| Question 1 | Some of the users in your organization have home offices, where they work during the weekdays. They require access to network resources, and all users can dial directly into the RAS server. Users currently have access 24 hours a day, 7 days a week. For security purposes, you want to limit the dial-in hours from 8 a.m. to 6 p.m. How should you proceed? -
A. Configure the properties of each user account. -
B. Configure the properties of the RAS server. -
C. Configure the conditions of the remote access policy. -
D. Configure the port properties. |
| Question 2 | John is the administrator of a Windows Server 2003 network. One of the users is reporting problems when attempting to dial into a remote access server. John suspects a conflict with the remote access policies. He cannot recall the order in which elements are applied. Which of the following correctly identifies the order in which remote access policy elements are evaluated? -
A. Permissions, conditions, profile -
B. Conditions, permissions, profile -
C. Conditions, properties, permissions -
D. Profile, permissions, conditions |
| Question 3 | You configured Windows Server 2003 as a remote access server. While enabling the service, you chose to use DHCP for IP address assignment. You are still using WINS on the internal network because you are still in the process of upgrading. Clients report that they can successfully connect but cannot access network resources using the UNC path . What must you do to resolve the problem? -
A. You must configure a range of IP addresses on the RAS server, as well as assign any optional IP parameters to clients. -
B. You must manually configure the IP settings on the remote access clients. -
C. You must install the DHCP Relay Agent on the DHCP server. -
D. You must install the DHCP Relay Agent on the RAS server. |
| Question 4 | John made changes to a group policy object and he wants to manually refresh all settings regardless of whether they have been changed. What command should he use? -
A. secedit /refresh -
B. gpupdate /force -
C. gpupdate /target:computer -
D. gpupdate /refreshpolicy -
E. secedit /refreshpolicy |
| Question 5 | You have multiple RAS servers on your network. You want to centralize the authentication of remote access clients and accounting information. Which of the following services should you install? -
A. IAS -
B. IIS -
C. RADIUS -
D. RRAS |
| Question 6 | For security purposes, smart cards are being implemented for all remote access users. Which of the following protocols is required to support smart card authentication? -
A. PAP -
B. EAP -
C. MS-CHAP -
D. SPAP |
| Question 7 | David is the network administrator of a Windows Server 2003 network. He is configuring demand-dial routing between a server in the head office and a server within a branch office. Both servers are running Windows Server 2003. David is configuring the user account on the answering router. Which of the following statements is true? -
A. Any user account name can be used. -
B. The user account name should match the demand-dial interface name of the answering router. -
C. The user account name should match the demand-dial interface name of the calling router. -
D. The user account name must match the computer name of the answering router. |
| Question 8 | Your internetwork consists of seven subnets. All subnets are connected using Windows Server 2003 RRAS servers. Nonpersistent demand-dial connections have been configured. You do not want to be burdened with updating the routing tables, and you want any changes to the network topology to be propagated immediately. Which of the following routing options should you implement? -
A. Static routes -
B. ICMP -
C. OSPF -
D. RIPv2 |
| Question 9 | Mary is the administrator of a Windows Server 2003 network. She added a new subnet to the existing network infrastructure. She needs to add a static route to the routing table to reach the new subnet. The subnet ID in use is 192.168.126.0. Which of the following commands would add a static route to the routing table? -
A. route -p 192.168.126.0 mask 255.255.255.0 192.168.125.1 metric 2 -
B. route add 192.168.126.0 mask 255.255.255.0 192.168.125.1 metric 2 -
C. route add 192.168.126.0 255.255.255.0 192.168.125.1 metric 2 -
D. route add 192.168.126.0 mask 255.255.255.0 gateway 192.168.125.1 metric 2 |
| Question 10 | Brandon is configuring IP security for his network. He wants all data to be encrypted but still wants clients that do not support IPSec to be capable of authenticating with the server. What should he do? -
A. Within the IP Security Monitor snap-in, assign the Secure Server (Require Security) policy. -
