Internet Explorer Security Settings
IE has very granular security settings that outpace any of its rivals. You can place Web sites in one of five IE security zones, and modify nearly 50 settings for each zone.
Security Zones
Internet Explorer has five different security zones:
-
Internet
-
Local intranet
-
Trusted sites
-
Restricted sites
-
Local computer
Internet security zones allow users to granularly define specific permissions for different Internet or intranet resources. Internet Explorer allows users (or administrators) to define ahead of time particular security permissions and privileges for various Web sites.
Local Computer Zone
The first four zones are readily accessible in IE (see Figure 8-12) by choosing the Tools menu option, then Internet Options, and then clicking on the Security tab. This unlisted zone is not easily end-user definable and represents content residing on the local computer. Also known as the My Computer zone, Windows now warns the user if content in the Local Computer zone wants to execute in IE. In earlier versions of IE, content from the Local Computer zone ran in the security context of the active user, but in IE 6 on XP SP2 and later versions, it is locked down with additional restrictions to prevent malware execution.
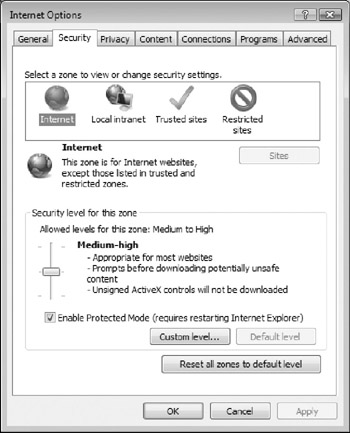
Figure 8-12: Internet Explorer security zones
The Local Computer zone lock down establishes the following default behaviors:
-
ActiveX controls may not run.
-
Java applets may not run.
-
Users may be prompted before they can run a script.
-
Users may be prompted before they can open a data source belonging to a different domain than the original server.
The Local Computer zone cannot be manipulated in IE by the end user, but can be configured using registry edits and programmatically. The zones can be manipulated in the registry at HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones. Each Zone is represented by the number 0 to 4, going from least to most restrictive. 0 is the My Computer zone, 1 is the Intranet sites zone, 2 is the Trusted Sites zone, 3 is the Internet zone, and 4 is the Restricted sites zone. If you are interested in manipulating zones using the registry read Microsoft KB article #182569 (http://www.support.microsoft.com/?id=182569). Editing zones via the registry allows a higher level of granularity than you can obtain through IE (that is, defining of acceptable TCP/IP port numbers and protocols for each zone), but for most users IE zones settings are best configured in IE.
Internet Site Zone
The Internet site is the default zone for all content not previously defined as residing in one of the other zones. Most of the time when you are surfing on the Internet using IE, the content being downloaded will reside in the Internet zone. The permissions and privileges in the Internet zone are moderately restricted (with a default of Medium-High security) as compared to the other zones. The security level is appropriate for most Internet sites, but is too lax when unpatched vulnerabilities are encountered or overall risk is high.
The Internet zone allows all scripts, signed ActiveX controls and Add-ons to run, although unsigned controls and plug-ins are disabled by default. Many Internet attacks can be stymied if scripting and ActiveX controls are disabled, but doing so will cause problems with many legitimate Web sites. If a widespread vulnerability is present, users can benefit greatly by customizing the security (covered next) to disable scripting and other non-HTML content. Most users could benefit by customizing the Internet security zone to an acceptable level of usability and security.
Local Intranet Zone
The Local intranet zone is a zone with elevated default privileges. The default security level is Medium-low. The intent is that users (or administrators) place internal trusted Web sites in the Local intranet zone, and any sites in this zone will have elevated privileges. By default, all Web sites residing on the local LAN (and other defined private IP subnets) will be placed in the Local intranet zone without the user having to specifically add the Web site. External Web sites can be added as well (see Figure 8-13), although users should remember that sites in this zone have elevated privileges.
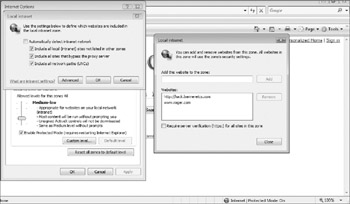
Figure 8-13: Adding a Web site to the Local intranet zone
As Figure 8-13 shows, along with the default selections, there are several options under the Local intranet zone. The first is "Include all local (intranet) sites not listed in other zones." This means that any server sites on the local network not listed in the Trusted Sites or Restricted sites zone will automatically be included here. If you disable this option, sites on the local network will not automatically be included in the Local intranet zone.
The "Include all sites that bypass the proxy server" option assumes that IE uses a non-transparent proxy to access non-local sites. By enabling the option, IE will add any sites to the Local intranet zone that are excluded from having to be filtered through the proxy server. The thinking is that only trusted sites would be excluded from being handled by the proxy server, and because they are trusted, they should be included by default in the Local intranet zone.
The Include all network paths (UNCs) option instructs Windows to include any NetBIOS shares in the Local intranet zone. This setting means that any security choices made on the Local intranet zone might impact regular Windows drive mappings. The Advanced button allows sites to be added manually. By default, the sites added to this location must be protected by using the HTTPS protocol to ensure site location authenticity, but this option is often deselected.
| Note | The Local intranet zone is disabled by default for non-domain computers. |
Trusted Sites Zone
Sites placed in the Trusted Sites zone have minimal restrictions and a Medium security level, but are not protected by Vista's Protected Mode. Most actions and content will be allowed to execute without user intervention. Even the highest risk actions only require the user to acknowledge before they proceed. Unlike the Local intranet zone, the Trusted Sites zone does not include Web sites by default. New sites can be required to be protected by HTTPS, the default, or just unsecured HTTP.
| Note | The Trusted Sites zone's default security level in IE 6 was Low. |
Restricted Sites Zone
The Restricted sites zone, as its name implies, restricts most non-HMTL content and activity by default. The security level is High. The only activity allowed without user intervention is pop-up ad blocking and font downloading. By default, no sites are within this zone. The Restricted sites zone has no HTTPS requirement option.
Most users won't have any entries here because if the Web site is high risk, they should not go there. With that said, if a user plans on visiting a high-risk Web site, they should put the Web site's domain name here, although don't expect IE's High security level setting to prevent all attacks. Malicious Web sites often have unknown "zero-day" attacks or use social engineering methods to trick the user into executing malicious code.
