Other Types of Password Attacks
There are a lot of password mechanisms in Windows, which means a lot of passwords to be used and stored. A password cracker looks for passwords anywhere they can find them. Here are some common Windows password mechanisms and locations…
Cached Credentials
By default, Windows 2000 and later computers will locally cache the last 10 domain user credentials used to log on to a domain. Windows will allow up to 10 different user profiles to log on using cached credentials if the domain controller isn't available. The last 10 user profiles will be allowed to log on as many times as their want without interruption. Microsoft created cached credential storage in case the domain controller was down or too busy to respond. It is the cached credential feature that allows laptop users logged into their domain accounts to unplug from the network and continue to log onto their laptop, using their domain accounts (of course, any network resources will not be available).
Cached credentials are stored in the registry key HKLM\Security\Cache\NL$n, where n represents a number between 1 and 10. Cached logon passwords are not stored in clear text. They are encrypted using DES, RC4, and HMAC_MD5 cryptology algorithms, and the password hash is even salted with the user's username in Unicode form. These cached password hashes can be recovered and cracked using a program capable of cracking cached credential hashes. The domain Administrator account is almost always one that is present in the cache. This means a local admin can recover the domain admin's password. Recovering cached credentials is especially useful on shared or kiosk machines.
Cachedump (www.off-by-one.net/misc/cachedump-1.1.zip) is one such utility. It works by starting a new service on the fly and reading the Lsass.exe process' static encryption key from memory. The stolen key is then used to extract the cache credential values. In order for Cachedump to work, you must be logged on locally as an administrator and run the program from a local drive. Of course, there must be cached credentials to discover.
When successful, Cachedump returns the name and password hash of the cached credentials (see Figure 4-14). The extracted password hashes are not the same as the LM or NTLM password hashes, and they can only be converted to their plaintext password equivalents using a password-cracking tool that understands cached credential password hashes. John the Ripper (www.openwall.com/john), one of the best and most popular password hash crackers, can be modified to crank on cached credential password hashes (www.banquise.net/misc/patch-john.html). Also, although it is not readily apparent, two of the user accounts in Figure 4-14 share the same password, but you can see that all the password hashes are different. This is due to the salting, which, unfortunately, is not done with the normal LM and NTLM password hashes.
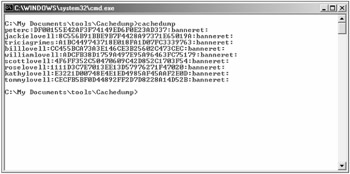
Figure 4-14
The cached logon feature can be disabled or limited using a GPO or registry entry. The number of cache logons allowed is set in the registry key HKLM\Software\Microsoft\Windows NT\CurrentVersion\ Winlogon\cachedlogonscount. In GPOs, you can find the similar setting at Computer Configuration\ Windows Settings\Security Settings\Local Policies\Security Options\Interactive logons: Number of previous logons to cache (in case domain controller is not available). The default value is 10. If set to 0, it disables cache logons all together. You should either disable cached logons or limit them to a smaller number of accounts—say, 1 to 3. Disabling cached logons completely might cause troubleshooting problems if the domain controller is down.
Computer Accounts
Don't forget that domain computer accounts also have logon names and passwords, although the passwords and password changes (every 30 days by default) are controlled by the domain controller. As shown in Chapter 3, computer accounts belong to many security groups by default, including the Everyone and Domain Computers group. There hasn't been a reported instance of a computer account and its password being used to compromise a network, but theoretically it could be done.
Service Accounts
Service accounts are normal logon accounts just like user accounts, but they have the Log on as a service user privilege. This allows the service account to log on and authenticate soon after Windows starts and prior to any user logging on. It also gives the service controller manager (Sc.exe) the ability to initiate each service account's logon and authentication. Each service account logs on using a logon credential as defined in its Log On tab in the Services console (Figure 4-15 shows an example).