B. Configure the settings of the appropriate group policy object and assign the Client (Respond Only) policy. -
C. Configure the Properties of TCP/IP and assign the Secure Server (Require Security) policy. -
D. Edit the appropriate group policy object and assign the Server (Request Security) policy. |
| Question 11 | You are configuring IPSec between two servers in a workgroup. You assign Client (Respond Only) to each of the servers, but you notice that IP packets being sent between the two servers are not being secured. What is causing the problem? -
A. Both are configured with the Client (Respond Only) policy. -
B. You can use IPSec only with Active Directory. -
C. One of the servers must be configured as an IPSec client. -
D. The servers cannot be members of the same workgroup. |
| Question 12 | You updated the policy settings and you want to apply changes immediately. Which of the following commands can you use? -
A. secedit -
B. gpupdate -
C. dcgpofix -
D. gpresult |
| Question 13 | Mike is planning a VPN solution for his company network. Which of the following protocols can you use to establish a VPN tunnel with a Windows Server 2003 VPN server? (Choose all correct answers.) -
A. PPP -
B. PPTP -
C. SLIP -
D. L2TP |
| Question 14 | John has enabled Routing and Remote Access on a computer running Windows Server 2003. Several clients establish VPN connections with the server from home offices. There are 20 clients that will be accessing the VPN server. John needs to increase the number of available PPTP ports. How can he accomplish this task? -
A. From the Properties window for the server, select the Ports tab. -
B. Using the Edit Profile button within the properties window for the policy, select the Ports tab. -
C. Use the Properties window for the Ports option. -
D. Use the PPTP tab from the Ports Properties window. |
| Question 15 | RRAS is installed on Server1. All remote access clients are running Windows XP Professional. You want to configure the most secure authentication protocol. Which of the following should you enable? -
A. PAP -
B. CHAP -
C. MS-CHAP version 1 -
D. MS-CHAP version 2 |
| Question 16 | Your network consists of three subnets: Subnet A, Subnet B, and Subnet C. There is a RRAS server on Subnet C configured with a range of IP addresses to assign to remote access clients. There are two DNS servers on the network, DNS01 and DNS02. You want remote access clients to use DNS02. What should you do? -
A. Configure the RRAS server to use DHCP. Install a DHCP server on Subnet C. Configure a scope on the DHCP server for the remote access clients. Configure the DHCP relay agent on the DNS server. -
B. Install a DHCP server on the network and configure the RRAS server to use DHCP for IP address assignment. Configure a scope on the DHCP server for the remote access clients. -
C. Install a DHCP server on the network. Configure a scope on the DHCP server for remote access clients. Configure RRAS to use DHCP. Configure the relay agent on the DHCP server. -
D. Install a DHCP server on Subnet C. Configure a scope on the DHCP server for remote access clients. Configure RRAS to use DHCP. Configure the relay agent on the RRAS server. |
| Question 17 | Joe is the administrator of a Windows Server 2003 network. He has configured a remote access server. Because of the security requirements of the company, he creates multiple remote access policies. User A attempts to gain remote access. The connection attempt does not meet the conditions of the first remote access policy. Which of the following statements is true? -
A. The connection attempt is denied . -
B. The properties of the user's account are evaluated. -
C. The next policy in the list is evaluated. -
D. The profile settings are evaluated. |
| Question 18 | Dayton Distributing plans to use Routing and Remote Access to give users the ability to access resources from other locations while still maintaining a high level of security. Specifically, the company president needs to be able to access resources from his home office and other locations. Network administrators also require remote access when they are working from home. You add a Windows Server 2003 server to the network and configure it as a remote access server. When configuring the dial-in properties of user accounts, how should you configure them for callback? -
A. Choose No Callback for the president's account and Set by Caller for the network administrators' accounts. -
B. Choose Set by Caller for the president's account and No Callback for the network administrators' accounts. -
C. Choose Always Callback To for the president's account and Set by Caller for the network administrators' accounts. -
D. Choose Set by Caller for the president's account and Always Callback To for the network administrators' accounts. |
