Steganography and the Internet
|
Intellectual Property Protection Systems
Digital Rights Management (DRM) Systems
Setup for DRM
To explain the need for Digital Rights Management systems it is best to start out talking about some deficiencies in traditional security models. Technology today and the security models that developed as a result of it primarily grew out of the defense industry. Traditional security models:
-
Are very hierarchical
-
Give governing powers to a system administrator
-
Focus on keeping intruders out
While this works well in a homogenous environment such as a military base, it becomes very cumbersome and impractical when it is thrown into distributed computing environments such as the Internet.
The Resistance to DRM
Another concern that DRM brings with it is that it is a disruptive technology. Two decades ago Hollywood was worried that VCRs would ruin the business of making movies, and prior to that music producers filed lawsuits to prevent radio stations from broadcasting their music to people for free.
As history has shown us, these disruptive technologies have created amazing new market opportunities.
Reasons for DRM: 11 Big Myths about Copyright
-
If it has no copyright notice, it is not copyrighted.
-
If I do not charge for it, it is not a violation.
-
If it is posted to Usenet, it is in the public domain.
-
My posting was just fair use!
-
If you do not defend your copyright, you lose it. Somebody has that name copyrighted!
-
If I make up my own stories, but base them on another work, my new work belongs to me.
-
They cannot get me; defendants in court have powerful rights!
-
Oh, so copyright violation is not a crime or anything?
-
It does not hurt anybody — in fact, it is free advertising.
-
They e-mailed me a copy, so I can post it.
-
So I cannot ever reproduce anything?
Intertrust
Intertrust software and hardware techniques can be implemented in a broad range of products that use DRM and trusted computing technologies, including digital media platforms, Web services, and the enterprise infrastructure.
Madison Project (from IBM)
The Madison Project was the code name for IBM's Electronic Music Management System (EMMS). This system was a stealth initiative to deliver piracy-proof, CD-quality music to consumers via the Internet in the summer of 1999. The AlbumDirect trial began in June and continued through December 1999; the follow-up research extended through mid-January 2000.
EMMS' end-to-end offerings were used to host and distribute music content over the Internet. In addition, EMMS had a clearinghouse capability that protected against unauthorized copying and use of music content by allowing content owners to specify consumer usage parameters and providing transaction reporting for financial clearing. The clearinghouse function is similar in concept to that used by a bank to assure that financial transactions are authorized. Trial participants also used the EMMS client software for music playback.
The experiment was set up at the AlbumDirect.com Web site, and it remains the most comprehensive initiative of its kind to date. The five biggest record companies — BMG Entertainment, EMI Music, Sony Music, Universal Music Group, and Warner Music Group — participated together in the tests. The idea was good except for the fact that MP3s had no copy protection and sites such as Napster sprang up, becoming a serious headache for the record industry.
One of the failings of the Madison Project was that AlbumDirect would not let users pick and choose the tracks they wanted; the purchaser had to buy the whole album. The audio files from AlbumDirect were enclosed in a proprietary wrapper allowing the consumer to play the files only on the PC with the company's proprietary player. The AlbumDirect sound files could not be moved directly to a portable MP3 player, and could not be played on a different computer, even if it was networked.
Another drawback was that albums cost $14 or more for just the download, not including the artwork for the album or the blank CD-R. In short, the process was not much less expensive than you would pay for a prepackaged CD of the same album at a retail store or online. For example, AlbumDirect was selling Sarah McLachlan's chart-topping Fumbling Towards Ecstasy for $14.38; the same title was available at Amazon.com for $14.99 and at CDnow.com for $15.99. IBM had announced that AlbumDirect would offer 2500 titles, but the actual number in late summer was closer to 1000.
While this may not be the best example for DRM, the potential for a balance between artists' copyrights and royalties weighed against a fair price for the consumer is very apparent, and it is only a matter of time before this technology is used with greater refinement and success.
Cryptolope (IBM)
Another product of IBM is called "cryptolope," which stands for cryptographic envelope. Cryptolope components are all written in Java. In fact, a cryptolope object, the "envelope," is nothing more than a JAR (Java archive) file and is used for secure, protected delivery of digital content. This enables what IBM calls "super distribution"; the package can be moved freely from place to place without losing intactness, authenticity, and associated terms and conditions. Cryptographic envelopes can be compared to secure servers; both approaches use encryption and digital signatures. But cryptographic envelopes go further:
-
A single envelope can encompass many different but interrelated types of content — for example, text, images, and audio — and keeps the package intact.
-
A cryptolope object is a self-contained and self-protecting object, and can be delivered any way that is convenient. A cryptolope object can be placed on CD-ROMs, FTP sites, or even passed casually from user to user, all without breaking the underlying security.
