Securing Your Host
When you secure a host, whether it is your Web server, application server, or database server, this guide breaks down the various secure configuration settings into separate categories. With this approach, you can focus on a specific category and review security, or apply security settings that relate to that specific category. When you install new software on your servers with this approach, you can evaluate the impact on your security settings. For example, you may address the following questions: Does the software create new accounts? Does the software add any default services? Who are the services running as? Are any new script mappings created?
Host Configuration Categories
Figure 1.2 shows the various categories used in Part IV of this guide, "Securing Your Network, Host, and Application."
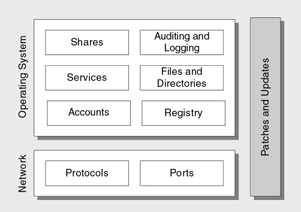
Figure 1.2: Host security categories
With the framework that these categories provide, you can systematically evaluate or secure your server's configuration instead of applying security settings on an ad-hoc basis. The rationale for these particular categories is shown in Table 1.2.
| Category | Description |
|---|---|
| Patches and Updates | Many top security risks exist because of vulnerabilities that are widely published and well known. When new vulnerabilities are discovered , exploit code is frequently posted on Internet bulletin boards within hours of the first successful attack. Patching and updating your server's software is the first step toward securing the server. If you do not patch and update your server, you are providing more potential opportunities for attackers and malicious code. |
| Services | The service set is determined by the server role and the applications it hosts . By disabling unnecessary and unused services, you quickly and easily reduce the attack surface area. |
| Protocols | To reduce the attack surface area and the avenues open to attackers, disable any unnecessary or unused network protocols. |
| Accounts | The number of accounts accessible from a server should be restricted to the necessary set of service and user accounts. Additionally, you should enforce appropriate account policies, such as mandating strong passwords. |
| Files and Directories | Files and directories should be secured with restricted NTFS permissions that allow access only to the necessary Microsoft Windows service and user accounts. |
| Shares | All unnecessary file shares, including the default administration shares if they are not required, should be removed. Secure the remaining shares with restricted NTFS permissions. |
| Ports | Services running on a server listen on specific ports to serve incoming requests . Open ports on a server must be known and audited regularly to make sure that an insecure service is not listening and available for communication. In the worst-case scenario, a listening port is detected that was not opened by an administrator. |
| Auditing and Logging | Auditing is a vital aid in identifying intruders or attacks in progress. Logging proves particularly useful as forensic information when determining how an intrusion or attack was performed. |
| Registry | Many security related settings are maintained in the registry. Secure the registry itself by applying restricted Windows ACLs and blocking remote registry administration. |
EAN: 2147483647
Pages: 613