machines (IBM) developed one of the most commonly used private key systems, DES. In 1977, the United States made DES a government standard, defined in the Federal Information Processing Standards Publication 46-2 (FIPS 46-2).
DES uses lookup table functions and is incredibly fast when compared with public key systems. A 56-bit private key is used. RSA Data Systems issued a challenge to break the DES. Several Internet users worked in concert, each tackling a portion of the 72 quadrillion possible combinations. The key used in RSA’s challenge was broken in June 1997, after searching only 18 quadrillion keys out of the possible 72 quadrillion. The plain text message read: “Strong cryptography makes the world a safer place.”
Skipjack and Clipper
The replacement for DES might be the NSA’s recent algorithm called skipjack. Skipjack is officially called the Escrowed Encryption Standard (EES), defined in FIPS 185, and uses an 80-bit key rather than the DES 56-bit key. The functions and complexity of each algorithm are different as well. Skipjack was supposed to be integrated into the clipper chip.
A clipper chip is a hardware implementation of skipjack. Clipper chips were proposed for use in U.S. telephone lines, but many civil liberties and privacy activists became upset because the U.S. government would be able to decrypt secure telephone conversations.
Public Key Encryption
Public key encryption, or a Diffie-Hellman algorithm, uses two keys to encrypt and decrypt data: a public key and a private key. The receiver’s public key is used to encrypt a message to the receiver. The message is sent to the receiver who can then decrypt the message using the private key. This is a one-way communication. If the receiver wants to send a return message, the same principle is used. The message is encrypted with the original sender’s public key (the original sender is now going to be the receiver of this new message) and can only be decrypted with his or her private key. If the original sender does not have a public key, a message can still be sent with a digital certificate (also sometimes referred to as a digital ID). The digital ID verifies the sender of the message.
Figure 8.7 shows public key–encrypted communication between two people, User X and User Y.
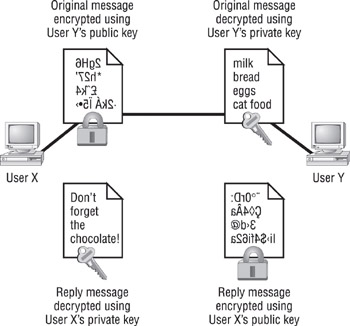
Figure 8.7: Public key encryption
| Note | The term Diffie-Hellman refers to all public key algorithms. Whitfield Diffie and Martin Hellman from the Stanford Research Institute invented public key encryption. They introduced the dual key concept in their 1976 paper, “New Directions in Cryptography.” |
RSA Data Security
Rivest, Shamir, and Adleman (RSA) encryption is a public key encryption algorithm named after the three scientists from the Massachusetts Institute of Technology (MIT) who developed it. They created a commercial company in 1977 to develop asymmetric keys and received several U.S. patents. Their encryption software is used in several products today, including Netscape Navigator and Novell’s latest NetWare Client.
| Note | For more information on RSA Data Security, go to www.rsa.com. |
Pretty Good Privacy (PGP)
PGP is an encryption utility based on public key encryption. In the early 1990s, Phil Zimmerman, also from MIT, wrote the majority of the code for this freely available version of public key encryption. The software was designed to encrypt data for e-mail transmission. Zimmerman compared e-mail to postcards. As the e-mail message is passed from server to server on the Internet, anyone can read it, just as anyone can read a postcard as it travels through the postal service. He compared an encrypted message to a letter mailed inside an envelope.
Zimmerman distributed the software for personal use only and restricted commercial use. The name PGP denotes that nothing is 100-percent secure. Both RSA Data Security and the U.S. federal government had problems with Zimmerman’s product. RSA complained about patent infringement (a license fee is now paid to RSA). The government decided to prosecute Zimmerman for exporting munitions grade software; however, the charges were eventually dropped. Many years later, PGP and other public key– related products are readily available.
|
|