-
A cryptolope object ties the usage conditions of the content to the content itself. One usage condition you frequently set is the price of your cryptolope object, but there are others. You might specify that viewing the content can only be done with a special viewer. Or, for certain types of content, you might specify that it can only be delivered to a system that is capable of applying a digital watermark. Because the cryptolope object is digitally signed, usage conditions cannot be tampered with without invalidating the cryptographic envelope.
A cryptolope system consists of four components:
-
The builder. You use this component to build cryptolope objects. It packages the associated files and objects into a cryptolope object, and allows you to set the price and usage conditions you want. You can run the builder in "batch mode," creating cryptolope objects ahead of time, or you can run in "server mode," creating a cryptolope object on demand in response to a particular user's request.
-
The clearinghouse. You run this component to unlock your cryptolope objects for your users. Along the way, it verifies the integrity and enforces the terms and usage conditions you set in the cryptolope object.
-
The opener or cryptolope player. This component runs on the end user's PC. It protects the user against malicious or anonymous modifications to the cryptolope content. It seamlessly contacts the clearinghouse, unlocks the content to which the user is entitled, and cooperates with the clearinghouse to enforce your wishes.
-
The lightweight certificate authority. Digital signatures require digital certificates. The IBM cryptolope system works with standard X.509 certificates. The lightweight certificate authority allows you to produce your own certificates in cases where these commercially available digital credentials are too expensive or otherwise inappropriate for your application (Figure 8.2).
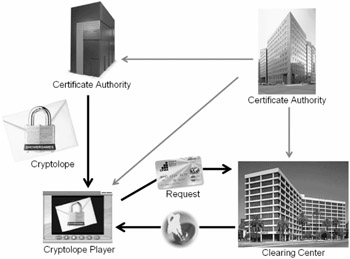
Figure 8.2
MagicGate and OpenMG (from Sony)
Sony Corporation is developing a new copyright management technology that could also revolutionize the way in which digital music content is delivered. Two new content protection technologies, tentatively called MagicGate and OpenMG, will provide a solution for protecting digital music on personal computers and personal audio player/recorders that use IC recording media.
MagicGate
MagicGate uses a microchip embedded in both the player and recorder, and media to ensure that protected content is transmitted only between compliant devices and media. All content is transmitted and stored in an encrypted format to prevent unauthorized copying, playback, and transmission of protected content.
MagicGate and OpenMG support the interchange of data between PCs and compliant audio player/recorders, allowing digital music content to be moved rather than copied, while preventing unauthorized copying, playback, and transmission. Sony is planning to broadly license MagicGate and OpenMG to relevant industries. Sony also plans to implement them into Memory Stick and PC-related products.
Super MagicGate
Sony has developed a secure electronic music distribution solution tentatively called Super MagicGate. It includes copyright management, electronic distribution, and content protection technologies for distributing digital music content electronically over the Internet and other digital networks. As with MagicGate and OpenMG, Sony will propose Super MagicGate to the SDMI and actively promote it to the relevant industries.
Super MagicGate features include:
-
Authentication and content encryption: Before music content is transmitted, authentication is conducted to ensure that both devices are compliant. If authentication is successfully completed, protected content can then be transferred and recorded in an encrypted format. This provides robust protection against the unauthorized accessing, copying, and distributing of digital music content.
-
Flexible usage settings: Super MagicGate accommodates flexible usage settings that give content providers more choice in setting conditions under which digital music content can be provided and enjoyed.
-
Active rights management: Usage and billing settings can be changed even after content has been delivered. Users could choose to purchase a music track after sampling it once for free or could receive a limited playback version of a song for upgrade to unlimited playback at a later date.
-
Offline usage management: Super MagicGate provides for offline tracking of usage and payment information, which allows flexible content usage and active rights management features to be applied to content enjoyed on portable audio player/recorders and products that are not directly connected to a network.
DRM Summary
-
Almost all things are copyrighted the moment they are written, and no copyright notice is required.
-
Copyright is violated whether or not you charged money; damages are determined by what was charged.
-
Postings to the Internet are not granted to the public domain and do not grant any permission to do further copying, except perhaps the sort of copying the poster might have expected in the ordinary flow of the Internet.
-
Fair use is a complex doctrine meant to allow certain valuable social purposes. Ask yourself why you are republishing what you are posting, and why you could not have just rewritten it in your own words.
-
Copyright is not lost because you do not defend it; that is a concept from trademark law. Ownership of names is also from trademark law, so do not think someone has a name copyrighted.
-
Fan writings and other work derived from copyrighted works is a copyright violation.
-
Copyright law is mostly civil law where the special rights of criminal defendants you hear so much about do not apply. However, new laws are moving copyright violation into the criminal realm.