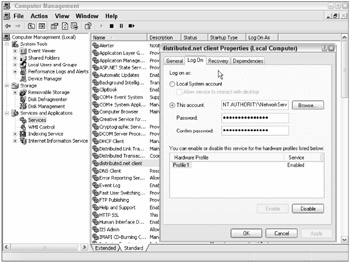
Figure 4-15
Most services use local SAM accounts, although some services may use domain-based accounts. Domain-based service accounts can use any authentication protocol to authenticate, including Kerberos. Most service accounts are installed when Windows is installed, and most use the highly privileged account Local System (although XP and later added LocalService and NetworkService service accounts and they are becoming more popular). Additional service accounts can be made manually, but most new service accounts are made when the administrator is installing software that requires a service account (such as tape backup software).
Service accounts are unique in that their logon names and passwords are not only stored in the local SAM or Active Directory database but also in local protected storage on the computer where the service resides. The local protected credential database is known as LSA secrets. The LSA stands for link state algorithm and the Lsass.exe process controls access to and from the LSA secrets. The LSA secrets storage area is located in the registry at HKLM\Security, but it normally isn't accessible to any user, even a local administrator—although if you can get in as Local System you can usually access it.
The LSA secrets storage area stores many things, including service account names and passwords, RAS credentials, dial-up networking account credentials, and FTP passwords. When you change a service account's password, you must change it in two places: the authentication database and the LSA secrets cache. Custom service account passwords (and many other passwords) are stored in plaintext in the LSA secrets cache storage area.
| Note | You cannot easily change the password of the default three service accounts (i.e., LocalSystem, LocalService, and NetworkService) and you should not manually change those passwords. |
Infamous whitehat hacker programmer Todd Sabin created the excellent Lsadump2 tool (www.bindview.com/Services/razor/Utilities/Windows/lsadump2_readme.cfm) for dumping the LSA secrets. Figure 4-16 shows Lsadump2 in action. Lsadump2 will dump the LSA secrets cache to screen although the information can be piped to a file for later analysis; for example:
Lsadump2 >lsasecrets.txt
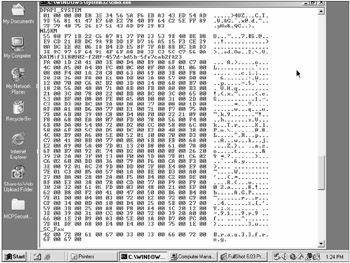
Figure 4-16
In order to use Lsadump2, you must be logged in interactively on the machine you wish to examine and have the Debug Programs user privilege, which usually only administrators have. Lsadump must be executed from a local directory (it does not work over remote network drive shares). If successful, it dumps the LSA secrets in a somewhat raw format that can be a little difficult to decipher at first glance. Information is dumped a secret at time. The service account names and other names (e.g., RasCredentials) found are on the left (often followed by the SID). Service account names will often begin with _SC_. In Figure 4-16, the Fax Service service account name is _SC_Fax. Its password follows: B.r.a.g.3.3.f.r.o.g. You need to remove the separating periods to reveal the true password of Brag33frog. The service account's name will not be visible, so you have to go to the Services console and review the service's Log On tab to discover the service account's name.
If you need to be logged in as administrator in order to run this utility, you might wonder what benefit dumping the LSA secrets cache gives you. First, many, if not most, service accounts have full administrator privileges to the entire domain. This is certainly true of tape backup and antivirus service accounts. Plus, SQL server service accounts are also stored here. Thus, by simply being a local administrator (or regular user account with Debug Programs privileges), you can find out domainwide administrator accounts. And because changing passwords in service accounts requires two password changes for every service account, most administrators never change their passwords. What a juicy target: highly privileged, domainwide accounts with passwords that rarely change. It's a password cracker's dream.
There are other password-cracking tools besides Lsadump2 that can dump the LSA secrets cache store, including Cain & Able. Lsadump2, and other tools like it, do not appear to work well on XP Pro Service Pack 2 or Windows Server 2003 Service Pack 1 and later machines. Microsoft must be addressing the weaknesses that allow these types of tools to work.
Credential Manager
Starting with Windows XP, Microsoft created a new password management mechanism called Credential Manager. It is used to store all sorts of other Windows password credentials (logon name and password), including those for drive shares, web sites, the RunAs/SaveCred feature, and .NET. Essentially any application that wants to use it can use it. The application need only use the Credential Manager API, and the Windows Credential Manager will securely store the passed credentials, and retrieve them when prompted.
