Introduction
|
It seems that since the beginning of time, as we human beings multiplied across this earth, there has been a division between the "haves" and the "have-nots." In the days of the hunter-gatherers, through the agricultural period, industrial period, and right into our information period approaching the knowledge age, there have always been people who threatened others. Some wanted food without hunting for it; others wanted material possessions of others without working for it; and others wanted power, fortune, and glory without earning it.
Throughout the ages, humans have used technology for good and for bad purposes:
-
Fire can be used for cooking and heating, or it can be used to burn down someone's home or crops;
-
Guns can be used to kill game and defend one's family, or they can be used to kill others and take what they own; and
-
Computers can be used to help find medical cures, or they can be used to break into other computers to destroy, modify, or steal others' information.
There are many examples of the utilization of all types of technology that can be used for good or bad purposes. However, they all have something in common. People are the driving force behind it all, and it is people as threat agents that the ISSO must always take into account when building a Corporate Information Assets Protection Program (CIAPP).
For our purposes, we will look at the various categories of threats to information and information systems in this our age of information. In order to discuss threats, we must look at them in the context of the overall triad of threats, vulnerabilities, and risks.
-
declaration of intent to cause harm: the expression of a deliberate intention to cause harm or pain;
-
indication of something bad: a sign or danger that something undesirable is going to happen;
-
somebody or something likely to cause harm: a person, animal, or thing likely to cause harm or pain
Threats to our information and the systems that store, process, display, and transmit that information fall into two basic categories: manmade or natural occurrences that can cause adverse affects to systems and information when combined with specific vulnerabilities. For example:
-
Natural threats include such things as fire, floods, hurricanes, and earthquakes.
-
Man-made threats or threat-related matters include such things as unauthorized system access, hacker/cracker/phreaker programs, the perpetrators themselves, theft of systems or services, denial of services, and destruction of systems or information.
Vulnerabilities are defined basically as weaknesses that allow specific threats to cause adverse affects to systems and information. For example:
-
Lack of current antivirus software;
-
Lack of systems access controls; or
-
Generally anything that weakens the security of the systems and the information they process, store, display, and transmit.
The chances that a specific threat can take advantage of a specific vulnerability to cause adverse affects to systems and information is known as risk. For example:
-
If you live in a strong earthquake area, what are the chances that your systems will be damaged in the event of a strong earthquake?
-
If you do not have audit trails on your system, how will you know if someone tries to penetrate your system, or worse yet, whether or not they succeed?
When one looks at the threats to information and their associated systems, the vulnerabilities of that protection system and their associated risks, one tries to assess or evaluate the level of risk to systems and their associated information. Assessments are usually done through a qualitative or quantitative analysis, or a combination of the two. It is the measurement of risks:
-
Qualitative analysis usually uses the three categories of risk, that is, high, medium, and low. It is an "educated best guess" based primarily on opinions of knowledgeable others gathered through interviews, history, tests, and the experience of the person doing the assessment.
-
Quantitative analysis usually uses statistical sampling based on mathematical computations determining the probability of an adverse occurrence based on historical data. It is still an "educated best guess," but primarily based on statistical results.
The proliferation in the use of computer and communications technologies over approximately the last 20 years has resulted in significant changes in the types of threats that are posed to the information environment that we have come to rely on. The way in which the threats that are posed to an information environment are measured has not advanced at the same rate as the technology has developed and as a result, has not yet transitioned from being an art to science.—Andy Jones [3]
This leads us to risk management. Risk management is defined as the total process of identifying, controlling, and eliminating or minimizing uncertain events that may affect system resources. It includes risk assessments; risk analyses, including cost-benefit analyses; target selection; implementation and testing; security evaluation of safeguards; and overall InfoSec review. The process of identifying InfoSec risks, determining their magnitude, and identifying areas needing safeguards is called risk assessment. In other words, you are assessing the risk of a particular target, such as a new software application's impact on the system's security processes, architecture, etc. The risk assessment process is subdivided into threats, vulnerabilities, and risks.
Analyses of the risks, the countermeasures to mitigate those risks, and the cost-benefits associated with those risks and countermeasures make up the risk analysis process. Basically, it is risk assessment with the cost and benefit factors added.
If I want to wreak havoc on a society that, in some cases, has become complacent, I am going to attack your quality of life. —Curt Weldon, R-PA, U.S. House Armed Services Committee[4]
Types of Threats
As an ISSO, you must become extremely familiar with the types of threats that may adversely affect the information and associated systems—the information environment for which you are responsible—as well as the details of each threat. Furthermore, you must understand how to mitigate each threat. As mentioned earlier, threats include but are not limited to employees, terrorists, techno-fraudsters, Netspionage agents, information warriors, other miscreants, a combination of these, or such things as malicious software programs. These threats are often called threat agents.
Natural Threats
Natural threats, as the name implies, are acts of nature. Some may call them "acts of God"; however, that is a personal choice. Since we are discussing information and systems protection, we won't delve into discussing whether or not God plays a role in threatening our information and our systems.
Although natural threats may seem to be random acts, often historical records and interviews with experts will help the ISSO determine if any type of pattern can be identified. If so, the data can be analyzed and a determination can be made as to the extent of risk based on the identified pattern. Defensive measures can then be employed to mitigate that risk. For example, if one lives in a region where there are hurricanes or typhoons, one can talk to meteorologists and review historical records. That review can help the ISSO determine a pattern and thus determine the amount of risk based on that specific threat. The ISSO would, for example, want to know:
-
How often a hurricane or typhoon strikes the area;
-
What were the maximum, minimum, and average wind speeds, damage, and rainfall associated with such storms;
-
What time of year they usually occur; and
-
What the impact in the past has been to the company's facilities and information systems.