You can also create your own IE security zones programmatically or using registry edits, however, these zones are not easy to configure and cannot be accessed using the IE GUI. For more information, see http://www.blogs.msdn.com/ie/archive/2005/01/26/361228.aspx. I hope that Microsoft creates an easy way for an unlimited number of new zones to be easily created and configured in the future. Why they have not done this already is a mystery. Next, this chapter will cover in detail each IE security setting and their default settings in each of default zones.
Zone Security Settings
IE 7 has over 45 separate security settings that can be customized for each IE security zone. Each one is summarized here along with general recommendations. Recommendations differing from Microsoft's default settings will be noted where applicable.
.NET Framework-Loose XAML
XAML files are markup files that use Extensible Application Markup Language (XAML), which is the user interface markup language for .NET 3.0's Windows Presentation Foundation (WPF) platform. See http://www.en.wikipedia.org/wiki/XAML for more details. Loose XAML is a new .NET capability that allows a user to launch any XAML file on their hard disk (or a URL link on a web page) and run it within a browser without compilation. Loose XAML is a markup language and can only render existing content, making it a low security risk. It is enabled for all zones except for Restricted sites.
.NET Framework-XAML Browser Applications
This security setting covers, for lack of a better description, non-loose XAML, which is compiled and must be run within the confines of a browser. As with Loose XAML, it is low risk, and enabled by default in all zones except for Restricted sites.
.NET Framework-XPS Documents
The XML Paper Specification (XPS) is Microsoft's newest document format. Royalty-free, XPS uses WPF to render a document on the screen the same as when it is printed. Many see XPS as competitor to Adobe's PDF format. XPS doesn't appear to have the sophistication of PDF, and as such, probably isn't much of a security risk. Microsoft has enabled it in all security zones except for Restricted sites.
.NET Framework-Reliant Components-Run Components Not Signed with Authenticode
The .NET Framework is Microsoft's client-server programming environment (with some loose comparison to Java's virtual machine environment). .NET is the dominant form of programming across the Windows platform.
Code is signed to prove authorship. Authenticode is Microsoft's digital signing mechanism for authenticating code, scripts, and ActiveX controls. Any software publisher (vendor) can purchase an Authenticode digital certificate for code signing.
Running an unsigned component means that you cannot automatically authenticate who created and initially distributed the component (and whether or not it is untrusted). Microsoft allows unsigned components to run automatically in all zones but the Restricted zone. I believe Microsoft was too lax on this setting. It should be set to disabled in Internet and Restricted sites zone.
| Note | This option and the next may not be available unless you have also installed the .NET Framework client software. |
.NET Framework-Reliant Components-Run Components Signed with Authenticode
Signed code is rarely a problem. Signed code can contain bugs and viruses (we hope that these would be unknown to the signer at the time the code was signed), but it is not common. If you trust the signed code to be non-malicious, you can accept it to run automatically. There have been instances where spyware and adware companies used signed code to distribute their largely unwanted software. Microsoft enables this in all zones, but the Restricted zone. Because of the spyware and adware issues, we suggest this setting be set to Prompt in the Internet zone.
ActiveX Controls and Plug-Ins-Allow Previously Unused ActiveX Controls to Run Without Prompting
This setting instructs IE to allow previously installed ActiveX controls that have never been run before to execute without warning the user. Hackers often take advantage of rarely used, but installed controls. Microsoft has rightly disabled this setting in the Internet and Restricted sites zones.
ActiveX Controls and Plug-Ins-Allow Scriptlets
Scriptlets refers to Dynamic HTML (DHTML) scriptlets, which were deprecated in IE 5. In the past, there were a few malicious exploits that used DHTML scriptlets. For that reason, Microsoft has correctly disabled them in all security zones except the Local intranet zone.
ActiveX Controls and Plug-Ins-Automatic Prompting for ActiveX Controls
ActiveX controls can be virtually any content, executable, or script delivered over a network through IE. Java applets are even delivered as ActiveX controls, in most cases. Windows uses dozens to hundreds of ActiveX controls. Most aren't needed in IE and one of the big changes in IE 7 is to not allow any ActiveX control to run in IE by default, except those expressly authorized by the user or admin. This is the opposite behavior for IE 6.x and before.
This particular setting determines whether or not the user will be prompted by a pop-up dialog box to install an ActiveX control or plug-in. If disabled, the Web site will attempt to download and execute the content, but IE will not prompt the user with a dialog box. Instead (if IE 6.x XP SP2 or higher is installed) the user will be warned on the yellow information bar about an ActiveX control needing to be installed. The information bar warning is less obvious than a pop-up dialog box in the middle of the browser window.
Microsoft enables this option in the Local intranet zone and disables it in the rest. How this setting is configured to is up to the user, although I always like to be prompted in an obvious manner for any ActiveX controls that are trying to be installed. Otherwise, a Web site feature may fail and the cause of the failure might not be readily apparent.
ActiveX Controls and Plug-Ins-Binary and Script Behaviors
Binary behaviors (http://www.msdn.microsoft.com/workshop/browser/behaviors/howto/creating.asp) were introduced in IE 5.5 and allow binary programs to be linked to and control HTML content. A binary behavior is a compiled object that can interact directly with the underlying OS. Its code cannot be read or examined using normal view source commands. They can be used to do many malicious things from a web page.
Prior to Windows XP SP2 and Windows Server 2003 SP1 (where this setting first arrived), there was no way to prevent a binary behavior in any IE security zone, including sites residing in the Restricted sites zone. Now, by default, binary behaviors are disabled in the Restricted sites zone, but allowed in the rest. We believe that binary behaviors are too powerful to be allowed from any Internet site. Accordingly, this option should be set to Disabled (or Administrator approved) for all zones, unless needed.
ActiveX Controls and Plug-Ins-Display Video and Animation on a Web Page That Does Not Use External Media Player
If enabled, this setting could allow an untrusted media player to execute active content within a Web site. Microsoft has correctly disabled this setting for all security zones.
