Four Layers of the DoD Model and the TCPIP Protocol Suite
Four Layers of the DoD Model and the TCP/IP Protocol SuiteBefore we get into layers and protocols, you need to know about ports , a concept that will come up repeatedly in TCP/IP. A port number identifies a sending or destination application. Every application running on a host uses certain ports or ranges of ports to communicate with applications running on other hosts . It is by these port numbers that TCP or UDP determines which application to pass the data to in the Application layer. The well-known ports have a value between 0 and 1,023. When an application on one device wants to communicate with an application on another device, it must specify the address of the device (IP address) and identify the application (port number).
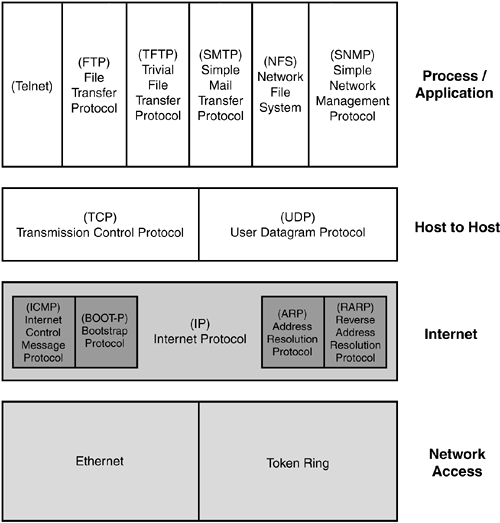
Let's start by looking at the specific functions and protocols of each of the four layers. In Figure 5.1, we will look at how those layers and protocols map to the OSI model later in the chapter. Figure 5.1. The four layers of the DoD model and associated protocols from the TCP/IP suite. Process/Application LayerThe first layer of the model is the Process/Application layer. This layer is where applications actually have to do something with the data once it is received. It is important to note than any software application that uses the TCP/IP suite ”such as Internet Explorer, Outlook Express, or Adobe Acrobat Reader ”needs to communicate with the correct port for that application process on a receiving computer. That is why these processes use well-known public port numbers. Noteworthy to mention is that the sending port and receiving port do not have to be the same, and generally are not the same. This layer also consists of a set of services that provides access to all types of networks. Applications utilize the services to communicate with other devices and remote applications. A large number of TCP/IP services is provided at the Application layer, some of which were mentioned previously. In the following sections, you will see a list of several Application layer protocols and their associated port numbers. File Transfer Protocol (FTP)FTP is used to copy a file from one host to another host, regardless of the physical hardware or operating system (OS) of each device. FTP identifies a client and server during the file transfer process. In addition, it provides a guaranteed transfer by using the services of TCP. The services that TCP provides are explained in more detail in the "Transport Layer" section of this chapter. FTP uses port 20 or 21 to deliver files. Trivial File Transfer Protocol (TFTP)TFTP was built to be a small, robust FTP service. The original goal was to develop a protocol that could fit into the limited read-only memory (ROM) space of diskless machines. TFTP is a connectionless protocol that uses the services of UDP for transport. TFTP is used to copy files from one host (server) to another host (client). In many cases, TFTP is used to copy software to a device as it boots up. A common use of a TFTP server is to upgrade the IOS of a Cisco router, which you hopefully have already done or will be doing soon. TFTP uses port 69. TelnetThe Telnet service allows users to act as though their terminals are attached to another device. This process is referred to as terminal emulation. Telnet is a very useful protocol in internetworking because it allows network administrators to view and configure remote devices in the network from one location. Telnet uses the services of TCP to provide a connection-oriented session. Telnet uses port 23. Simple Mail Transfer Protocol (SMTP)SMTP is used to pass mail messages between devices. It uses TCP connections to pass the email we've all grown to love between two mail servers. SMTP uses port 25. More specifically , SMTP is what allows email to get from the mail client to the mail server, whereas POP3 or Post Office Protocol is what gets mail from the mail server to the mail client. Simple Network Management Protocol (SNMP)SNMP is used to obtain data on remote devices, such as a configurable switch. Typically, a network-management station uses SNMP to poll the devices in a network and to retrieve data regarding the devices' current and past conditions. Each of the agents maintains a management information database (MIB) locally that constantly stores information about that device. The manager systematically polls each of its agents, requesting information from their databases. It then manipulates and organizes the data into a useful format for reporting or displaying on the network-management monitor. SNMP has become the de facto standard for device management and is widely used today. Domain Name ServiceDNS is a service that is used to translate hostnames or computer names into IP addresses, such as www.awsb.ca . DNS is a hierarchical database of names and their associated IP addresses. DNS allows people to enter a word-based address for any device on the Internet. When this occurs, that person's device requests a DNS lookup from a DNS server. The DNS server replies with the IP address associated with that hostname. Can