Such information on this type of threat can assist the ISSO in mitigating the threats at least cost, based on how much risk the company's management would want to assume. By the way, as an ISSO, remember that you are the in-house consultant on such matters. Risk taking and risk-taking decisions are the purview of company management. As an ISSO, you provide them expert opinion and recommendations, but under no circumstances should you make the final risk decision. That is why they "make the big bucks." Risk management decisions may be pushed on you; however, don't fall for that ploy, as it is management's way of getting out of their company responsibilities. Furthermore, if something occurs, based on the risk accepted, that damages the protection of company information and systems, at least management knew the risks.
You will find that management is averse to taking risks but will do so to save money—usually to the detriment of InfoSec. Make no mistake, you probably will still be blamed even if they do not take your recommendation; therefore, it is imperative that such decisions be formally documented and the risks acknowledged in writing by the manager assuming the risks. You may still lose your job if something fails; however, your chances of winning a "wrongful discharge" lawsuit may be enhanced. Such is the life of an ISSO.
The other natural threats based on the physical locations of your company's information systems, such as fire and earthquakes, can be dealt with in a similar manner.
Andy Jones, a security and assets protection expert looks at natural threats and accidents as follows [5]:
For this group of threat agents, which includes fire, wind, water, earthquake, and accidental damage, each element will need to be considered in isolation as they have only tenuous links to each other and the main area of commonality is that they are not planned or directed.
Fire. The likelihood of a direct effect on a system from fire is easily calculable and there is considerable experience and documented case histories in the insurance industry of underwriting this type of event.
Wind. The possibility of damage from wind is largely geographically dependent, as some locations are far more prone to wind damage than others. Again there is considerable experience and documented case histories in the insurance industry of underwriting this type of event.
Water. The likelihood of a direct effect on a system from water is easily calculable and there is considerable experience and documented case histories in the insurance industry of underwriting this type of event.
Earthquake. The possibility of damage from an earthquake is also largely geographically dependent, but again there is considerable experience and documented case histories in the insurance industry of underwriting this type of event.
Accidents. The threat to a system from accidental misuse or damage is very different from the other categories in this group, as it will be affected over time by the attitude and disposition of the staff in addition to the environment. What separates this from the malicious threats is the absence of malice or motivation. Again, this threat is well understood and the probability of such an event occurring can be reasonably predicted from actuarial data.
It is possible that more than one of these natural threats will affect a system at the same time or shortly after each other. An example of this might be an earthquake that is followed by a fire as a result of the disruption to the gas or electrical services that the initial event caused.
Natural Threat Agent. The "threat agent" element expands into the types of agent that may be seen. These have, for convenience and because they can be dealt with in two very different ways, been subdivided into two different groups, the natural threat agents and the malicious threat agents (See Figure 3.1).
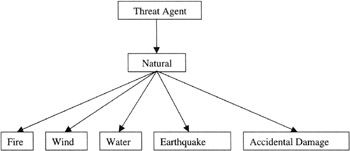
Figure 3.1: The components of the natural threat agents.These are a relatively well-understood set of threats and there is actuarial history for the effects of Fire, Wind, Water, and Earthquake components that is based on long established experience within the insurance industry. For the last of components, accidental damage, there is also a wealth of information available with regard to the likelihood of an incident occurring in the physical domain (e.g., someone dropping a piece of equipment).
Unfortunately there is little or no documented information available for incidents that have occurred in the electronic environment, so little obvious benefit can be gained from any past experience in the domain.
Human Error—Accidents
As noted above, Professor Jones includes accidents under the "Natural" category. Surprisingly, many ISSOs don't consider the threats caused by human error: accidents. Being human, we naturally will make mistakes. So, does human error fall under the category of natural threats, and are we humans as users of systems to be categorized as natural threat agents? Or do we fall under the category of "manmade" threats? There is no law or rule that says that you as an ISSO must treat accidents as one, the other, both, or neither. However, human error is a threat to information and systems, and as such should undoubtedly be considered as such by an ISSO—and dealt with accordingly.
As an ISSO, you may look at such a threat as one that falls into the category of "sh*t happens," and there is no way to mitigate or plan for such occurrences. However, that is not true. Let's look at an example: Some employees install their own software, causing systems problems; modify group files; accidentally delete files; and do other things that affect information systems protection. Processes can be developed and put in place to mitigate such threats. For example, employees can be trained on installing software, or trained experts can be designated to do it for them.
So, yes accidents happen, but most accidents that are serious threats to the protection of information and systems can be mitigated. One or more studies or surveys taken over the years and lost in time (at least lost in time to the author) have indicated that human errors have a greater impact on information and systems protection than do manmade threats caused by purposeful attacks. As an ISSO, be sure to consider human error threats when developing a Corporate Information Assets Protection Program (CIAPP).
Manmade or Malicious Threats
Manmade or malicious threats take many forms, with new types of threats being identified on what it seems to be almost a weekly basis. However, these threats can all be categorized into general groupings. Again quoting Andy Jones's paper on threats:
In order for a malicious threat to exist, there must be an agent that will implement the threat and that agent must have the motivation to carry it out, the capability and the opportunity to do so.