ActiveX Controls and Plug-Ins-Download Signed ActiveX Controls
Signed ActiveX controls usually present little risk unless signed by a spyware or adware vendor. IE prompts the user to approve on zones except for the Restricted sites. These defaults are acceptable.
ActiveX Controls and Plug-Ins-Download Unsigned ActiveX Controls
Unsigned ActiveX controls are highly risky and, generally, should be disabled, or set up to prompt if you plan to come in contact with needed unsigned controls. Microsoft correctly disables them in all zones.
ActiveX Controls and Plug-Ins-Initialize and Script ActiveX Controls Not Marked as Safe for Scripting
Once ActiveX controls or plug-ins (plug-ins are usually ActiveX controls) are downloaded-which is the option being decided in the two options mentioned previously-there is still the matter of whether to execute them. Vendors can mark their ActiveX controls as Safe for Initialization and Safe for Scripting. The first option determines whether the control can be initialized (i.e., started and executed). The second option is whether it can be directed by scripting, which means it could have different outcomes based upon the script. If both options are selected, then any web page can invoke them.
The idea is that if the vendor determines the control is safe (that is, can't be used in a harmful way), then why not let other web pages and programmers re-use the control? Unfortunately, there is no official guidance or testing tool that a vendor can run to find out if their "safe" control is really safe. In more than a dozen different exploits over the years, a control marked safe for scripting, was used to do something malicious.
In this particular option, IE is asking whether or not to allow web pages to initialize and script controls that are not marked safe? Considering that controls marked safe for scripting are potentially dangerous, ones that were tested and not found to be safe by their vendors definitely should not be allowed to run. Microsoft disables them in all zones. The default settings are good.
ActiveX Controls and Plug-Ins-Run ActiveX Controls and Plug-Ins
This setting has a huge impact on IE. It determines whether IE can run ActiveX controls and plug-ins at all, regardless of their safety, and regardless of whether they are signed or unsigned. Disabling this feature defeats many, if not most, exploits that have attacked IE over the years. Unfortunately, it is such an all-or-nothing proposition that disabling it causes problems with many popular Web sites.
Microsoft enables this option by default in all zones, but the Restricted sites zone, where it is disabled. This is an acceptable default. However, if you are worried about a widespread, malicious IE vulnerability that cannot be stopped by disabling this option, consider disabling this option until a patch or other alternative defense can be applied.
Alternately, IE can be instructed only to allow administrator-approved controls to run. In order to use this option, you must use group policy, an administrative template, a security template, or the IE Administrator's Kit-and know the control's CLSID.
ActiveX Controls and Plug-Ins-Script ActiveX Controls Marked Safe for Scripting
This setting discusses whether controls previously marked "safe" can be scripted. This is one of the toughest calls because ActiveX controls that were thought to be safe for scripting have been involved in many vulnerabilities over the years, but disabling it causes problems with many legitimate Web sites. Microsoft enables it by default in all zones except the Restricted sites zone, where it is disabled. This is an acceptable default. However, if you are worried about a widespread, malicious IE vulnerability that can be stopped by disabling this option, consider disabling this option until a patch or other alternative defense can be applied.
Downloads-Automatic Prompting for File Downloads
This setting determines whether the user will be prompted by a pop-up dialog box for normal file downloads. In most cases, the answer should be yes. It is always nice to know when a Web site is trying to download content. If this option is disabled, and the next option is enabled, then the user will download and potentially execute files without a primary acknowledgement (although the user may be prompted to confirm a download location). That particular situation would be harder to defend. Microsoft disables this for all zones, except for the Local intranet. This option should be enabled on all zones.
Interestingly, when this setting is disabled, most file downloads still prompt the user before proceeding. Internet Explorer contains a hard coded list of file types (by file extension) that the warning dialog box cannot be disabled for. They are:
-
ASP
-
BAS
-
BAT
-
CHM (IE5 only)
-
CMD
-
COM
-
EXE
-
LNK
-
INF
-
REG
-
ISP
-
PCD
-
MST
-
PIF
-
SCR
-
HLP
-
HTA (IE5 only)
-
JS
-
JSE
-
URL
-
VBS
-
VBE
-
WS
-
WSH
Downloads-File Download
Disabling this option prevents all file downloads. If the previous option is enabled, it is usually safe to enable this option. Microsoft enables this option in all zones, but in the Restricted sites zone where it is disabled. The defaults are acceptable.
Downloads-Font Download
This option determines whether IE HTML fonts, normally needed for the correct presentation of a web page, can be downloaded automatically. It is enabled in all zones by default, except the Restricted sites zone where it is set to Prompt. The default settings are good.
Enable .Net Framework Setup
If enabled, this will prevent .NET Framework from being installed. It is enabled in all zones except Restricted sites.
Java VM-Java Permissions
This setting will not appear unless the Java Virtual Machine (JVM) component has been installed. Microsoft's default settings are acceptable.
Miscellaneous-Access Data Sources Across Domains
This setting determines whether a web page can retrieve data from another server located in a different domain. If set to disabled, it will only allow data to be retrieved from the same server the originating web page is being served from or from another server in the same domain. A few exploits have been accomplished when this setting is enabled. Most Web sites access data on servers in the same domain. If this feature is not needed, keep it disabled. Microsoft disables it in most zones, but prompts it in the Local intranet zone. The default settings are acceptable in most cases.
Miscellaneous-Allow META REFRESH
A Meta-Refresh is an HTML command that instructs a browser to refresh the current web page after a periodic interval. It can also be used to re-direct a user, without their permission, to another web page. It has been used maliciously many times, but as long as other critical vulnerabilities are patched, there is little risk. Legitimate use of Meta-refreshes is common. Microsoft enables this option in all zones, but the Restricted sites zone. The default option is normally okay.
Miscellaneous-Allow Scripting of Internet Explorer Web Browser Control
This is a new option in IE 6.x XP SP2, although the control is not. The Web browser control is a stand-alone ActiveX control that can be used by programmers to add a mini-HTML browser to their application. After a few vulnerabilities were found by enabling this option by default, Microsoft disables it in all zones except for the Local intranet. The default option is acceptable.