you imagine if this service never existed? You would have to know the IP address of every Web site, effectively a nightmare, so be happy. DNS uses port 53. DNS has some security issues as well because it uses port 53 for both UDP and TCP traffic. Transport LayerThe next layer for us to look into is the Transport layer. The Transport layer passes data between the Application layer and the Internet layer. It consists of two protocols, Transmission Control Protocol ( TCP ) and User Datagram Protocol ( UDP ) . This layer provides an end-to-end connection between two devices, otherwise referred to as host-to-host communications, during communication by performing sequencing, acknowledgments, checksums, and flow control. The Transport layer allows the Application layer to ignore the complexities of the network and focus on its primary job. This layer is also responsible for sending data that it receives from the Network layer to the appropriate application. TCPTCP provides a connection-oriented, reliable service to the applications that use its services. TCP was designed to add some reliability into the world of IP networking. A description of the main functions of TCP follows :
UDPUDP is a connectionless protocol that will run on top of an IP network. One of the disadvantages of UDP is that it provides very few error recovery services. However, one's disadvantage is another's advantage. Because there is no error checking, UDP is considerably faster than TCP. The primary purpose of UDP is to broadcast messages over a network. UDP simply receives data from the Application layer, applies the proper header, and sends the datagram on its merry way. This is why UDP is referred to as a best-effort protocol. Internet LayerThe Internet layer is responsible for path determination and packet switching. The Internet layer utilizes a logical addressing scheme to make intelligent decisions regarding path determination and packet switching. The Internet layer performs the actual relay of packets from an originating network to a destination network in an efficient manner. Every packet is viewed by IP, which determines its destination by using a routing table. The routing table helps establish the best path for the packet to be sent. IPInternet Protocol ( IP ) is the transport for TCP, UDP, and Internet Control Message Protocol (ICMP) data. IP provides an unreliable service and is effectively a connectionless protocol. I know this is hard to imagine, but remember that the transport layer above it does all the error checking, so this layer does not have to worry about it. It lets the upper-layer protocols, such as TCP, or application-specific devices worry about reliability. In addition, IP performs as a connectionless service because it handles each datagram as an independent entity. IP performs packet switching and path determination by maintaining tables that indicate where to send a packet based on its IP address. Address Resolution Protocol (ARP)ARP is a TCP/IP protocol that is used to convert an existing IP address into a physical address. Consider a computer that wants to know the address of another computer. The computer sends out (broadcasts) an ARP request to the network. The receiving computer that owns the physical address being sought replies to the original computer that was looking for its address. Sound rather simple? It is. Reverse Address Resolution Protocol (RARP)RARP provides the exact opposite type of mapping from ARP ”that is, RARP maps a known physical address to a logical address. A diskless machine that does not have a configured IP address when started typically uses RARP. These devices send a broadcast requesting an IP address. In such a scenario, a device on the same local area network (LAN) is designed to respond to this broadcast request and supply the IP address for that physical address. Internet Control Message Protocol (ICMP)ICMP communicates error messages and control messages between devices. The ICMP protocol allows devices to check the status of other devices, query the current time, and perform other functions. The most popular use of ICMP is the use of the PING command. The PING command uses ICMP to test an Internet connection. The Ping command is an excellent command used for troubleshooting, but you probably already know that by now, don't you? The most common ICMP messages are as follows:
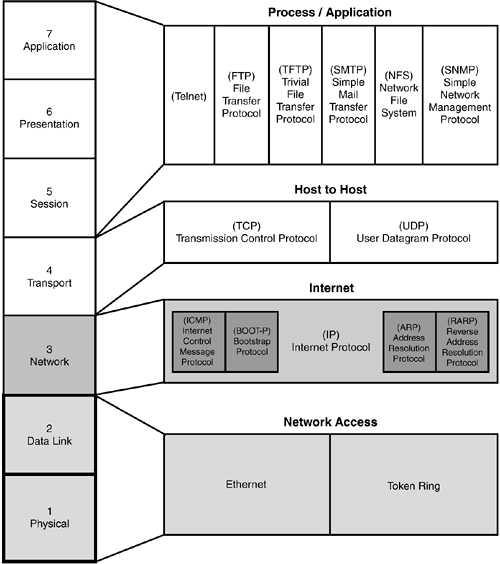
Network Interface LayerThe Network Interface Layer does just as its name implies: It works at the hardware level to define the physical transmission of signals along the network. It effectively encapsulates information into frames (remember encapsulation?) that can be transmitted across the network. This layer provides access to the LAN. The physical addressing and network-specific protocols exist at this layer. Token Ring, Ethernet, and Fiber Distributed Data Interface (FDDI) are some examples of Network Interface layer protocols, as can be seen in Figure 5.2. Figure 5.2. This graphic shows how the OSI model (left) maps to the DoD model (right). You should be familiar with how these two models relate for the test. |
EAN: N/A
Pages: 155