Systems Built on Encrypted MP3 Files
Mjuice (from Audio Explosion)
Mjuice is a new encrypted file format for audio that uses 128-bit security encryption and is designed to work seamlessly with other software applications. Mjuice has been bought by ArtistDirect, who added this vital piece of technology to its software suite: a secure download solution. ArtistDirect offers digital music downloads in MP3 format, as well as in various secure formats belonging to other companies. Mjuice delivers its catalogue of 30,000 licensed tracks to consumers in a proprietary, secure MP3 format supported by major audio players such as WinAmp and Real Jukebox.
M-Trax (from MCY)
M-Trax technology not only encrypts and watermarks MP3, it also offers its own proprietary digitizing tool, allowing the delivery of CD-quality music. M-Trax philosophy states that focusing on security is a bad idea. M-Trax allows you to play the music at home, at the office, or in the car. It can be taken to a friend's house or, when you have tired of it, sold at a used record store. This solution gives you more flexibility, something you could not do with a normally encrypted MP3 file.
That is exactly what another encrypted-MP3 company, AudioSoft, has accomplished. After three digital copies are made, the copy capacity is disabled.
Key2Audio (from Sony)
Key2AudioXS is a system solution with a sophisticated audio copy control solution, and a clone-proof multimedia part that allows owners of original CDs to enjoy added value in the form of bonus material.
When the disk is inserted into the drive, an authentication process verifies it. If it is the original user, the user gets access to PC playback, CD-Extra content and a Web link. This Web link connects the user directly to a Web area where bonus material of the corresponding disk is available for download or streaming.
Via DRM, Key2AudioXS prevents unauthorized usage, copying, and online distribution. Any further usage is limited and restricted to the PC from which the initial access has been made. Only customers who have purchased the original disk will have access to authorized content.
Super Audio CD (SACD) and DVD-Audio
-
New format contains digital watermarks.
-
Require special new audio components to work.
-
Sony and Philips SACD contains two watermarks: One is for visual verification; the other is invisible and authenticates the disk for playback; without the watermark the disk will not play in a SACD player.
-
DVD-Audio disks use technology from Verance, and have acoustic watermarks that cannot be heard by the human ear and must be present for the player to recognize the disk.
-
Has not received wide consumer report because of lack of titles, legacy CD, and DVD support.
Recording Industry Association of America (RIAA)
The RIAA is a trade organization that comprises virtually all U.S. record labels and is partnered with dozens of technology firms, including Microsoft and IBM, to develop the Secure Digital Music Initiative (SDMI) to thwart piracy. In total, RIAA is a forum of more than 160 companies and organizations. SDMI specifications were to include MP3 but after a certain time, compliant players would no longer support unprotected MP3 files. While not officially a part of the SDMI, the Madison Project shared the initiative's aim of delivering digitally secure music.
The RIAA is working to develop voluntary, open standards for digital music to enable the widespread Internet distribution of music by adopting a framework that artists and recording and technology companies can use to develop new business models.
The RIAA, along with its sister organizations, IFPI and RIAJ, and the major record companies, was the driving force behind the initial launch of SDMI.
Secure Digital Music Initiative (SDMI)
The SDMI portable device specification is a voluntary, open standard to create and distribute music using unprotected formats, including those who wish to be able to post anonymously. The scope of this is beyond music and includes spoken audio content such as talk shows and audio books.
SDMI-compliant portable players will allow consumers to continue to play music in currently available unprotected digital formats, such as MP3, and also to access music that will only be available through SDMI-compliant digital distribution methods. The SDMI guidelines will offer consumers the opportunity to play and use their music collections in many flexible ways. Portable device specifications will provide for consumers to make personal copies of CDs for playback on their computers and on portable music devices. SDMI will provide artists with the opportunity to reach their fans through new technologies, while respecting and protecting their copyrights.
The MUSE Project (European Union and Recording Industry)
The MUSE project is the European equivalent to the RIAA. Its goal is to create a secure way of distributing music. The MUSE project has four main goals:
-
Audibility
-
Robustness
-
Tamperproof
-
Cost
In order to meet these goals, it is clear that audio watermarking technologies will be a vital component of future protection systems for sound recordings. BlueSpike submitted its Giovanni digital watermarking technology to MUSE and is among four proposals being considered out of a total of eight submitted.
There has been little effort thus far to merge audio and video watermarking efforts into a cohesive initiative. While this is not a problem that is being addressed presently, if MUSE chooses two entirely different methods of watermarking, any consumer device designed to handle digital audio and video may have to incorporate two different watermark detectors.
|
EAN: 2147483647
Pages: 220