Miscellaneous-Allow Script-Initiated Windows Without Size or Position Constraints
This option determines whether or not a Web site can open a new IE window anywhere and of any size. Unscrupulous web advertisers often make oddly sized browser screens (i.e. either very small or very large) to make it difficult on the user to close the pop-up advertising window. It is disabled by default in all zones except Restricted sites. This is an acceptable default choice.
Miscellaneous-Allow Web Pages to Use Restricted Protocols for Active Content
You can define, in the zone registry settings, which protocols and port numbers are allowed in a particular zone. Using this setting you can define whether or not Web sites in this zone can use protocols and port numbers not explicitly defined in the registry. Microsoft has this option set to Prompt in most zones, and disabled in the Restricted sites. The default options are acceptable.
Miscellaneous-Allow Websites to Open Windows Without Address or Status Bars
Many malicious Web sites and adware try to fool users by opening windows without addresses or status bars. This is disabled for Internet and Restricted sites zones, and enabled for Local intranet and Trusted Sites zones. The defaults are acceptable.
Miscellaneous-Display Mixed Content
This option determines whether or not you will be prompted if a web page tries to display content from a HTTP and HTTPS communications streams at the same time. In IE 6, if it was set to Prompt, they could receive the following "Security Information" message on the web pages that contain both secure (https) and nonsecure (http) content:
This page contains both secure and nonsecure items. Do you want to display the nonsecure items?
This is a very common occurrence on HTTPS Web sites, although to be truly secure they should never mix content types. All but the security paranoid disable this feature, even though Microsoft's default on all zones is Prompt. The default is acceptable unless you are particularly worried about spoofed HTTPS Web sites.
This option has been enhanced in IE 7 and users will no longer see the mixed-content dialog box prompt shown previously. IE7 will only render the secure content by default, and offers the user the opportunity to unblock the not secure content using the new Information Bar. This is an excellent change because in previous versions of IE, the user was asked the question without really knowing the difference between the secure and not secure content. Now, they will see the secure content first, separated from the non-secure content. Besides preventing some types of malicious attacks, it will prevent a lot of Web site advertising.
Miscellaneous-Don't Prompt for Client Certificate Selection When No Certificates or Only One Certificate Exists
This setting was introduced in IE 5.5 SP1. When this option is set to Enable, IE does not prompt the user with a "Client Authentication" message when it connects to a Web site that has no certificate or only one certificate. When Disabled, IE will display the following "Client Authentication" message even if the Web site does not have a certificate or has only one certificate:
Identification The Web site you want to view requests identification. Select the certificate to use when connecting.
Microsoft enables it in the Local intranet zone and disables elsewhere. This is an acceptable setting, although it also means that you may be sending your identity to the connected server.
Miscellaneous-Drag and Drop or Copy and Paste Files
Determines whether files and folders can be dragged and dropped between client and server, or whether files and folders can be copied and pasted between client and server. Strangely, if disabled in the Internet zone, it will not allow the described options between mapped drives on your computer if the NetBIOS shares were mapped using IP addresses instead of names. Dragging and dropping files is also helpful for FTP and WebDAV operations. Microsoft enables this setting in all zones except Restricted sites, where it is set to prompt. There is little misuse possible, so the defaults are acceptable. The one attack type the authors are aware of involves a timing attack where the user is tricked into overwriting an unintended file in an unintended location. This has been proven in theory, and even demonstrated a few times. However, this type of attack has never been used in a widespread manner, so Prompt should be acceptable.
Miscellaneous-Include Local Directory Path When Uploading Files to a Server
Enabled on all zones except for Restricted sites by default, it passes along the local directory path when uploading files using HTTP or FTP (within IE). Defaults are acceptable.
Miscellaneous-Installation of Desktop Items
Determines whether or not a Web site can install shortcuts and content to the user's desktop. Should be disabled or set to Prompt in most zones. Microsoft set it to Prompt in all zones, except for the Restricted sites zone, where it is disabled. The defaults are acceptable.
Miscellaneous-Launching Applications and Unsafe Files
Determines whether or not the hard coded file types listed previously can be launched or their associated programs executed. This is Enabled on the Local intranet, disabled on Restricted sites zone, and set to Prompt on the Internet and Trusted Sites zones. The defaults are acceptable.
Miscellaneous-Launching Programs and Files in an Iframe
Determines whether programs and files can be executed in an inline floating IE frame (IFRAME). Several vulnerabilities have used this feature over the years. It should be set to Prompt or Disabled. Microsoft sets it to prompt in all zones except where it disables it in the Restricted sites zone. The defaults are acceptable.
Miscellaneous-Navigate Sub-Frames Across Different Domains
Determines whether it is possible to open up a child sub-frame that references a server located in a different domain than its parent. A malicious Web site could mimic a legitimate Web site by inserting a window as a frame within the legitimate Web site's window. This feature was used in a few exploits years ago, but now is not considered overly dangerous. Microsoft disables this setting in all zones, except for the Local intranet zone. I prefer to set the option to Prompt in the Internet zone for usability reasons.
Miscellaneous-Open Files Based on Content, Not File Extension
This option determines whether IE will read the first 200 bytes of a file's header to determine if the file meets the MIME Type the Web site claims it to be. If the extension matches the MIME type, IE does not check the file header. But if there is a disagreement, IE reads the file header in an attempt to determine the correct MIME Type. It has been enabled in all zones except for the Restricted sites zone. We would Enable it there as well.
Miscellaneous-Software Channel Permissions
This setting specifies the computer's level of access for Web-based software distribution channels. The possible values are: High Safety/Low Safety/Medium Safety
-
High Safety: Prevents users from being notified about software updates by e-mail, software packages from being automatically downloaded to users' computers, and software packages from being automatically installed on users' computers.
-
Medium Safety: Notifies users about software updates by e-mail, and allows software packages to be automatically downloaded to (but not installed on) users' computers. The software packages must be validly signed; users are not prompted about the download.
-
Low Safety: Notifies users about software updates by e-mail, allows software packages to be automatically downloaded to users' computers, and allows software packages to be automatically installed on users' computers.
The Internet zone and Local intranet zones are set to Medium safety. The Trusted Sites zone is set to Low safety. The Restricted sites zone is set to High safety. The selections are reasonable.
