Defending Against Password Attacks
With password hacking so prevalent, what's a network administrator to do? The typical Windows administrator can institute just the first five of the following steps and significantly decrease the password-cracking risk.
Disable LM Password Hashes
One of the single best things any network administrator can do is disable the storage of LM password hashes and force users to change their passwords after LM hash storage is disabled. This can be done several ways, including registry entry and GPO policy. To enable the disabling of LM password hash storage, in the GPO or local computer object, locate the option Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Network Security: Do not store LAN Manager hash value on next password change and enable.
You can also disable the storage of LM Manager hashes by requiring all passwords to be 15 characters or longer. Unfortunately, to date, Windows only allows the maximum size of the minimum password field to be set to 14 characters. This will change in future service packs and versions of Windows. Passwords longer than 14 characters will also confound password crackers and rainbow tables. The longer your password, the more difficult it will be to crack.
You can also disable LM hash storage by using certain Unicode characters. Table 4-1 shows the Unicode Alt character codes that cause the LM hash to be disabled.
| 0128–0159 | 0306–0307 | 0312 | 0319–0320 |
| 0329–0331 | 0383 | 0385–0406 | 0408–0409 |
| 0411–0414 | 0418–0424 | 0426 | 0428–0429 |
| 0433–0437 | 0439–0447 | 0449–0450 | 0452–0460 |
| 0477 | 0480–0483 | 0494–0495 | 0497–0608 |
| 0610–0631 | 0633–0696 | 0699 | 0701–0707 |
| 0709 | 0711 | 0716 | 0718–0729 |
| 0731 | 0733–0767 | 0773–0775 | 0777 |
| 0779–0781 | 0783–0806 | 0808–0816 | 0819–0893 |
| 0895–0912 | 0914 | 0918–0919 | 0921–0927 |
| 0929–0930 | 0933 | 0935–0936 | 0938–0944 |
| 0947 | 0950–0955 | 0957–0959 | 0961–0962 |
| 0965 | 0967–1024 | ||
| Table from Microsoft's Windows 2000 Security Hardening Guide (www.microsoft.com/technet/security/prodtech/windows2000/win2khg/03osinstl.mspx). | |||
As with any security advice, test thoroughly before implementing in a production environment. Many applications still rely on the LM hash, although most environments will not have any problems. Certainly continue using LM hashes if you have DOS, Windows 3.x, or other unpatched legacy systems in your environment. If you communicate with Unix/Linux clients using Samba, Samba may require LM hashes.
Require Long, Complex Passwords
Require long, complex passwords for all passwords in the enterprise. This means passwords that are at least 15 characters long, and contain at least one non-alphanumeric character. Consider requiring that highly privileged accounts, such as Administrator, have one non-keyboard character (although if the password is sufficiently long, no complexity is needed). If the password exceeds 15 characters, the likelihood of any password cracker finding it, even when no complex characters are involved, is remote.
Disable LM and NTLM Authentication
All Windows machines 2000 and later should use Kerberos and one other form of authentication. Disable LM and NTLM authentication options and force the computer to use secure NTLMv2 authentication when Kerberos can't be used. This can be done using a registry edit or group policy. In a GPO or local computer policy, find Computer Configuration\Windows Settings\Security Settings\\ Local Policies\Security Options\Network Security: LAN Manager Authentication level (see Figure 4-19). Choose the most restrictive setting possible—you'll need to test before implementing in your environment. If you can enable Send NTLMv2 response only/refuse LM & NTLM, you'll significantly reduce risk from network-sniffing password crackers.
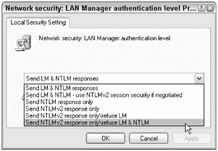
Figure 4-19
Enable Account Lockouts
Enable Account Lockouts. Located in a GPO or local computer policy at Computer Configuration\ Windows Settings\Security Settings\Local Policies\Account Lockout Policy, it was created to prevent password-guessing attacks, manual or otherwise. When Account Lockouts is enabled, after a predetermined number of bad passwords are consecutively entered on a single security principal, the Windows Account Lockouts feature can disable the account for a predetermined amount of time or require an admin to re-enable it.
Microsoft is beginning to recommend that Account Lockouts not be enabled. Their reasoning is that if passwords are complex enough, then complexity alone will defeat guessers, and Account Lockouts is not needed. They are also worried about manipulative hackers or password-guessing worms using the Accounts Lockouts feature to cause a self-caused denial-of-service attack. I agree. But unfortunately, Microsoft has yet to provide us with tools that ensure that our passwords are really complex. As discussed at the beginning of this chapter, it is easy to make insecure passwords even when password complexity is enabled. The password Password2 would meet complexity requirements and it isn't very complex.
Instead, I recommend enabling Account Lockouts, using the following settings:
-
Set the Account lockout threshold to a certain number of acceptable bad password attempts—say, 3 to 5.
-
Set the Reset account lockout counter after to 1 minute (the smallest it can be).
-
Set Account lockout duration to 1 minute.
