How Parental Controls Work
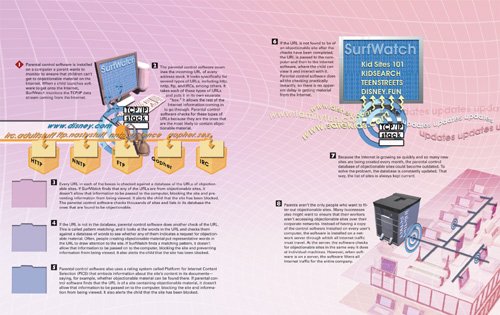 |
How Personal & Internet Security Works
ISBN: 0789735539
EAN: 2147483647
EAN: 2147483647
Year: 2004
Pages: 161
Pages: 161
Authors: Preston Gralla
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governing Information Technology Through COBIT
- The Evolution of IT Governance at NB Power