| Question 19 | Your junior network administrator was responsible for installing and configuring a remote access server. Certain users need to be able to dial directly into the server to access network resources. To test the configuration, you attempt to connect to the server but are unsuccessful . When you open the Routing and Remote Access snap-in, you notice that the default remote access policy has been deleted. What should you do? -
A. Disable Routing and Remote Access and then re-enable the service. -
B. Create a remote access policy. -
C. Configure the dial-in properties of the user accounts. -
D. Configure the remote access profile settings. |
| Question 20 | Jim has configured two remote access policies. The profile settings of Policy A are configured so that remote access is permitted only during the hours of 8 a.m. and 5 p.m. This policy is applied to the Sales group. Policy B has no dial-in restrictions configured, and it is applied to the Managers group. Policy A is listed first. Mike is a member of the Sales and Managers groups. He attempts to dial into the remote access server at 6 p.m. Which of the following statements is true? -
A. Mike will be permitted remote access. -
B. Because the connection attempt does not match the profile settings of Policy A, Policy B is evaluated. -
C. The connection attempt is denied. -
D. The dial-in restrictions configured for Mike's user account determine whether he has remote access permission. |
| Question 21 | You are in the process of configuring profile settings for a remote access policy. You configure the settings as shown in the following figure. Which of the following statements are true? (Choose all correct answers.) 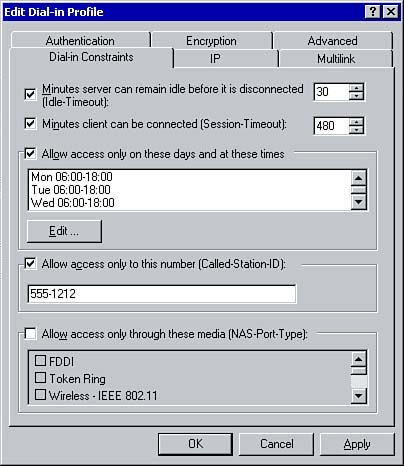 -
A. Users will be disconnected after 8 hours of inactivity. -
B. Users will be disconnected after 30 minutes of inactivity. -
C. Users can remain connected as long as necessary. -
D. Users can dial in only between 6 p.m. and 6 a.m. -
E. Users can dial in only between 6 a.m. and 6 p.m. -
F. Users can dial any number for remote access. |
| Question 22 | Mark is the administrator of a Windows Server 2003 network. A user reports that he is unable to communicate with any hosts on a remote subnet. Mark uses the ipconfig command to verify that TCP/IP is properly configured on the workstation. He uses the ping command to test whether TCP/IP is initialized on the local computer. He then pings the IP address assigned to the local workstation. Both pings have successful results. When troubleshooting the problem, what should he do next? -
A. Ping the IP address of a local host. -
B. Ping the IP address of the default gateway. -
C. Ping the IP address of a remote host. -
D. Ping the IP address of a remote router. |
| Question 23 | John captured a large amount of network traffic using Network Monitor. He wants to limit the captured information to only display traffic containing the SMB protocol. What should he do? -
A. Configure a trigger. -
B. Configure a capture filter. -
C. Configure a display filter. -
D. Configure a packet filter. |
| Question 24 | Mary is the network administrator. She wants to give Joe the ability to view real-time data as it is captured using System Monitor. Joe should be able to perform this task from the server or from his workstation. What should Mary do? -
A. Add his user account to the Performance Log Users group. -
B. Add his user account to the Administrators group. -
C. Add his user account to the Performance Monitor Users group. -
D. Add his user account to the Domain Admins group. |
| Question 25 | Bob is running Network Monitor to analyze specific types of network traffic. He wants to configure Network Monitor to only gather information pertaining to specific protocols and traffic type. What should he do? -
A. Configure a display filter. -
B. Configure a capture filter. -
C. Configure a trigger. -
D. Configure an IP packet filter. |
| Question 26 | Susan is putting together a performance report for her managers. She wants to gather statistics about the total amount of TCP/IP traffic on the local computer. Which of the following counters should she monitor? |
| Question 27 | You are having trouble connecting to your ISP using a dial-up connection. You want to verify the TCP/IP configuration on the local computer. Which utility should you use? -
A. ipconfig -
B. ping -
C. tracert -
D. pathping |
| Question 28 | A computer running Windows Server 2003 connects to the Internet through a dial-up connection. You are having problems establishing a connection and you want to verify that the modem is working. Which of the following can you use to verify the status of the modem? -
