Certification Objective 10.04: System Logging Configuration
|
| < Day Day Up > |
|
An important part of maintaining a secure system is keeping track of the activities that take place on the system. If you know what usually happens, such as understanding when users log into your system, you can use log files to spot unusual activity. Red Hat Enterprise Linux 3 comes with several utilities you can use to monitor activity on a system. These utilities can help you identify the culprit if there is a problem.
RHEL 3 comes with two logging daemons. The kernel log daemon service, klogd, logs kernel messages and events. The syslog daemon, syslogd, logs all other process activity. You can use the log files that syslogd generates to track activities on your system. If you are managing multiple Red Hat Enterprise Linux systems, you can configure the syslogd daemon on each system to log messages to a central host system.
Both daemons are typically active by default, and they both can be activated by the /etc/rc.d/init.d/syslog script. Once these daemons start, the syslog daemon examines /etc/syslog.conf to find the logging options that you may have configured.
System Log Configuration File
You can configure what syslogd records through the /etc/syslog.conf configuration file. As shown in Figure 10-5, it includes a set of rules for different facilities: auth, auth-priv, cron, daemon, kern, lpr, mail, mark, news, security, syslog, user, and uucp.
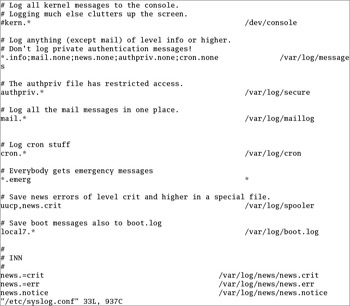
Figure 10-5: The syslog.conf log configuration file
Each facility is associated with several different levels of logging, known as the priority. In ascending order, log priorities are: debug, info, notice, warn, err, crit, alert, emerg. There's also a generic 'none' priority which logs all messages at all levels.
For each facility and priority, log information is sent to a specific log file. For example, take the following line from /etc/syslog.conf:
*.info;mail.none;news.none;authpriv.none;cron.none /var/log/messages
This line sends log information from all of the given facilities to the /var/log/messages file. This includes:
-
All facility messages of info level and higher
-
All log messages related to mail, news, authpriv (authentication), and cron
You can use the asterisk as a wildcard in /etc/syslog.conf. For example, a line that starts with *.* tells the syslog daemon to log everything. A line that starts with auth.* means you want to log all messages from the auth facility.
By default, syslogd logs all messages of a given priority or higher. In other words, a cron.err line will include all log messages from the cron daemon at the err, crit, alert, and emerg levels.
Most messages from the syslog daemon are written to files in the /var/log directory. You should scan these logs on a regular basis and look for patterns that could indicate a security breach.
Managing Logs
Logs can easily become very large and difficult to read. By default, the logrotate utility creates a new log file on a weekly basis. You can also configure /etc/logrotate.conf to compress, mail, and remove desired log files. By default, the cron daemon runs logrotate on a regular basis, using the configuration files located in the /etc/logrotate.d directory. As you can see in Figure 10-6, this process works fairly well; five or more weeks of logs are kept for a number of log facilities.
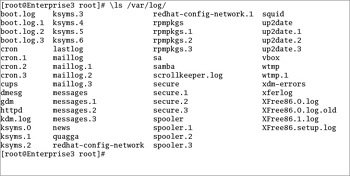
Figure 10-6: A typical set of log files in /var/log
The Red Hat Log Viewer
There is a new Red Hat GUI tool that can help you scan though applicable logs. It can be helpful if you don't remember the locations of the key log files and don't remember to look through /etc/syslog.conf for those locations. In the GNOME Desktop, you can start this tool from the console with the redhat-logviewer command or click Main Menu | System Tools | System Logs. Either option opens the tool shown in Figure 10-7.
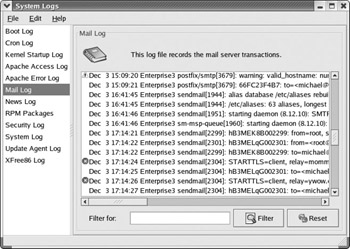
Figure 10-7: Red Hat System Log Viewer
However, this package took several minutes to load on my computer, time that you might not have during the Red Hat exams. As the Red Hat Log Viewer simply provides a front end, it's best if you know the files you need in the /var/log directory.
For example, you can review the information shown in Figure 10-7 simply by looking through the latest mail log files in the /var/log directory. And as of this writing, the regular text log files provide more complete information. On the other hand, the Red Hat Log Viewer does include warning and trouble icons that can help you identify problems with specific services. Different log files and their functionality are shown in Table 10-5. This is based on the previously described configuration of the /etc/syslog.conf file. All files shown are in the /var/log directory. As you can see, the System Log tool does not cover all log files.
Figure 10-8: The Security Level Configuration tool
| Log Files | Label in the System Log Tool | Description |
|---|---|---|
| boot.log | Boot Log | Associated with services that start and shut down process |
| cron | Cron Log | Based on scripts run by the cron daemon |
| cups/ | Not included | Directory of printer access, page, and error logs |
| dmesg | Kernel Startup Log | Basic boot messages |
| gdm/ | Not included | Directory of messages associated with starting via the GNOME Display Manager; includes login failures |
| httpd/ | Apache Access Log | Directory of log files associated with the Apache Web server |
| ksyms | Not included | Messages binding kernel modules (kallsyms for Linux Kernel 2.6) |
| maillog | Mail Log | Log messages related to the sendmail and postfix mail servers |
| messages | Not included | Messages from other services as defined in /etc/syslog.conf |
| news/ | News Log | Directory of log messages related to the Internet Network News (INN) service |
| quagga/ | Not included | Directory of routing messages |
| redhat-config-network | Not included | Actions taken through the Red Hat Network Configuration tool |
| rpmpkgs | RPM Packages | Current list of installed RPM packages |
| sa/ | Not included | List of memory usage information |
| samba/ | Not included | Directory of access and service logs for the Samba server |
| scrollkeeper.log | Not included | Log related to GNOME documentation |
| secure | Security Log | Lists login and access messages |
| spooler | Not included | Print spool log |
| squid/ | Not included | Directory of files related to Squid Proxy Server access, cache, and storage |
| up2date | Update Agent Log | Lists actions taken when you've updated your server using the Red Hat Update Agent (up2date) |
| wtmp | Not included | List of logins, in binary format; can be read with the utmpdump command |
| xdm-errors | Not included | Messages associated with the X Display Manager |
| xferlog | Not included | Log of files transferred from other computers, such as via FTP |
| XFree86 | XFree86 Log | Messages during Linux GUI start process |
| XFree86.setup.log | Not included | Setup messages for the X Window System; may include configuration problems |
Exercise 10-3: Checking Logs
In this exercise, you'll inspect the log files on your computer to try to identify different problems. You'll use the Red Hat System Log viewer, and inspect log files directly.
-
Restart your Linux computer. Log in as the root user. Use the wrong password once. Log in properly as the root user.
-
Open a GUI desktop interface.
-
Open the Red Hat System Log Viewer. Click Main Menu | System Tools | System Logs. Depending on the speed of your computer and the size of your logs, this may take a few minutes.
-
In the System Logs window, navigate to the Security Log area in the left pane. Scroll to the bottom of the screen. You should see a red 'X' with a 'FAILED LOGON' message.
-
In a console, navigate to the /var/log directory and open the file named secure. Navigate to the same 'FAILED LOGON' message.
-
Look through the other logs in the System Logs window and close this tool. Close the secure file.
|
| < Day Day Up > |
|
EAN: N/A
Pages: 194