Capability. The capability of an organization or an individual to mount an attack and to sustain it at an effective level will vary with the complexity, resources, and sophistication of both the attacking force and of the target. It may be sufficient for an attacker to mount an attack at any level in order to achieve their objective, but it may also require a high level of processing power over a long period to have a significant effect.
Motivation. The motivation to carry out a malicious attack on a system could rise from any number of situations. Some commonly accepted motivational drivers are: political, secular, personal gain, religious, revenge, power, terrorism, curiosity, and the like.
Access. In order for a threat agent to carry out an attack on an information system, they must have either physical access to the system (the threat agent gaining direct access to the system) or electronic access (via other networks). Without this, an attack cannot be initiated.
Catalyst. A catalyst is required to cause a threat agent to select the target and the time at which the attack will be initiated. The catalyst could be something that affects either the target or the threat agent.
Inhibitors. There are a number of factors (affectors) that will inhibit a threat agent from mounting an attack either on a specific target or at a specific time. Again, these may affect either the target or the threat agent. An example of this may be the perception that the target system is well protected and that any attempt to attack it will be quickly detected.
Amplifiers. There are a number of factors (affectors) that will encourage a threat agent to mount an attack at a specific time against a particular target. Again, these may affect either the target or the threat agent. An example of this may be the perception that the target system is not well protected and that an attempt to attack it will not be detected.
System-Related Factors
In order for a threat agent to mount a successful attack on a system, there are at least two system-related factors that must be present.
The first is that there must be an exploitable vulnerability in the system for the threat agent to utilize in order to have an effect. For a vulnerability to be exploitable, it must be known (or there must be an expectation that it will be known) to the threat agent, and the threat agent must have sufficient access to the system to affect the attack. The vulnerability may exist in the hardware, the operating system software, or the applications software.
The second is that the target system must be important enough to the organization that its loss or degradation in its availability, confidentiality, or integrity would have an impact on the business process of the organization.
Relationship of Threat Elements
The potential for a threat agent to pose an actual threat to an information infrastructure will be influenced by a number of factors. In reality, for the threat agent to pose a real threat to an information infrastructure, the agent must posses a capability and must also be able to gain either physical or electronic access.
The potential impact of such a threat agent will be influenced by its level of capability. The threat agent will be inhibited by factors that hinder their ability to form a threat and will be strengthened by other factors. In addition, there will be some type of catalyst that will cause them to act, depending on their motivation. The components of "threat" that apply to a malicious threat and their interrelationships are detailed in Figure 3.2.
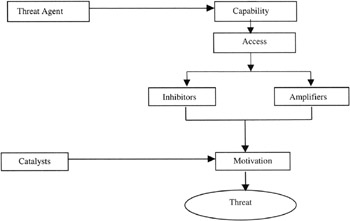
Figure 3.2: The threat components and their relationships.
Malicious Threat Agent
Malicious Threat Agents expand into at least seven components (See Figure 3.3).
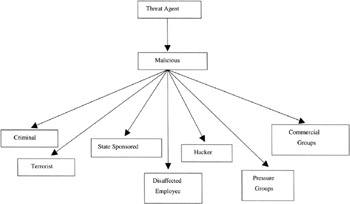
Figure 3.3: The components of the malicious threat agent.
A malicious threat agent can be generated from any number of groups. This is not meant to be an exhaustive list of potential sources or groupings of malicious threat agents, as these will change over time as technology, education, national and international politics, cultural, and a host of other factors have an effect.
Capability
In order for a malicious threat agent to be effective, they must have the capability to conduct and sustain an attack. The constituent elements of "capability" are detailed in Figure 3.4.
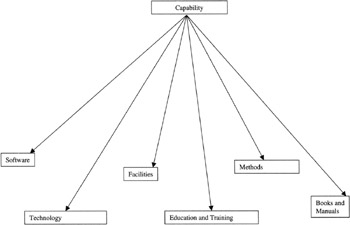
Figure 3.4: The components of capability.
For a malicious threat agent to be able to carry out an attack, they must have the means and the necessary skills and methods to be successful. They must also, in some cases, have a sustainable depth of capability in order to achieve their aims.
Inhibitors
There are several factors that both inhibit and assist a malicious threat agent in perpetrating a successful attack. These have been labeled as inhibitors and amplifiers. The inhibitors are identified in Figure 3.5.
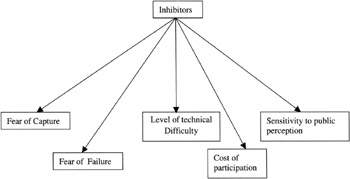
Figure 3.5: The components of inhibitors.
An inhibitor will either prevent a threat agent from carrying out a successful attack, minimize the impact that a successful attack will have, or reduce the inclination of a threat agent to initiate an attack. The fear of being captured as a result of conducting an attack may well act as a sufficient deterrent to the threat agent and cause it to decide not to carry out the attack. If the threat agent perceives that its peers, or indeed the public, will hold it in contempt for attempting the attack (for example if the target was a hospital or a charity), this may be sufficient to inhibit the attack. Also, if the level of technical difficulty that the threat agent encounters is sufficiently high, the threat agent may decide that the investment of effort required to carry out the attack is not worth it.