Most users and administrators don't even know it exists, but if they have ever said yes to saving a password for automatic logging on, they have probably used it. To access the Credential Manager, a user needs to go to the User Accounts control panel applet and choose the Advanced tab, and then select the Manage Passwords button (see Figure 4-17). There the user can view, edit, and delete saved credentials. You can also use the third-party utility ClearCredCache (www.harper.no/valery/ct.ashx?id=deba3b20-9d29-440f-b7bb5a61c50bd99d&url=http%3a%2f%2fwww.harper.no%2fvalery%2fcontent%2fbinary%2fClearCredCache.zip), written by a Microsoft MVP, to quickly clear all credentials.
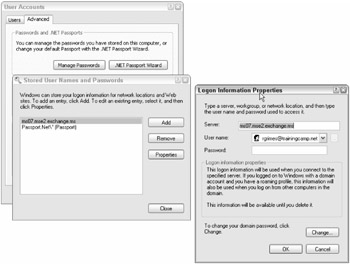
Figure 4-17
The protected credentials are stored in the user's profile (local or roaming) at \Documents and Settings\%Username%\Local Settings\Application Data\Microsoft\Credentials\ %UsersSID\Credentials or at \Documents and Settings\%Username%\Application Data\Microsoft\Credentials\%UsersSID\Credentials. These file locations aren't easily accessible to the normal end user.
Data Protection API
The Credential Manager credential database is protected by Microsoft's Data Protection API (DPAPI). DPAPI replaces Microsoft's earlier protection mechanism called Protected Storage. DPAPI protects other things besides the Credential Manager database, such as EFS private keys, S/MIME certificates, and other digital certificates. DPAPI uses a master key to protect valuable authentication credentials. The master key is at least 512 bits long, but in Windows Server 2003 domain controllers (at native domain mode or higher) it is 2,048 bits in length. By default, the master key is changed every 90 days.
Even though DPAPI is a secure, reliable technology, like the logon credential cache, the Credential Manager cache is exploitable by a logged on user with administrative permissions. You can use Cain & Able to view the saved credentials in clear text (see Figure 4-18) or use its stand-along utility, CredDump (www.oxid.it/creddump.html).
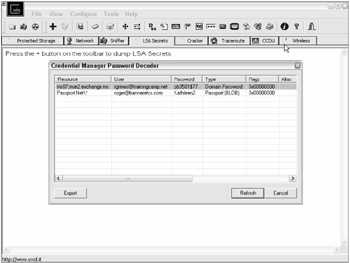
Figure 4-18
Because stored credentials are often common among varying resources (the logon name and password used in one location is often used in multiple places), finding a password here can lead to wider exploits.
RDP Connection Objects
The Remote Desktop Protocol (RDP) is used to connect to several Microsoft Terminal Services technologies, including Terminal Services, Remote Desktop, and Remote Assistance. If an RDP connection is made frequently, Microsoft allows an RDP Connection object (click Start ð All Programs ð Accessories ð Communications ð Remote Desktop Connection) to be created so that in the future the user need only click on the icon to launch an RDP connection. RDP traffic is encrypted by default so that the remote logon password is never sent in clear text.
Although it is not the default, users can save their remote logon password with their connection object so that they do not need to enter the password to connect. If the password is saved, the Cain & Able program, using its RDP Decoder feature, will quickly reveal any saved passwords. It will reveal any RDP connection stored password in seconds, regardless of its complexity or length. An intruder would need local administrative access to use the RDP decoder, but the process is simplified greatly using Cain & Able. For this reason, you should not store passwords with your RDP connections.
Windows 9x and ME logon passwords are stored in PWL files using RC4 encryption. There are several password-cracking tools that will attempt to recover the passwords stored in PWL files, including Advanced Windows Password Recovery (www.tomdownload.com/utilities/security_encryption/advanced_windows_password_recovery.htm), Pwl Tools (http://lastbit.com/vitas/pwltool.asp), and Unix-based Windows 9x Password List reader (http://freshmeat.net/projects/pwl9x). If attackers can't recover user passwords from PWL files, they can delete the PWL file (essentially getting rid of the password protection) or create their own PWL files (just search on "PWL file creation" using any Internet search engine). PWL files are not used in Windows NT, 2000, XP, or later.