Miscellaneous-Submit Non-Encrypted Form Data
This option determines whether HTML pages in the zone can submit unencrypted forms to or accept unencrypted forms from servers in the zone. Forms sent using SSL are always allowed. This option is usually enabled, except for Restricted sites where it is set to Prompt. The defaults are good.
Miscellaneous-Use Phishing Filter
Enabling this filter tells IE 7 to send each new domain URL to Microsoft's anti-phishing servers for inspection before allowing the page to be displayed. If a site has been defined as fraudulent, the user is warned. It slows down web surfing, but increases security significantly. It should be enabled on zones except Local intranet sites (because it isn't needed and only affects performance), and these are the Microsoft defaults.
Miscellaneous-Use Pop-Up Blocker
Determines whether the built-in pop-up blocker is turned on. As with the previous setting, this should be enabled for all zones, except the Local intranet. This is the Microsoft default, as well.
Miscellaneous-Userdata Persistence
Determines whether a Web site can save a data about the user or the current session on the user's hard drive, much like a cookie would be able to do. This feature is used by many legitimate Web sites, and although it can possibly be used maliciously, it's best to leave it turned on. The mischief caused by enabling this is limited to tracking-no code execution or exposure of local data (unless you count browsing habits). Microsoft leaves it turned on by default for all zones, but the Restricted sizes zone and this is acceptable.
Miscellaneous-Web Sites in Less Privileged Web Content Zone Can Navigate into This Zone
This setting prevents less privileged content from initiating new connections into higher privileged zones. This was created to defeat a new type of malicious attack. Microsoft has this option enabled in most zones, but disabled in the Restricted sites zone. It should be disabled by default in the Internet zone.
Scripting-Active Scripting
This setting determines whether scripting is allowed in IE. If turned off, this disables JavaScript and VBScript engines. Although many IE exploits rely on scripting to work, so do most Web sites. Leave this enabled unless you are trying to defend against a widespread attack that cannot be stopped by using alternative defenses. Microsoft enables on all zones except the Restricted sites zone and this is acceptable.
Scripting-Allow Programmatic Clipboard Access
In previous versions of IE, a malicious Web site could script language to copy the data last used in the Clipboard application (from user's Edit, Copy, Edit, Paste operation) to their Web site. Users and administrators often use the Clipboard to copy long and complex passwords during a logon sequence. This vulnerability could potentially let a malicious Web site see confidential data.
This option used to be called "Allow paste operations via script" in previous versions. See http://www.sourcecodesworld.com/special/clipboard.asp to determine if your browser is vulnerable to paste operations manipulations. In IE 6, Microsoft enabled this option in all zones except the Restricted sites zone. In IE 7, this value is set to Prompt in the Internet and Trusted Sites zones, enabled in the Local intranet zone, and Disabled in the Restricted sites zone. It should be disabled on all zones unless needed. When set to prompt, the user will see a dialog box, similar to Figure 8-14, when a Web site attempts to access the Clipboard.
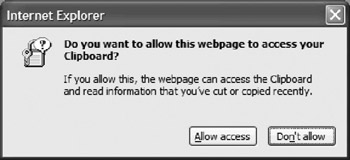
Figure 8-14: Internet Explorer asking for confirmation before letting a Web site use the Clipboard for pasting operations
| Note | A developer, malicious or legitimate, can add their program's executable to the \HKLM\Software\Microsoft\Windows\Internet Explorer\Main\FeatureControl\registry key (see http://www.msdn.microsoft.com/library/default.asp?url=/library/en-us/IETechCol/cols/dnexpie/clipboard_scriptaccess.asp for more details) to bypass the warning prompts. |
Scripting-Allow Status Bar Updates Via Script
This option determines whether a Web site can update the status bar using a script. Some malicious Web sites use scripts to fraudulently modify IE's status bar, such as indicating whether SSL is enabled or not. It is correctly disabled for Internet and Restricted sites zones.
Scripting-Allow Websites to Prompt for Information Using Scripted Window
This setting determines whether a Web site can query IE for personal information (for example, your e-mail address). Microsoft has appropriately turned it off in the Internet and Restricted sites zones.
Scripting-Scripting of Java Applets
This determines whether Java applets can be scripted. Although there have been dozens of Java exploits found over the years, only one has ever been widespread. The overall risk is low. You can enable the scripting of Java applets on all zones except the Restricted sites zone, which is the Microsoft default.
User Authentication
Last, this option determines how IE responds to a request for the browser to authenticate the user. In previous versions of IE, IE would always respond to authentication requests by trying to log in with the current user's name and password. Unfortunately, it is possible for malicious Web sites to force unprotected Windows computers to use older, weaker authentication protocols (LAN Manager), which are easy to crack.
A common ploy for a spammer was to send the victim a spam e-mail that contained a 1-pixel graphic (called a web spider or beacon) that needed to be downloaded from the spammer's malicious web server to display in the e-mail. Previous versions of Outlook and Outlook Express would attempt to download the graphic automatically to display in the e-mail. The hostile Web site would request user authentication to download the web spider, and tell the victim's computer that it only understands the LM authentication protocol. Thus, all the victim did was open an e-mail and their computer was sending back their login name and password in an easily hackable format.
Now IE will only send the user's current logon name and password if the site is listed in the user's Local intranet sites zone. Otherwise, IE will try to logon anonymously or prompt the user for their logon name and password. IE's default settings are acceptable.
