Configuring for Internet Connectivity
| To figure the best solution for connecting your environment to the Internet, you must consider your network's current configuration and the forecast for its future. Some typical considerations are growth, security, availability, and reliability. Future growth can be built into a network by installing equipment such as routers, switches, and hubs with leftover open ports, which allows additional network devices to be quickly plugged in and configured for use as needed. Security is addressed on one level by locking rooms where switching and routing equipment are kept and by providing passwords to those devices only to those who absolutely need them. On additional levels, security is addressed by providing proper filtering of network traffic in and out of the network through the following filtering actions:
Additionally, you can further secure network resources by requiring users to authenticate before they gain any access to the network and to limit that access to users and groups based on the resources they need to perform their assigned tasks . This can be any type of limitation, from outright denial of access for resources that certain groups have no need of to allowing network logons only during permitted hours. If some network users never have a regular need to log on from 6 p.m. through 6 a.m. and all day on Saturday and Sunday, you could set logon restrictions for those users and groups. Reliability is addressed by providing redundancy where needs are the most critical. Single points of failure can exist throughout a network, but at times these single points are not acceptable. It's one thing for a print server to go down because printing queues can be restarted or, if the server suffered a terminal crash, redirected during repairs and rebuild efforts. It's entirely different when the only Global Catalog server goes offline. For most deployments, clustering or redundant servers are recommended. Clustered servers can be deployed so that a pair of physical servers (or larger cluster configurations) functions as a single virtual server. Clustering offers fault tolerance in the event of node failure, as the other node in a pair simply takes over the full load of all requests , and offers load balancing when the cluster is running in active/active mode, meaning both servers are online and servicing user requests for resources.
For Domain Name System (DNS) servers and domain controllers, having more than one of these servers available at the local site or over a WAN connection (locally is preferred) aids in fault tolerance. When one of the local servers fails, the other server running the same service assumes total responsibility for the network service being hosted. For example, assume that servers DNS1 and DNS2 are providing DNS services to a site, and some clients at that site are using DNS1 as a primary DNS server and DNS2 as a secondary DNS server. That means the other clients use DNS2 as their primary DNS server and DNS1 as their secondary DNS server. If DNS2 goes down, all clients are forced to use DNS1 until DNS2 becomes available again. Networked systems can be configured for Internet connectivity by using Internet Connection Sharing (ICS) or through an Internet Security and Acceleration (ISA) server. Network Address Translation (NAT) is actually one of the protocols available on RRAS servers, but it is also used when Internet connectivity is configured through a Windows Server 2003 system using ICS. NAT can be used to share a single IP address or a small number of external IP addresses with a larger pool of internal systems by hiding the internal private address scheme from the Internet. The device performing the NAT service, be it an ISA server, RRAS server, or even a hardware device such as a router, holds a table of mappings between internal systems and externally accessed resources and vice versa. What this means is that if you're using a host on the internal side of a NAT device and make a call to the Internet to access a remote Web site, when that Web server responds, the returning GET data makes it back to your system because the NAT device is keeping track of which internal host made the GET request of the remote Web server. The reverse is also true. A GET call is nothing more than calling for a Web page. It's the function call your Web browser makes when you enter http://www.gunderville.com and the page is rendered in the browser window; in other words, you've told the browser to "get" the index page at the URL you've entered. If your NAT device receives a remote GET call coming into your private network for a Web server that is hosted, the NAT device knows to map <PUBLIC IP ADDRESS>:80 ( :80 denotes the HTTP port number) to <PRIVATE IP ADDRESS>:80 to allow fetching the Web site.
Internet Connection Sharing (ICS) also uses NAT when it is the main Internet connection point for a home or small office. All other systems on the small LAN use the one system configured for ICS as an access point (think "router" or "default gateway") to the Internet. This is accomplished by allowing the system configured as the ICS point to obtain the necessary DHCP or fixed external IP address for access to the Internet. Also, clients on the LAN must use IP addresses from the private IP address ranges, which allows them to connect to the ICS system and route calls to the Internet through its installed interface. The private range of IP addressing assigned to clients using an ICS system is assigned directly from the ICS system. This includes any necessary DNS information as well.