Other Common Windows Authentication Mechanisms
There are many other authentication mechanisms in Windows, including IIS logons, Password Reset Diskettes, and a plethora of other options.
IIS Logons
Windows logon authentication also occurs with IIS authenticated logons. If an IIS web site is not selected to require anonymous logon authentication, a connecting Windows client might send its current user credentials using LM, NTLM, NTLMv2, or Kerberos authentication. In Internet Explorer 6, the browser will only send anonymous credentials to non-intranet servers (see Figure 4-6 again), and will prompt the user before it sends non-anonymous credentials. On web sites (legitimate or not), the user's current credentials will be sent by default (older IE versions sent authenticated credentials by default to all IIS servers, even the ones requiring anonymous connections).
Other places that Windows users may be required to type in logon credentials is RRAS connections, locked screensavers, SQL databases, Outlook and Outlook e-mail connections, and SharePoint services. Passwords, although not logon passwords, are used for setting up Windows trusts, Cluster Services, and IAS client server connections. Passwordlike pre-shared keys (PSK) are used in IPSec, Radius, WEP, and 802.1x communications.
Password Reset Diskette
Stand-alone XP Pro systems can also store their local logon password on a diskette, called the Password Reset Diskette. It can be used when the user doesn't remember her current password to reset the password back to a previous password saved on the disk. When enabled (it's enabled in the Ctrl+Alt+Del dialog box), the user will be prompted for their Password Reset Diskette whenever they type in their password wrong. It's also a clue to a local intruder to look for the diskette when trying to do a local logon attack. To date, there are no publicly known crack attacks against the credentials stored on the diskette.
Password Authentication Mistakes
The media frequently reports on passwords sent in plaintext across the network, plaintext passwords visible in temporary files, or default blank passwords. Although Microsoft was famous for leaving plaintext passwords in temporary files, they have gotten significantly better over the years. Still, Dr. Watson memory dumps often contain plaintext passwords or password hashes.
In July 2005, SecuiTeam (www.securiteam.com) revealed that Dell-installed XP Pro computers have a hidden administrator account with a blank password (www.securiteam.com/windowsntfocus/5KP091PGBO.html). Many popular programs have been caught with password mistakes. For instance, although Microsoft Word allows a document to be password protected, at least two flaws have been found in Word's password protection scheme.
The first flaw is that Word uses RC4 symmetric encryption but does not randomly change what is called the initialization vector (IV) between document saves. This is a basic crypto flaw. It allows someone to save a protected identical document twice, and when the two documents are compared to each other using an XOR algorithm, the RC4 symmetric encryption key is rendered (www.schneier.com/blog/archives/2005/01/microsoft_rc4_f.html). The second issue is that any protected Word document can be opened in a text editor and the password simply blanked out (www.tech-faq.com/wordpassword-recovery.shtml). Microsoft is far from the only vendor to have problems with cryptographic routines, but it shows that even the largest companies with the best resources make mistakes. Creating new cryptographic routines takes extensive expertise, testing, and competent reviewers.
Let's not forget all the other places where passwords can be used and stored. Many web sites require logon names and passwords. Computers can require bootup or BIOS configuration passwords. PDAs and cell phones can have passwords. Routers and network devices have passwords. Many applications like Microsoft Office have passwords.
Island Hopping
The reason all these other passwords matter is that users often use the same or nearly identical passwords across multiple locations. The network administrator might institute the strong password protections possible in the world, but if the user uses the same password to manage their e-Bay account or to purchase online porno, the strength of the password is only as strong as every place it is stored. Hackers frequently setup bogus web sites asking users to establish login names and passwords. Then those credentials are used to break into the employee's work site, which they happily provided when applying to the online web site. When a hacker learns about a password in one location and uses it successfully to compromise a new location, it is called island hopping.
Create a password policy and encourage your users to use different passwords for personal use than they use at work. Consider requiring different passwords for the computer resources with the most value in your organization. Having separate passwords for different applications on the same network is counterintuitive to the single-sign-on push occurring in most organizations, but ease of use has to be measured against the subsequent risk from password island hopping.
EAN: 2147483647
Pages: 122