Table 8-2 summarizes IE's default zone security settings. We make practical recommendation changes as highlighted in parenthesis where appropriate.
| DEFAULT SETTING PER ZONE (AND RECOMMENDATION IF THEY VARY FROM MICROSOFT'S DEFAULTS) | ||||
|---|---|---|---|---|
| SETTING | INTERNET | LOCAL INTRANET | TRUSTED SITES | RESTRICTED SITES |
| Default Security level | Medium-High | Medium-Low | Medium | High |
| Protected Mode | On | On | Off | Off |
| .NET Framework-Loose XAML | Enable | Enable | Enable | Disable |
| .NET Framework-XAML browser applications | Enable | Enable | Enable | Disable |
| .NET Framework-XPS documents | Enable | Enable | Enable | Disable |
| .NET Framework-reliant components-Run components not signed with Authenticode | Enable (Disable or Prompt) | Enable (Disable or Prompt) | Enable (Disable or Prompt) | Disable |
| .NET Framework-reliant components-Run components signed with Authenticode | (Enable Prompt) | Enable | Enable | Disable |
| ActiveX controls and plug-ins-Allow previously unused ActiveX controls to run without prompting | Disable | Enable | Enable | Disable |
| ActiveX controls and plug-ins-Allow Scriptlets | Disable | Enable | Disable | Disable |
| ActiveX controls and plug-ins-Automatic prompting for ActiveX controls | Disable | Enable | Disable | Disable |
| ActiveX controls and plug-ins-Binary and script behaviors | Enable (Disable or Prompt) | Enable (Disable or Prompt) | Enable (Disable or Prompt) | Disable |
| ActiveX controls and plug-ins-Display video and animation on web page that does not use external media player | Disable | Disable | Disable | Disable |
| ActiveX controls and plug-ins-Download signed ActiveX controls | Prompt | Prompt | Prompt | Disable |
| ActiveX controls and plug-ins-Download unsigned ActiveX controls | Disable | Disable | Disable | Disable |
| ActiveX controls and plug-ins-Initialize and script ActiveX controls not marked safe for scripting | Disable | Disable | Disable | Disable |
| ActiveX controls and plug-ins-Run ActiveX controls and plug-ins | Enable | Enable | Enable | Disable |
| ActiveX controls and plug-ins-Script ActiveX controls marked safe for scripting | Enable | Enable | Enable | Disable |
| Downloads-Automatic prompting for file downloads | Disable (Enable) | Enable (Enable) | Disable (Enable) | Disable |
| Downloads-File download | Enable | Enable | Enable | Disable |
| Downloads-Font download | Enable | Enable | Enable | Disable |
| Enable .NET Framework setup | Enable | Enable | Enable | Disable |
| Java VM-Java Permissions* | High safety | Medium safety | High safety | Disable Java |
| Miscellaneous-Access data sources across domains | Disable | Prompt | Disable | Disable |
| Miscellaneous-Allow META REFRESH | Enable | Enable | Enable | Disable |
| Miscellaneous-Allow scripting of Internet Explorer web browser control | Disable | Enable | Disable | Disable |
| Miscellaneous-Allow script-initiated windows with size or position constraints | Disable | Enable | Disable | Disable |
| Miscellaneous-Allow web pages to use restricted protocols for active content | Prompt | Prompt | Prompt | Disable |
| Miscellaneous-Allow Web sites to open windows without address or status bars | Disable | Enable | Enable | Disable |
| Miscellaneous-Display mixed content | Prompt | Prompt | Prompt | Prompt |
| Miscellaneous-Don't prompt for client certificate selection when no certificates or only one certificate exists | Disable | Enable | Disable | Disable |
| Miscellaneous-Drag and drop or copy and paste files | Enable | Enable | Enable | Prompt |
| Miscellaneous-Include local directory path when uploading files to a server | Enable | Enable | Enable | Disable |
| Miscellaneous-Installation of desktop items | Prompt | Prompt | Prompt | Disable |
| Miscellaneous-Launching applications and unsafe files | Prompt | Enable | Prompt | Disable |
| Miscellaneous-Launching programs and files in an IFRAME | Prompt | Prompt | Prompt | Disable |
| Miscellaneous-Navigate sub-frames across | Disable (Prompt) | Enable | Disable | Disable |
| Miscellaneous-Open files based on content, not file extension | Enable | Enable | Enable | Disable (Enable) |
| Miscellaneous-Software channel permissions | Medium safety | Medium safety | Medium safety | High safety |
| Miscellaneous-Submit non-encrypted form data | Enable | Enable | Enable | Prompt |
| Miscellaneous-Use Phishing Filter | Enable | Disable | Enable | Enable |
| Miscellaneous-Use Pop-up Blocker | Enable | Disable | Enable | Enable |
| Miscellaneous-User data persistence | Enable | Enable | Enable | Disable |
| Miscellaneous-Web sites in less privileged web content zone can navigate into this zone | Enable (Disable) | Enable | Enable | Disable |
| Scripting-Active Scripting | Enable | Enable | Enable | Disable |
| Scripting-Allow Programmatic clipboard access | Prompt (Disable or Prompt) | Enable (Disable) | Prompt (Disable) | Disable |
| Scripting-Allow status bar updates via script | Disable | Enable | Enable | Disable |
| Scripting-Allow Web sites to prompt for information using scripted window | Disable | Enable | Enable | Disable |
| Scripting-Scripting of Java applets | Enable | Enable | Enable | Disable |
| User Authentication | Automatic only in Intranet zone | Automatic only in Intranet zone | Automatic only in Intranet zone | Prompt for username and password |
IE Advanced Settings
Advanced settings apply consistently across all IE security zones. Some of the settings complement or override the options available in the separate security zones. In general, settings chosen here win over the individual settings in the security zones (but not always). For that reason, a user or administrator must be aware not to set configuration options in conflict with one another. These issues are noted when applicable.
There are over 60 different Advanced settings in IE 7. This section of the chapter will cover only the settings that can purposely affect IE's overall security.
Browsing-Disable Script Debugging (Internet Explorer or Other)
This is two separate options that tell IE whether or not to check for script errors. If enabled, as is the default, it disables this ability. This is usually only useful for programmers. If enabled, IE warns the user when script errors are located. Malicious Web sites often have code bugs so disabling this feature would show an interested programmer the coded mistake automatically, if they wanted to know. The delineation between IE script debugging and other foreign debuggers is new to the latest versions of IE.
Browsing-Display a Notification About Every Script Error
If enabled, IE displays a notification message about every error it encounters in a script. It is disabled by default and this is usually an acceptable choice. Like the last option, there is little to gain by enabling this feature unless the user is a programmer and looking for security coding issues.
Browsing-Enable Third-Party Extensions
Extensions allow a browser's functionality to be enhanced and extended. Although many legitimate programs install extensions, so too does malware, spyware, and adware. Microsoft enables this by default. If legitimate extensions are not needed, disable.
