Data Execution Protection
Buffer overflows work by unexpectedly co-mingling data and executable code in a single memory area. The buffer overflow places executable code into a section of memory that is then executed by the processor.
Data Execution Protection (DEP), which was introduced in Windows XP Pro SP2, and is improved in Windows Vista, can be used to prevent co-mingled data from being maliciously executed. DEP can be enabled in software, or on No eXecute (NX) processor chips, in hardware. These chips, available both from AMD and Intel, contain a hardware-based security feature that allows pages of memory to be marked as non-executable. NX-capable processors (called XD by AMD) must be accompanied by an NX-capable BIOS and mother board, and further supported by an NX-capable OS (such as Windows Vista) and applications.
By default, Windows XP Pro and later (including Windows Server 2003 SP1) system files are protected by DEP, and by NX chips if present. Software developers can also configure their applications to use DEP or NX. Administrators can use the Advanced Settings option under the System control panel applet, and then Advanced and Performance options to customize which programs to be protected (see Figure 1-1). However, many programs will refuse to run or will have operational problems if DEP or NX is enabled, so ensure application compatibility first before enabling for additional files beyond the Windows defaults.
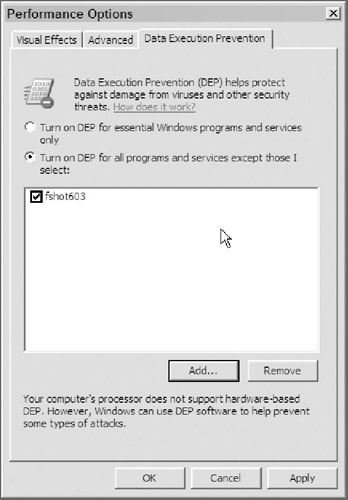
Figure 1-1: DEP can be enabled for all processes that are not specifically exempted.
| Note | NX-enabled software is also available in other operating systems, such as Linux and BSD. See http://www.en.wikipedia.org/wiki/NX_bit for more details. |
EAN: N/A
Pages: 163