Amplifiers
The types of affectors that will amplify or increase the possibility of a successful attack are varied, but include factors such as peer pressure. In this amplifier, the threat agent desires to be well regarded by their peers. Their desire to gain the recognition and respect of their peers through the demonstration of their skills strengthens their resolve to carry out the attack. The level of education and skill that an agent possesses, or can gain access to, will improve the confidence of a threat agent and also increase the likelihood of success. Access to the information that the agent needs in order to mount an attack, in terms of information on the target, other relevant information systems, organizations or in terms of programming scripts and tools that can be run to conduct an attack, will also increase the possibility of a successful attack.
Catalysts
The causal factor in a threat agent deciding if and when to carry out an attack on an information system may be a result of an event, such as publicity for an organization with which the agent has a disagreement, or perhaps the start of an armed conflict between the agent's country and an opponent. Another factor may be the circumstances of the agent and any change (perhaps in location, social grouping, or employment status) may affect their ability or desire to carry out an attack.
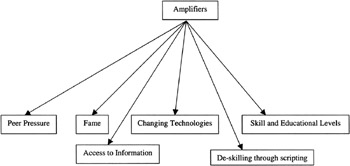
Figure 3.6: The components of amplifiers.
An attack may also be triggered by the advent of a new technology which makes what was previously not achievable a possibility. (See Figure 3.7.)
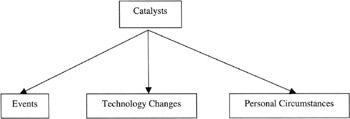
Figure 3.7: The components of catalysts.
Motivation
The motivation of the threat agent is a subjective area that is influenced by a wide range of factors dependent on the grouping from which the threat agent originates. The components that are shown above are not intended to be a comprehensive list of motivational factors, but rather to give an indication of the range of drivers that may have an influence. In some cases a number of these drivers will act together to influence the threat agent. (See Figure 3.8.)
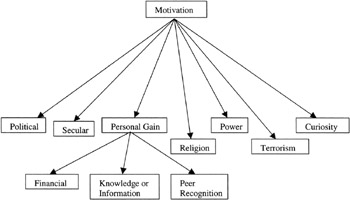
Figure 3.8: The components of motivation.
Malicious Threat Agent—State Sponsored
State sponsored malicious threats may take the form of denial of service attacks on financial systems or critical national infrastructures in order to modify public perception, or cause instability in the target country and prevent it from taking other actions. It may also take the form of espionage or industrial espionage[6]. A characteristic of this group is that it will be risk-averse and conservative in its actions, taking great efforts to evade identification.
Information on nation states is, in the main part readily available from open sources. The limiting factor in this is that by its nature, the information may be dated and the elements useful for the purposes of determining a nation's readiness to mount an attack may be limited.
For an attack sponsored by a nation state to be effective, it would require sufficient technology available to mount the attack, telecommunications, Internet connectivity, and power supplies to allow the attack to take place and be sustained, and sufficient personnel resources with adequate levels of education and skill to mount and maintain the attack. Each country will have specific cultural drivers.
A threat agent that is sponsored by a nation state may have the objective of preventing or reducing access to information systems (denial of service), manipulating or corrupting information (disinformation), or gaining access to information (espionage). The impact that each of these types of attack will have varies, and the likelihood of each must be considered separately.
Malicious Threat Agent—Terrorists
Terrorist activity may be linked to criminal activity and as a malicious threat agent, the terrorist may operate in both groups. Terrorism requires funding to be effective. Given that terrorists operate outside of the normal national and international laws, it is common for them to resort to criminal activity to generate funds to support their activities, in addition to any direct terrorist related action. Direct terrorist activities may include the publication of propaganda, communications, or attacks on systems to either influence the public, users, or owners of a system, or to prevent the system from operating. For example, this includes causing the electrical supply system in a city to fail and gaining the desired effect from the ensuing chaos.
Qualitative information on terrorist organizations is not readily available from open sources. While generic information from external sources is available, accurate and in-depth information is not normally available in a verifiable form except where it is released or disseminated from national resources that will probably be hostile to the terrorist organization.
For a terrorist sponsored attack to be effective, it would require sufficient technology available to mount the attack, telecommunications, Internet connectivity, and an adequate power supply to allow the attack to take place. If one of the required outcomes is a sustained attack, then they must also have sufficient depth of personnel resources with adequate levels of education and skill available to mount and maintain the attack. Each terrorist group will have specific drivers. These may be religious, cultural, ethnic, political, or any number of others.
A terrorist threat agent is most likely to have the objective of preventing or reducing access to information systems (denial of service), and this should be the area that is further investigated.
Malicious Threat Agent—Pressure Group
Pressure groups will tend to have a specific focus or cause that they support and wish to further the aims of. Recent history has shown that such groups, whether secular or religious, have learned they can achieve results by exerting influence on peripheral targets, rather than on a direct attack on the primary target.
Qualitative information on pressure groups is not, for the main part, readily available in the public domain from open sources. While generic information from external sources will be available, accurate and in-depth information is not normally available in a verifiable form, as these are not accountable organizations.
For an attack sponsored by a pressure group to be effective, it would require that the necessary technology was available to mount the attack. It is assumed there would be telecommunications, Internet connectivity, and an adequate power supply to allow the attack to take place. If the required outcome is a sustained attack, then the pressure group must also have sufficient personnel resources with adequate levels of skill available to mount and maintain the attack. Each pressure group will have specific drivers that may be religious, cultural, ethnic, political, or any number of others.
Due to the range of organizations that are included in this group and the fact that they have varying degrees of legitimacy and history, identifying specific sources of information for the various aspects of pressure groups cannot easily be documented. For detailed information on a specific pressure group, it would be necessary to look at the information sources that were specifically related to that group. Details that are available on a pressure group will vary over time as it becomes more or less active.
