AUTOMATED SERVER CREATION
| | ||
| | ||
| | ||
Since much of the work needed to create and maintain a user 's desktop is mitigated by moving to a Terminal Server/Presentation Server environment, the main job of building IT infrastructure becomes that of server and network configuration. Although many organizations intend to standardize the server build process, few can accomplish this goal by merely writing install instructions. The TSE build process, including the application installation, typically will incorporate hundreds of manual steps and is thus prone to installation errors and omissions. As the number and frequency of new servers and applications increases , the task of building and maintaining the servers becomes quite onerous. The other problem is one of change control and consistency. Unless there is a standard method for building a server, a myriad of problems are bound to crop up. These can include DLL library conflicts, application version differences, application optional component differences, and driver conflicts. In this section, we will introduce two methods to address this task: server imaging (also referred to as cloning) and unattended scripted installs . Though they are not mutually exclusive, they do each have a different focus.
Imaging is the process by which a standard collection of software components is defined, tested , and certified. This collection includes the operating system, the applications, utilities, and any system configuration changes necessary to make the system work, as shown in Figure 11-1. A system image is often created using a third-party utility such as RES Wisdom, Symantec Ghost Corporate Edition, and Symantec PowerQuest DeployCenter software. These programs allow great flexibility in how the image gets loaded on a target system. Options include creating a self-loading image on a media set like a bootable floppy disk and CD-ROM, or creating a software distribution server in which the same image can be deployed to multiple target servers. Using such products can speed up the loading process by orders of magnitude. The imaging method for bulk server creation has the following advantages:
-
– The imaging process requires no programming or scripting knowledge.
-
– Multicasting an image to multiple target servers saves time and is a standard feature of most server imaging products.
-
– Imaging can save on backup space, backup window time, and server restore time. By saving the images from the critical servers each night, there is no longer a need to include the server OS and applications in the backup job, although it is important to back up the imaging server on a regular schedule (for instance, once per week).
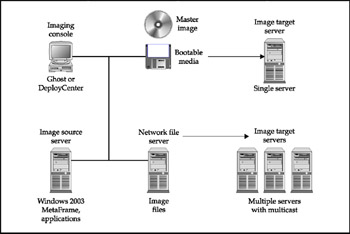
Figure 11-1: Imaging
These are among the limitations of imaging:
-
– An image is specific to each hardware type. Differences in NICs, video cards, array controllers, and manufacturers are difficult or impossible to handle within a simple image. Thus multiple images are often required and can be time-consuming to maintain.
-
– It is difficult to track all the components and configuration changes that go into an image. For example, many large enterprise applications have several options that can be chosen during installation that affect how the application will run. Unless all of these options are recorded, there is no way to be sure which were chosen when the image was created.
-
– After the image is successfully installed on a target computer, information that is unique to the computer must be changed. This information includes the system identifier (SID), IP address, and so on.
Scripting the bulk server creation process involves the creation of recorded software packages that can be replayed on target servers, as shown in Figure 11-2. A package can simply be the standard application software setup program that runs unattended with a predefined answer file, or it can be a proprietary set of software components and system configuration changes created with a commercial software packaging program such as Citrix Installation Manager (IM). One server acts as a deployment host and contains the software packages. Windows Scripting Host can be used to replay the packages and make any needed configuration changes the same way on all servers. Optionally, a tool such as IM from Citrix can be used to create application packages. IM has its own facility for distributing these packages. The scripting method of bulk server creation has the following advantages:
-
– One build can support different hardware types.
-
– Microsoft supports scripting.
-
– A high degree of flexibility for loading applications, service packs , utilities, and making configuration changes is possible with scripting.
-
– A single application can be changed and deployed without significantly affecting the actual deployment script.
-
– It provides consistency at the OS level across all configured builds. This consistency helps provide stability for the entire environment.
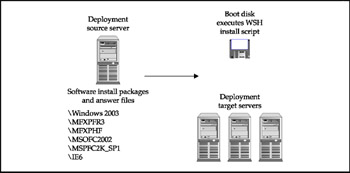
Figure 11-2: Scripting
This method has these limitations:
-
– If anything other than a commercial package such as IM or Microsoft System Management Server (SMS) is used, knowledge of scripting is required. Though we feel the effort is justified, learning VBScript or JScript requires a higher level of commitment than simple batch programming.
-
– Areas of the operating system, such as the \wtsrv directory, must be granted read/ write access for all users in order for the scripts to run. Though these security holes can be closed later, this must be taken into account during the server build process.
The two methods for building servers, using an imaging product and scripting, are not mutually exclusive. In fact, they can be used together quite effectively. We will discuss an example of this later in the chapter.
Imaging Products
Symantec now owns both the Ghost and PowerQuest imaging products.
Both products have unique features. However, a simple, generalized procedure for creating a disk image can be abstracted. First, to create a disk image, follow these steps:
-
Boot to the network with the boot CD-ROM or floppy. This floppy is created manually or with utilities from Symantec or PowerQuest. The boot disk will map a network drive for storing images.
-
Once booted , run the imaging client program from the floppy or from the mapped network drive.
-
Select Disk To Image from the client interface.
-
Choose a location on the network to store the file and proceed.
To load a disk image, follow these steps:
-
Boot to the network with the boot floppy from the target computer.
-
Once booted, run the imaging client program from the floppy or from the mapped network drive.
-
Choose Image To Disk from the client interface.
-
Choose the correct image file from the network drive and proceed.
-
Remove the boot CD-ROM while the target computer is being imaged so that it will reboot from the local hard drive once imaged .
Microsoft Support
To overcome some of the postinstallation configuration problems that can crop up, Microsoft created a System Preparation Utility (SPU) for Windows NT, and Microsoft continues to support system cloning with Windows 2000 and 2003 with Sysprep version 1.1. The release of these tools coincides with Microsoft's public endorsement of cloning technology. The Windows SPU provides each cloned PC with a unique system identifier (SID). It provides a Registry entry that Microsoft technical support can use to determine whether a system has been cloned. We have used these products many times with no trouble for server cloning. We also know firsthand of at least two major PC hardware manufacturers that use cloning products internally.
EAN: 2147483647
Pages: 137
- Understanding SQL Basics and Creating Database Files
- Using SQL Data Definition Language (DDL) to Create Data Tables and Other Database Objects
- Using SQL Data Manipulation Language (DML) to Insert and Manipulate Data Within SQL Tables
- Working with Comparison Predicates and Grouped Queries
- Working with Ms-sql Server Information Schema View