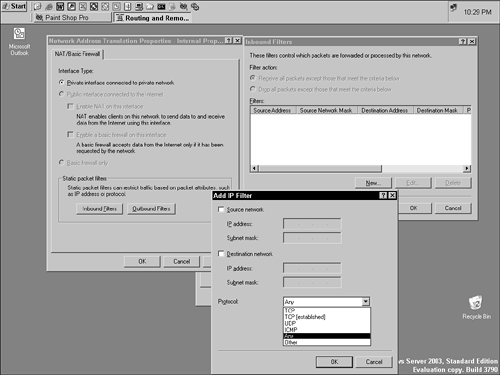
An administrator must set up and configure an interface for NAT when it is used for RRAS. To do this, right-click NAT/Basic Firewall in the Routing and Remote Access MMC tree pane, and then choose New Interface. Under Interfaces, select the interface you want to add, and then click OK. You are then left with a couple of options. If the chosen interface is connected to the Internet, select the Public Interface Connected to the Internet radio button and click the Enable NAT on This Interface check box in the NAT/Basic Firewall tab. In a high-security environment, you should make sure your public interface is protected with packet filters by selecting the Enable a Basic Firewall on This Interface check box. If this interface connects to a small private network, select the Private Interface Connected to Private Network radio button in the NAT/Basic Firewall tab instead (see Figure 4.9). Figure 4.9. The Add IP Filter dialog box enables you to add a new filter to control which packets are accepted and forwarded or denied by the filter. Under Routing and Remote Access Services in the Routing and Remote Access MMC tree pane, you can find the NAT/Basic Firewall Service installed by default in the IP Routing section. Right-click NAT/Basic Firewall Service and choose Properties to review general information that includes the default event log setting of Log Errors Only. You can change this setting to Log Errors and Warnings, Log the Maximum Amount of Information, or Disable Event Logging. In the Translation tab, the default setting for Remove TCP Mapping After (Minutes) is set to 1440 (24 hours) and Remove UDP Mapping After (Minutes) is set for 1 minute. In the Address Assignment tab, you can set the NAT configuration so that clients are automatically assigned IP addresses by using DHCP addressing. To do this, select the Automatically Assign IP Addresses by Using the DHCP Allocator check box. One of the features of Microsoft ISA Server is that it can function using NAT, just like RRAS and ICS. ISA Server can also use NAT to connect a private LAN to the Internet while protecting private network resources and internal IP addressing schemes from external access. It supports many additional features in an effort to ensure extra security for LANs. ISA Server Enterprise Edition can be used in a cluster deployment to provide fault tolerance and load balancing and has the following additional security features:
After you have implemented the method your enterprise is going to use for configuring Internet connectivity, there is always the issue of troubleshooting connectivity problems. In many instances, the tools included in the TCP/IP suite can be used to assist with troubleshooting any network connectivity problems, through the LAN or WAN and even over the Internet.
You can also use Network Monitor to view and detect problems on LANs. Network Monitor is not installed on Windows Server 2003 by default. If you want to use it, perform the following steps:
As with most component additions to a system, you must be a member of the Administrators group or have been delegated the necessary authority to perform this action on the local system. Domain and Enterprise Administrators can also install tools on the system if the server is a member of a domain. After Network Monitor is installed, you can gather information that can be used to identify baseline network loads of the client system and troubleshoot problems from the network adapter of the local system.
Network Monitor can be set up with specific triggers so that it automatically starts capturing information when certain conditions are met. Captures can also be set up to use filters to "record" only specific network information in the capture. System Monitor, which can be found in the Performance MMC, is much like Network Monitor, in that it allows you to baseline and review the performance and response of the local system or other systems on a network, depending on how it's configured. The main difference is that Network Monitor enables you to review the network performance, and System Monitor (in the Performance MMC) enables you to review the overall system performance beyond just the networking component. The data that can be collected via System Monitor is categorized into performance objects, performance counters, and performance object instances. Performance objects are the counters associated with a resource or service that can be monitored , such as output from the system processor or the browser service. Performance counters are directly associated with a performance object. The corresponding values associated with the PhysicalDisk counter are values such as Average Disk Bytes/Read, Average Disk Bytes/Write, and so forth, and are not found under the Processor Object because they aren't relevant. The output data from performance counters for particular performance objects can be collected and viewed in real time, or it can be written to a performance log file or an SQL database for analysis. The information can also be stored in HTML format and viewed using Internet Explorer. |
EAN: 2147483647
Pages: 123