Pressure groups are affected by a wide range of factors that influence their motivation, ability, and likelihood of them carrying out an attack. A threat agent sponsored by a pressure group may have the objective of preventing or reducing access to information systems (denial of service), manipulating or corrupting information (disinformation), or gaining access to information ([industrial] espionage). The impact that each of these types of attack will have varies, and the likelihood of each must be considered separately in the light of the aims of the pressure group and its target.
Malicious Threat Agent—Commercial Group
A threat agent that acts on behalf of a commercial group will tend to have one of a small number of objectives. These will range from industrial espionage, to damaging the interests of competitors, to influencing small nation states. A characteristic of this group is that it will be risk averse and conservative in its actions, taking great efforts to evade identification. Qualitative information on the capability of a commercial organization to carry out an attack is not, for the main part, available in the public domain from open sources. While very specific and detailed information will be available on a number of aspects relating to the commercial concern, specific information with regard to its capability to pose an information threat will only be generated from analysis of the organization, or from information on past activity that becomes available.
For an attack sponsored by a commercial organization to be effective, it would require sufficient technology and available resources. It is assumed that there would be telecommunications, Internet connectivity, and an adequate power supply to allow the attack to take place. If the required outcome is a sustained attack, then the organization must also have sufficient personnel resources with adequate levels of skill available to mount and maintain the attack. The driver for a commercial organization to mount an information attack will be to gain a commercial advantage in the marketplace, either by gaining information on or from its competitors, or by reducing the ability of the competitor to operate efficiently in the marketplace.
Commercial groups are affected by a wide range of factors that influence their motivation, ability, and the likelihood of them carrying out an attack. A threat agent sponsored by a commercial group may have the objective of preventing or reducing access to information systems (denial of service), manipulating or corrupting information (disinformation), or gaining access to information ([industrial] espionage). The impact that each of these types of attack will have varies and the likelihood of each must be considered separately in the light of the perceived aims of the commercial group and its target.
Malicious Threat Agent—Criminal
Criminal activity that provides a threat to information systems will be a result of the criminal attempting to:
-
Gain access to the system in order to defraud someone of resources (money or property),
-
Prevent the detection or investigation of other criminal activity,
-
Gain information that will enable them to commit other crimes,
-
Gain access to personal information that will enable them to commit other crimes (identity theft, blackmail, stalking, harassment).
As the descriptor "criminal" covers a huge range of activities, from financial gain through to murder, drug smuggling, trafficking, and sex offences, it is not possible to define generic characteristics.
For the purposes of this discussion, the threat agent from a "criminal" group will tend to have one of a small number of objectives. These will range from industrial espionage, to damaging the interests of competitors, to influencing small nation states. A characteristic of this group is that it will be risk-averse and conservative in its actions, taking great efforts to evade identification.
For an attack sponsored by a criminal group to be effective, it would require available resources to mount the attack. This is not normally an issue for a criminal group as they tend to be "cash rich" and do not have to account for their funds. If the required outcome is a sustained attack, they must also have sufficient personnel resources with adequate levels of skill available to mount and maintain the attack. Each criminal group will have specific drivers, but these will predominately be financial or competitive gain.
Any form of useable information on the capability of a criminal organization to carry out an attack is not, for the main part, available in the public domain from open sources. Law enforcement and national intelligence agencies invest a vast effort on attempting to gather this type of information and have had only limited success. Some inference can be gathered over a period of time as the effect of the actions of a group become apparent.
For an attack sponsored by a criminal group to be effective, it would require that the technology and level of skill was available to mount the attack. It is assumed there would be telecommunications, Internet connectivity, and an adequate power supply to allow the attack to take place. If the required outcome is a sustained attack, then the organization must also have sufficient depth of personnel resources with adequate levels of skill available to mount and maintain the attack. The driver for a criminal group to mount an information attack will be for financial gain or influence. This may not be apparent from the form of an attack. For example the Cali Drug Cartel may mount an intelligence gathering attack to gain information on the movements of British Royal Naval shipping assets in the Caribbean. The purpose of gaining this information would be to enable them to avoid the ships and thus allow them to deliver the drugs to mainland USA and as a result make more profit.
Although it is difficult to deal separately with each of the factors that may contribute to the capability of a criminal group to pose a threat, considerable information is available from which the individual elements that are required can be extracted.
Criminal groups are affected by a wide range of factors that influence their motivation, ability, and likelihood of them carrying out an attack.
A threat agent sponsored by a criminal group may have the objective of preventing or reducing access to information systems (denial of service), manipulating or corrupting information (disinformation), or gaining access to information ([industrial] espionage). The impact that each of these types of attack will have varies, and the likelihood of each must be considered separately in the light of the perceived aims of the criminal group and its target.
Malicious Threat Agent—Hacker
Hackers' objectives will normally be to gain status from their peers by causing visible damage to a system "because they can." Other reasons for an attack may be to gain access to a system in order to utilize its resources, either for the processing capability or in order to cover other activities. Due to the basis of this group being a technical capability rather than a specific motive or pressure, the type of attack that may be mounted will not be based on the impact to the system owner but rather the real or perceived benefit to the perpetrator.
