Counteracting Intrusion
When hackers become bored with a manual search for security holes, they start automated tools.
One such automated tool is Security Scanner, developed by the Application Security and intended for testing MySQL security (Fig. 28.4). Like any security tool, Security Scanner can be used both for benign and for harmful purposes.
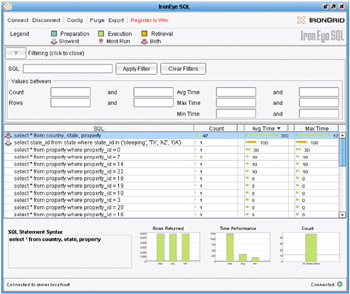
Figure 28.4: The toolset for monitoring SQL servers. Without using such tools, an attacker has no chance of remaining unnoticed
It allows hackers to detect security holes both in database servers and in Web scripts. A database server is tested for vulnerabilities to DoS attacks, the presence of weak passwords, incorrect configuration of access rights, etc. The scanner also detects filtering errors in scripts (recall that filtering errors allow SQL injections, thus considerably simplifying attack implementation).
Shellcoders Programming Uncovered (Uncovered series)
ISBN: 193176946X
EAN: 2147483647
EAN: 2147483647
Year: 2003
Pages: 164
Pages: 164
Authors: Kris Kaspersky