If someone types in a bad password too many times, they only have to wait a minute until it is reset. Having Account Lockouts enabled and set to anything defeats password guessers. Password guessers have to cycle through dozens to hundreds of passwords (it is hoped) to find the right one, sometimes thousands. By enabling Account Lockouts, you make the computational time too long. As far as a computer worm causing a denial-of-service attack is concerned, if I've got a computer worm guessing at passwords using all my users' logon names, I want regular users locked out until the computer worm is stopped anyway. And when the worm is gone, all user accounts enable in 60 seconds.
| Note | Usually you cannot lock out the Administrator account using Account Lockouts. This is a good thing. Who wants a hacker locking out the Administrator account? However, if you wish, you can enable Account Lockouts using Microsoft's Passprop utility (www.dynawell.com/reskit/microsoft/win2000/passprop.zip). I recommend not enabling this feature, as you should always have at least one account that cannot be locked out, to prevent a hacker from intentionally locking everyone out of the network. |
Force Moderately Frequent Password Changes
Using group policy, set Computer Configuration\Windows Settings\Security Settings\Local Policies\Password Policy\Maximum Password Age to 90 days or less. Given enough time, any password guesser, cracker, or rainbow table would be able to defeat any password. The key is to change the password more frequently than the time needed by the attacker. Some high-security organizations force password changes at 30, 45, or 60 days. Any reasonable interval can be argued—just don't make it too short, forcing your users to write it down. Ninety days or less seems reasonable for most organizations.
Rename Highly Privileged Accounts
As discussed before, highly privileged accounts, such as Administrator, should be renamed to something inconspicuous. Be sure to remove the default descriptions. Then create bogus accounts with the original account's name and give them long and complex passwords. Turn on auditing (or Per-User Selective Auditing) to track password guess attempts against those bogus accounts. Yes, hackers can do SID enumeration, but most don't and automated password-guessing worms never do.
You can automate renaming the local Administrator and Guest accounts using group policy. You can change the names at Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Accounts\Rename administrator account and Rename guest account. This renames only the local accounts, not domain admin accounts.
Give Additional Protections to Highly Privileged Accounts
Highly privileged account passwords deserve more protection than most of the passwords on your network. Besides making admin passwords extra long and complex, consider these other recommendations:
-
Change the password more frequently than normal passwords.
-
Only use your most highly privileged accounts on trusted computers. You want to ensure that a hardware keyboard logger or trojan isn't intercepting the password.
-
Use different passwords for your different administrative accounts. Your local administrator password should not be the same as your domain or enterprise admin password, and so on. Your Directory Services Restore Mode admin password should be different than all of the rest (and known by fewer admins).
-
Separate domain admin and enterprise and schema admin roles (don't give both to same user account).
-
Consider splitting up single passwords into two password halves, so that no single user has the entire password. This would force collusion to use the accounts, and fired employees would never have the passwords to attack the company with. If you use this option, the whole password should be written down and stored in two different, safe locations by an independent third party.
-
Consider requiring smart cards or biometrics for admin logons.
-
Don't forget to change passwords on the Directory Services Restore Mode admin account occasionally.
| Note | Microsoft has an excellent password guide for highly privileged accounts, called Microsoft Solutions for Security: The Administrator Accounts Security Planning Guide (www.microsoft.com/technet/security/topics/serversecurity/administratoraccounts/default.mspx). |
Enable Logon Screen Warning Messages
As discussed above, logon screen warning messages defeat many brute-force password-guessing programs. You can enable logon screen warnings in group policy at Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Interactive logon\ Message text for users attempting to logon (and the related Message title for users attempting to logon).
Audit Passwords on a Regular Basis
Do it before the password hacker does. Using some of the tools in this chapter (e.g., Pwdump4 and John the Ripper or Cain & Able), scan for weak passwords on a regular basis. This will help you to ensure that users are using sufficiently long and complex passwords, identify areas of improvement, and document compliance.
Consider Using Random Password Generators
If passwords are long and complex enough, it defeats most password crackers. Consider using a random password generator to generate random-looking passwords if you are in a high-security environment. Unfortunately, unless the user runs this process, it defeats the purpose. If the administrator runs the random generation process and hands out the password, it immediately defeats the purpose of the password (uniquely known to prove identity). Also, users don't like inputting randomly generated passwords. You can find random password generators all over the Internet. An interesting site to visit is Funk's Password Amplification (www.funk.com/radius/enterprise/pass_amp.asp). It includes free software that takes a user's easy-to-guess password and attempts to make it more complex and harder to crack but not overly hard for the user to remember.
Don't Use a Password
Use two-factor or token-based authentication instead. Passwords alone will always be susceptible to compromise, if only from social engineering attacks, Two-factor authentication, smart card, USB token, biometric, asymmetric tokens, or other stronger authentication schemes should be considered where the value of the data warrants. These authentication methods invite their own sets of problems, but entities that replace passwords with stronger authentication methods where possible decrease their risk of successful attack.
EAN: 2147483647
Pages: 122