For an attack sponsored by a hacker or hacker group to be effective, it would require available resources to mount the attack. This is not normally an issue for a hacker group, as they have support from their peers. If the required outcome is a sustained attack, they must also have sufficient personnel resources with adequate levels of skill available to mount and maintain the attack. Each hacker group will have specific drivers, but these will predominately be for self-aggrandizement or revenge.
Any form of useable information on the capability of a hacker group to carry out an attack will, if it is available, be in the public domain from open sources. Law enforcement and national intelligence agencies attempt to gather information on these groups, but due to their transient nature, have had only limited success. Some inference can be gathered over a period of time as the effect of the actions of a hacker group become apparent.
For an attack sponsored by a hacker group to be effective, it would require an appropriate level of skill available to mount the attack. It is assumed that there would be telecommunications, Internet connectivity, suitable technology, and an adequate power supply to allow the attack to take place. The driver for a hacker group to mount an information attack varies, with the main drivers being anything from curiosity, to financial gain, to revenge.
It is difficult to deal separately with each of the factors that may contribute to the capability of a hacker or hacker group to pose a threat, however considerable information is available from which the individual elements that are required can be extracted:
Hacker groups are affected by a wide range of factors that will have an influence on their motivation and ability and the likelihood of them carrying out an attack.
A threat agent that is sponsored by a hacker group may have the objective of preventing or reducing access to information systems (denial of service), manipulating or corrupting information (disinformation), or of gaining access to information ([industrial] espionage). The impact that each of these types of attack will have varies, and the likelihood of each must be considered separately in the light of the perceived aims of the hacker or hacker group and the target.
Malicious Threat Agent—Disaffected Staff
In this scenario, a disaffected member of staff is seeking to cause damage to the image or structure of the organization, or to extract value in the form of funds or property of some value.
Indicators of potential disaffected staff can be isolated, as there are a number of identified case histories that can be used to identify significant common factors from these case histories.
Any form of useable information on the capability of a disaffected member of staff to carry out an attack will, if it has been made available by the employing organization, be in the public domain. Information that is held by law enforcement and national intelligence agencies is not likely to be made available in reasonable time as it will, potentially, be required for prosecution.
For an attack undertaken by a disaffected member of staff to be effective, it would require that they possess the appropriate level of skill. The drivers for a disaffected member of staff to mount an information attack will vary, with the main drivers being anything from financial gain to revenge.
Malicious Threat Agent—Subversive Organizations
A member of staff belonging to a subversive organization will not, in probability, be known to their employer. The membership of a subversive organization will become an issue when the aims and objectives of the employing organization are in conflict with those of the subversive organization, or when the subversive organization can further its own aims using the information, facilities, infrastructure, or influence that is provided by the employing organization.
Indicators of this type of threat agent will be difficult or impossible to identify, as the motivation of the perpetrator will not be clear and their membership of the subversive organization will be difficult to determine. It is clear that some organizations will be more prone to this type of threat agent (for example government departments, the judiciary and law enforcement) as these are the types of organization that can leverage significant influence and favor. A possible example of a subversive organization would be the Freemasons.
Any form of useable information on the effect of subversive or secretive organizations on an organization with regard to their ability to carry out an attack will, if it has been made available, be unlikely to be in the public domain. Information that is held by law enforcement and national intelligence agencies is not likely to be made available as it will have either been gathered either as part of an investigation for subsequent criminal prosecution, or will have been gathered as intelligence for reasons of national security.
For an attack that is undertaken by a subversive within an organization to be effective, it would require that they possess appropriate level of skill. The drivers for a subverted member of staff to mount an information attack will vary, with the main drivers being to gain influence or intelligence.
Perhaps the most widely known society that affects members of the law enforcement community in the United Kingdom is that of the Freemasons. Whilst there is no attempt to impugn the name of the society or of its members, there has, for a number of years, been concern in the law enforcement community in the UK, that members of its staff belong to this organization but do not, and in some cases, will not, declare their membership. There are around the world many more examples such as The Skull and Bones Society in the United States, which boasted among its leadership President George Bush, or the Illuminati.
In this case it is not the individual or group that poses the threat agent that is the most significant element, but instead it is the organization that is the target of their attention. The most likely reason for this type of threat agent to mount an attack on an organization would be to gain influence and power. As a result, it is most likely that the organization type that will be most likely to be affected by this type of threat agent will be one where the major currency is power or influence.
Threat Amplifiers
A threat amplifier is any factor that increases either the likelihood of an attack taking place or the likelihood of the attack being successful. The factors may be either real or imagined. Examples of amplifiers may be discussion amongst hackers of the discovery of a new method for penetrating the security of a particular system or the announcement of a breakthrough in research at a particular organization that attracts attention from competitors.
Threat amplifiers will be a mixture of transient and longer-term influences and as a result, the sources of information on these will be varied. There is an added dimension with these influencing factors in that some are real and some are perceived.
Of the factors that were identified, those that are detailed below were considered to be the most significant. Taking each of these factors in turn:
-
Peer Pressure. A threat agent is more likely to carry out an attack if they feel that to do so will advance their prestige or status within their peer group. Particularly within hacking circles, elevated status and regard by other hackers will gain the individual access to information and resources that they did not have before, and will also achieve one of their aspirations of increased status within the community.
-
Fame. In all social groupings, a proportion of the individuals will seek to be recognized for the actions that they have undertaken. These actions may have been good or bad, but the desire of the individual that has carried out the attack to be recognized for their skill and daring will be quite high.