Browsing-Use Inline Autocomplete
Disabled by default, this feature determines whether IE's AutoComplete feature (which automatically tries to fill in requested information, such as a user's name and address) does so when a Web site form requests stored information. It can be used maliciously by a remote Web site by tricking the browser into serving up otherwise confidential information or locally by an unauthorized user. Keep disabled unless needed.
International-Send UTF-8 URLS
UTF-8 encoding allows a user to use URLs that include non-ASCII and foreign language characters, regardless of the language of the user's' operating system and browser language. Without UTF-8 encoding, a web server must be based on the same language code page as that of the user's to correctly render URLs containing non-ASCII or foreign characters. Disabling would prevent some URL obscurity spoofing attacks, such as the double-byte encoding, but would cause problems with many legitimate Web sites. Microsoft has it enabled by default and it should probably stay that way.
Java (or Java-Sun)-Use JRE x.x for <applet>
Only appears if a Java Virtual Machine (JVM) environment is installed. There is some additional risk from running Java, but if you keep Java patched, you can leave this option enabled. Often needed for legitimate Web sites. If you use Java, make sure to keep up on the latest Java JVM and patches.
Security-Allow Active Content from CDs to Run on My Computer
A new IE setting. Determines whether browser content can run in the Local Computer zone if launched from local CDs. If disabled, active content runs in the Internet zone. Leave disabled unless needed.
Security-Allow Active Content to Run in Files on My Computer
A new IE setting. Determines whether browser content can run in the Local Computer zone if launched locally. If disabled, all active content runs in the Internet zone. It has often been the cause of many exploits. Leave disabled unless needed.
Security-Allow Software to Run or Install Even If the Signature Is Invalid
Disabled by default and should be left that way. If enabled, allows unsigned and untrusted software to run.
Security-Check for Publisher's Certificate Revocation
Enabled by default and should be left enabled. Checks to see if the publisher's (that is, software vendor who signed the program) digital certificate has been revoked by the Certificate Authority (CA). You would never want to run a program whose publisher's certificate was revoked. This could mean that the publisher's private key was stolen and has been fraudulently used to sign a malicious executable.
Security-Check for Server Certificate Revocation
If enabled, and it is by default, IE will check to see if a server's SSL or TLS digital certificate is revoked, during the initial handshake connection to a HTTPS Web site. However, it is not uncommon for many legitimate Web sites' revocation to "fail" for one reason or another. Usually it is because the revocation link (called the certificate revocation link distribution point) is unreachable at the moment or not defined correctly.
If the Web site is legitimate and the digital certificate it gave is legitimate, you can usually choose to ignore the certificate revocation message. Usually the additional warning messages, if they occur, encourages users to further verify the SSL connection status. And anything that makes the end user more involved in verifying digital certificates without always accepting them by default is a good thing.
Security-Check for Signatures on Downloaded Programs
This option is enabled by default and should remain that way. It ensures that any downloaded programs have verified digital signatures or else displays a warning about what is invalid about the digital certificate (or the digital signature may be missing all together). An invalid or missing digital signature means the software is at a higher risk for maliciousness, albeit, remembering that most downloadable software on the Internet is not signed.
Security-Do Not Save Encrypted Pages to Disk
Disabled by default, this option ensures that pages encrypted by SSL/TLS are also stored encrypted on the local disk. This option can be left disabled in most organizations unless the security risk of a local intrusion is higher than average. Normally, in order for an intruder to search and find downloaded Internet content belonging to another user, they must have admin rights to search the user's profile. If the intruder has local admin rights, this is just one of the many attacks that they can launch. Still enabling this security option causes only slightly higher disk and CPU utilization. Most administrators only turn it on computers with shared access.
Security-Empty Temporary Internet Files Folder When Browser Is Closed
As with the previous option, this feature is disabled by default and only needs to be enabled if local admin attack risk is higher than normal. If turned on, the TIF area will be deleted every time IE is closed. This option does have a moderate to substantial performance penalty during the erasing actions. Most administrators only turn it on computers with shared access.
Enable Memory Protection to Help Mitigate Online Attacks
IE's main executable, Iexplore.exe, is not protected by Data Execution Protection (DEP), although on a positive note, it is enabled for Ieuser.exe and Ieinstal.exe. We recommend that you enable DEP protection for Iexplore.exe, unless you use a conflicting add-on (e.g. Java). To enable DEP protection for IE, start IE in admin mode, click on the Tools menu option, and choose the Advanced tab under the Internet Options menu selection. Then, enable the Enable memory protection to help mitigate online attacks.
Security-Enable Integrated Windows Authentication
This setting works in conjunction with the security zone setting, User Authentication, which defines whether authentication would happen automatically or not, and to which zones. This setting determines whether Windows logon authentication can be used, if prompted.
There are four types of Windows logon authentication protocols: LM, NTLM, NTLMv2, and Kerberos. If this feature is enabled, which it is in IE 7, users can logon using Windows authentication to Web sites that support integrated Windows authentication (such as IIS). The integrated login presents the user's currently logged in name and password for authentication if requested. If the related zone setting is set to automatic, the authentication occurs without the end user having even been aware of the exchange. If the automatic authentication has not been approved, the user will be prompted for logon credentials.
By default, all newer versions of IE will connect to all web servers using anonymous authentication first. If the web server requires Windows logon authentication, in most cases the user will be prompted for a logon name and password unless they are connecting to an intranet site. When enabled, the automatic use or prompting of integrated login can be controller by IE security zone. Even if this feature is turned on, Windows logon authentication methods normally only work on the local network (or forest), and over VPNs; and are not normally allowed over the Internet (without much planning, configuration, and management).
Although there is little risk to most environments by enabling this feature, you can leave it disabled unless needed. Remember to turn it on if needed (i.e., for SharePoint Services, IIS, and so on). If allowed to non-intranet sites, disable the use of LM and NTLM authentication protocols (discussed in Chapter 3) to prevent malicious remote Web sites from requesting insecure versions of user logon credentials.