-
Access to Information. If an individual or group believes that they will gain access to useful information, either as a direct result of carrying out an attack or as an indirect benefit, they will, in some cases, be more inclined to carry out the attack. This access to information may be the primary motivation for the attack or a secondary benefit.
-
Changing Technology. Typically, the release of new technology is followed by its acceptance into common use, the discovery of weaknesses in the technology, and the exploitation of those weaknesses for illicit purposes.
-
De-Skilling through Scripting. As new techniques to subvert the security of systems are understood, the more skilled attackers, most particularly from the hacking community, will write scripts that will automate the attack. As these become available to the less skilled users who could not carry out the attack without the automated tools, the number of people that could conduct an attack is increased.
-
Skill and Education Levels. As the general level of education with regard to technology increases, the use of technology becomes almost ubiquitous, and as the skill level with regard to the use of new technologies increases, so too will the number of people who have the understanding of the technology and ways to carry out attacks increase.
Other Issues That Will Amplify the Threat to a System
-
Law Enforcement Activity. If the laws within the target country or the country from which the threat agent is operating are perceived to be weak or not relevant (for example, using the theft of electricity to charge a person for a hacking offense), or if the laws that are being used have not been tested in the courts or have been tested and shown to be ineffective, or if the law enforcement community is seen to be reluctant in its application of the law, the perceived lack of law enforcement will act as an amplifying factor.
-
Target Vulnerability. If the target that the threat agent has identified is perceived to be in a poorly protected state (for example if the system software is poorly maintained) or if it has vulnerabilities that come into effect through no fault of the system management, this may amplify the likelihood of the threat agent undertaking the attack.
-
Target Profile. If the profile of the target is such that in comparison to similar organizations, it is more attractive to the threat agent, this will amplify the likelihood of an attack.
-
Public Perception. if the perception of the public is against the organization that the target represents, then this will increase the likelihood of a threat agent carrying out an attack. An example of this would be Arab language web sites in the period after September 11, 2001.
Threat Inhibitors
A threat inhibitor will be any factor that decreases either the likelihood of an attack taking place or the likelihood of an attack being successful. The factors may be either real or imagined. Examples of inhibitors may be publicity relating to individuals being prosecuted or investigated for attempting to break into a system or a change in the state of the security of a system.
Threat inhibitors will, in a manner similar to threat amplifiers, be a mixture of transient and long-term influences and as a result, the sources of information on these will be varied. There is an added dimension with these influencing factors in that some are real and some are perceived. Examples of the type of factor that may inhibit the likelihood of an attack are detailed below.
Of the factors that were identified, those that are detailed below were considered to be the most significant. Taking each of these factors in turn:
-
Fear of Capture. If the threat agent has the perception that, if they initiate an attack, they are likely to be identified and captured, this will act as a deterrent and will inhibit the perpetrator.
-
Fear of Failure. If the threat agent believes that they are likely to fail in their attempt to conduct an attack, this may act to deter them from trying. This effect will be further enhanced if they are sensitive to the opinions of others and believe that the failure will become known to them.
-
Level of Technical Difficulty. If the defenses of a target that has been identified by a threat agent [are] shown to be difficult to overcome, then this will, in most cases, reduce the likelihood of the threat agent attacking the system as the threat agent will search for a less challenging target. In some cases this may be inverted as the threat agent will attack the most difficult of targets to prove or demonstrate their skills and abilities.
-
Cost of Participation. If the cost of undertaking the attack is too high, then this will inhibit the threat agent from initiating the attack. The cost may be in terms of finances or of the appropriate equipment or of time or information.
-
Sensitivity to Public Perception. If the target that the threat agent has selected is one that would gain the threat agent disfavor in the eyes of the public, this may act as a deterrent. An example of this would be an attack on the military resources of your own country during a conflict or an attack on a respected charity. The sensitivity of the threat agent to the public feelings may inhibit the action.
Other Issues That May Inhibit the Threat to a System
-
Law Enforcement Activity. If the laws within the target country of the country from which the threat agent is operating are strong and relevant laws that have been tested in the courts and shown to be effective and if the law enforcement community is seen to be aggressive in its application of the law, this will act as an inhibiting factor.
-
Target Vulnerability. If the target that the threat agent has identified is perceived to be in a well protected state (for example if the system software is well maintained and any probes of the system are actively pursued) or if the system is thought to be protected by a variety of devices, this should inhibit the likelihood of the threat agent undertaking the attack.
-
Target Profile. If the profile of the target is such that in comparison to similar organizations, it is less attractive to the threat agent, this will inhibit the likelihood of an attack.
-
Public Perception. If the perception of the public is in favor of the organization that the target represents (for example a hospital or an animal rescue center), then this will reduce the likelihood of a threat agent carrying out an attack.
-
Peer Perception. If the consensus of opinion of the peers of the threat agent is that the target would be "poor" for reasons of ease of access, resulting in no peer acknowledgement for a successful attack, or because the business of the target receives the support of the peer then this [decreases] the likelihood of an attack.
Threat Catalysts
Threat catalysts are those factors or actions that cause an attack to be initiated at the time and on the target that is selected. Again, the catalyst may be either real or perceived. Examples of catalysts are a change in the political relationship between two countries or the initiation of armed conflicts between two groups or an event that receives media attention and is, as a result, highlighted in the public awareness.
The main groupings of threat catalysts have been identified as:
-
Events. An event may be related to the attacker or to the target, either directly or indirectly. An event that influences the threat agent might be a personal experience or exposure to news that triggers predetermined actions. An event that affects the target might be a declaration of war or the initiation of a conflict between two nation states or for a company, a research and development success that might change the value of the company.