Security-Phishing Filter Settings
New with IE 7, this option enables or disables IE's new anti-phishing filter option. We can think of no reason to disable it, other than the 1–2 second delay it incurs sometimes on new Web site connections.
| Note | Occasionally, the phishing filter will not check on the Web site and report whether the Web site is a known phishing site until many seconds after the web page is loaded. It might appear as if a web page is not a suspected phishing site, and then 2–10 seconds later the Web site is accurately marked as a known phishing site. This may be a result of the performance trade-offs allowing the Web site to load during the same time the filter check is made, meaning that there is the slight chance that a user could use the malicious web page for a few seconds prior to the warning. |
The three Phishing Filter options are as follows:
-
Check Web sites Automatically
-
Do Not Check Web sites Automatically
-
Turn off Phishing Filter
If you turn the filter off completely, the Check This Website option, which can be done manually on a per-site basis, is disabled. Choose the Do Not Check Websites Automatically option if you want to allow per-site manual checking. I frequently use the Report This Website option to report phishing and fraudulent Web sites to Microsoft to benefit other users. After reporting the suspected Web site, it goes through a review process before being made available as a confirmed phishing site to other users.
The anti-phishing filter can also be enabled or disabled using IE zone security settings. If the phishing filter is turned off in Advanced settings, it overrides settings (s) in the separate security zones.
Security-Use SSL 2.0, SSL 3.0, TLS 1.0
This option determines what version of SSL is allowed or if Transport Layer Security (TLS) is enabled. SSL 2.0 is disabled by default, but the other two options are enabled. TLS is the next version of SSL. (There will be no SSL 4.0 standard.) It works more securely at a lower layer of the OSI model and has many improved security features. SSL 2.0 should be disabled. There are a few Web sites still using it, but the overall percentage is not overwhelming. All the good commercial sites have long supported SSL 3.0 and above.
Security-Warn About Invalid Site Certificates
This option is enabled by default and warns the user if a web server's digital certificate is invalid (if SSL/TLS are enabled in the previous setting). Legitimate sites with invalid certificates abound, unfortunately, usually because of expired useful life dates or because the current Web site doesn't make the certificate's Web site address. Still, warning users that a digital certificate is invalid raises awareness and may alert them to a spoofing or man-in-the-middle attack.
Security-Warn If Changing Between Secure and Not Secure Mode
This setting determines whether or not IE will notify the user that they are being directed between SSL/TLS and non-SSL/TLS sites. The default option of Enabled is acceptable.
Security-Warn If Forms Submittal Is Being Redirected
As with the separate identical security zone setting, this option determines whether the user will be notified that the data they are submitting to a Web site is being redirected to another Web site. Although this can occur on legitimate Web sites, the default option of Enabled should be left turned on to warning users of spoofing or man-in-the-middle attacks. There is a similar (but different) zone setting, which determines if the user can submit forms data unencrypted or not.
Table 8-3 summarizes IE 7's default settings.
| ADVANCED SETTING | DEFAULT SETTING |
|---|---|
| Browsing-Disable Script Debugging (Internet Explorer or Other) | E |
| Browsing-Display a notification about every script error | D |
| Browsing-Enable third-party browser extensions | E |
| Browsing-Use inline AutoComplete | D |
| International-Send UTF-8 URLs | E |
| Java (or Java-Sun)-Use JRE x.x for <applet> | E |
| Security-Allow active content from CDs to run on My Computer | D |
| Security-Allow active content to run in files on My Computer | D |
| Security-Allow software to run or install even if the signature is invalid | D |
| Security-Check for publisher's certificate revocation | E |
| Security-Check for server certificate revocation | E |
| Security-Check for signatures on downloaded programs | E |
| Security-Do not save encrypted pages to disk | D |
| Security-Empty Temporary Internet Files folder when browser is closed | D |
| Security-Enable Integrated Windows Authentication | E |
| Security-Phishing Filter Settings | Check Web sites Automatically |
| Security-Use SSL 2.0, SSL 3.0, TLS 1.0 | D, E, E |
| Security-Warn about invalid site certificates | E |
| Security-Warn if changing between secure and not secure mode | E |
| Security-Warn if forms submittal is being redirected | E |
Other Browser Recommendations
IE is a complex piece of popular software. Hackers are never going to stop attacking it, and it is unlikely to suddenly become unexploitable. Odds are that IE will always remain one of the most exposed and attacked pieces of software in Microsoft's platform. Still, running IE doesn't mean getting a guaranteed successful attack. Here are the many defenses you can take to prevent IE exploitation, going from most useful to least.
Don't Browse Untrusted Web Sites
The number one way to prevent malicious exploitation is to not visit unknown and untrusted Web sites. Don't click on "weird" links sent to you in e-mail. Look out for strange looking phishing URLs. Too many encoded characters or sound-alike names and URLs should set off warning bells. Any company asking for your financial information unexpectedly is probably a fraud. Verify your SSL links by scrutinizing the accompanying digital certificate. Make sure all the information is valid and points to the correct Web site. IE 7, with its anti-phishing filter, is making great strides in preventing users from visiting fraudulent Web sites. But fake Web sites can be made in seconds, and more than likely always stay well ahead of IE's real-time checking behavior.
If you just have to visit a non-trusted Web site, consider running the IE session in a virtual environment like Microsoft's Virtual PC or VMware's VMWorkstation. That way if anything ugly happens, you can reset the session and minimize the potential risk to the real underlying OS. Microsoft has already released the Shared Computer Toolkit for Windows XP (http://www.microsoft.com/windowsxp/sharedaccess/overview.mspx), which, among other features, prevents permanent changes (i.e., made by malware) from being saved in between reboots. Also, consider using a less functional alternate browser or one that has been set to run no active content at all (for example, Lynx) when visiting unknown Web sites.
Many people run less functional browsers all the time in the hope that it will prevent malicious exploitation. While it may minimize the risk, at the expense of functionality, IE's coding cannot be removed from Windows. Even when you run an alternate browser, it is very possible for a malicious program to call IE's coding (for example, via e-mail, embedded link in Microsoft Office, and so on). So, even if IE isn't your main browser, be sure to install all patches and updates. Not doing so, even if you don't use it, increases exposure risk.
Keep IE Patches Updated
Once you are running IE 6.x or 7.x, keep on top of the patches. Patch any critical patches as soon as you can after testing. These days many IE exploits are getting released within three days of patch announcement. In the past you could afford to wait a few weeks. No longer. Immediate testing and deployment of critical patches should be a priority of any organization.
EAN: N/A
Pages: 163