-
Technology Changes. A change in technology occurs at approximately nine-month intervals and as a result, new uses for technology become apparent and also shortcomings in the technologies that are in use become understood in the wider community. This constant technology churn can be the catalyst for a threat agent to carry out an attack as they see an opportunity developing.
-
Personal Circumstances. A change in the personal circumstances of the threat agent may be as a result of exposure to information that affects their values or beliefs. Alternatively it might be as a result of the actions of others, such as them being fired from their job and as a result having time to conduct an attack and the motivation of revenge against the former employer. Another alternative may be an elevation in position or peer regard and a desire for them to demonstrate their skills.
The catalyst that will cause a threat agent to initiate an attack on a target will, by its nature, be a transient occurrence.
Threat Agent Motivators
The factors and influences that motivate a threat agent are diverse and may operate singly or in unison. Whilst a range of groupings of threat agent motivators can be easily generated, the reason that each of the factors would come into effect and the degree that it would influence the threat agent is subject to a large number of varying influences.
The primary groupings of threat agent motivators are detailed below, together with a general description, but no further analysis of this subject area will be undertaken as a part of the research in this paper. The main motivational factors are:
-
Political. Where the motivation is for the advancement of a political cause, it may be because the threat agent wishes to further the cause of the political organization or further their own position within the political grouping. The outcome may be an attack on a political party's web site or the denial of service of a resource, particularly during the period running up to an election.
-
Secular. If the motivation of the threat agent is to support their secular beliefs, it is possible that the level of action that they will be prepared to take is quite high. A person that is supporting their secular beliefs will be likely to pursue an attack to a final conclusion.
-
Personal Gain. There are a number of aspects that have been grouped together under this general descriptor, as individuals are motivated by different rewards and gains. In this example, three types of gain have been identified. The first is financial gain, where the threat agent will gain money, goods or services as a result of carrying out the attack. This may be direct gain with the result being able to use stolen credit card numbers or it may be indirect gain through being paid to carry out the attack. The second type of gain is the acquisition of knowledge or information. In this area the benefit that the threat agent may seek is in the information itself or the knowledge that is gained in obtaining access to the information. The third type of personal gain is in the form of recognition by the threat agent's peers. This may result in the threat agent gaining status amongst their peers or gaining access to additional information or resources as a result of having demonstrated their abilities.
-
Religion. This is one of the more regularly observed motivational factors. Religious conflicts are amongst the most common and as a result it is to be expected that this will be a major motivational factor for a threat agent. Given the number of conflicts that are occurring at any point in time and the profile of the varied religions and the ability of an attacker to identify not only the religious artifacts but also the assets of the adherents of that religion (in a number of cases, it is possible to tell from an individual's name what their religion is likely to be), attacks on these types of targets are common.
-
Power. If an individual seeks to gain or to demonstrate that they have gained power, they may choose to demonstrate their capability through an attack on an information system.
-
Terrorism. Cyber Terrorism has not yet been conclusively observed. The use of information systems by terrorists is, conversely, well proven. An example would be if a terrorist threat agent were to use their capability to further their cause by denying service to the enemy or by achieving a propaganda victory.
-
Curiosity. This is a strong and difficult to quantify motive. As it is normally unfocussed and will only be directed at the target in question whilst the curiosity lasts, it is difficult to predict or to determine when the threat agent will have sated their curiosity.
Motivation
The elements that provide the motivation for an individual or a group to carry out an attack will be highly variable and subjective. Something that would provide motivation to one individual or group may not affect another similar group in the same way. The elements that have been identified below are general indicators only.
No attempt has been made to quantify or value the effect of the above factors on the threat agent as this is outside the scope of the project.
[2]Encarta World English Dictionary & (P) 1999, Microsoft Corporation. All rights reserved. Developed for Microsoft by Bloomsbury Publishing Plc.
[3]Andy Jones is a Senior Lecturer at the University of Glamorgan, Wales. Professor Jones has been kind enough to allow the extensive use of his master's thesis, "Identification of a Method for the Calculation of the Capability of Threat Agents in an Information Environment," in the writing of this chapter. Professor Jones is also the co-author, along with Dr. Kovacich and Perry Luzwick of the book, Global Information Warfare, published by Auer-bach in June 2002.
[4]Speaking at an InfoWar Conference in Washington, D.C., in September 1999,
[5]Andy Jones is a Senior Lecturer at the University of Glamorgan, Wales. Professor Jones has been kind enough to allow the extensive use of his master's thesis, "Identification of a Method for the Calculation of the Capability of Threat Agents in an Information Environment," in the writing of this chapter. Professor Jones is also the coauthor, along with Dr. Kovacich and Perry Luzwick, of the book Global Information Warfare, published by Auer-bach in June 2002.
[6]Espionage through the networks (network-enabled espionage) has become known as "Netspionage." See Netspionage: The Global Threat to Information, published by Butterworth-Heinemann, 2000, for a detailed look at this growing threat.
|
EAN: 2147483647
Pages: 204
- Key #4: Base Decisions on Data and Facts
- When Companies Start Using Lean Six Sigma
- Making Improvements That Last: An Illustrated Guide to DMAIC and the Lean Six Sigma Toolkit
- The Experience of Making Improvements: What Its Like to Work on Lean Six Sigma Projects
- Six Things Managers Must Do: How to Support Lean Six Sigma