A. System Monitor -
B. Network Monitor -
C. ping -
D. Device Manager |
| Question 29 | Mary is gathering network-performance statistics on a Windows Server 2003 domain controller. She wants to determine the number of logons the domain controller has received since the last time it was restarted. Which counter should she monitor? -
A. Logons Received Total -
B. Logon Total -
C. Logons Received/sec -
D. Logons/sec |
| Question 30 | Clients on the network are unable to obtain an IP address from the DHCP server on the network. You soon discover that the DHCP service on the server has failed to start. You reboot the server and the service still does not start. What should you do? -
A. Continue to reboot the server until the service starts. -
B. Verify that any services DHCP depends on are started using the Services console. -
C. Use the DHCP console to start the service. -
D. Reinstall the DHCP service. |
| Question 31 | Bill is configuring the service-recovery options for the server service on a Windows Server 2003 domain controller. If a service fails to start, which of the following actions can he perform? (Choose all correct answers.) -
A. The computer can attempt to restart the service. -
B. He can reboot the computer. -
C. He can restart the services that it depends on. -
D. He can send an email message to the network administrator. |
| Question 32 | A new network service is added to the existing infrastructure. You want to determine how much more traffic is generated since it was installed. Which of the following tools can you use to capture and analyze network traffic? -
A. Network Performance -
B. Network Diagnostics -
C. Network Monitor -
D. Network Manager |
| Question 33 | Which of the following command-line utilities can you use to view a list of all the routers a packet passes through to reach a specific destination host? -
A. ping -
B. tracert -
C. arp -
D. ipconfig |
| Question 34 | A new service pack has just been released for Windows Server 2003. You download the service pack. What should you do before installing it? -
A. Notify users that the server will be down. -
B. Take all production servers offline. -
C. Install the service pack in a test environment. -
D. You need do nothing but proceed with the installation. |
| Question 35 | Diane finished installing Windows Server 2003. She is in the process of performing some basic steps to secure the operating system. She wants to implement the principle of least privilege. What should she do? -
A. Create a new user account for herself and add it to the local Administrators group so that she can perform administrative tasks at any time. -
B. Nothing. She should always log on with the Administrators account. -
C. Create a new group and add the group to the local Administrators group. Create a user account for herself and add it to the new group. -
D. Create two user accounts: one with restrictive permissions for performing daily tasks and the other with additional privileges for performing administrative tasks. |
| Question 36 | Sean finished running the Security Configuration and Analysis utility on a domain controller. He notices that several of the results appear with a red X beside them. What does this red X indicate ? -
A. It indicates that the system settings correspond with those in the template. -
B. It indicates that the configured system settings do not match those in the template. -
C. It indicates that these values do not need to be configured based on the server role. -
D. It indicates that these settings have not been configured. |
| Question 37 | Joe has just made changes to the security settings on a domain controller. He is concerned that the changes will not be automatically updated. What is the default interval at which security settings are automatically refreshed on a domain controller? -
A. 24 hours -
B. 60 minutes -
C. 5 minutes -
D. 60 seconds |
| Question 38 | Mary is testing the impact of various security settings within a test environment. She makes several changes to the security settings on a standalone server. What is the default interval at which security settings are automatically refreshed on a workstation or server? -
A. 24 hours -
B. 12 hours -
C. 120 minutes -
D. 90 minutes |
| Question 39 | Auditing is enabled for the Bayside network. Tony is the senior network administrator and suspects that one of the junior network administrators has made changes to some of the settings with the group policy object. Which log file should Tony use to verify his suspicions? -
A. Application -
B. Audit -
C. Security -
D. System |
| Question 40 | Mary is planning to install SUS. Which of the following are considered to be minimum hardware requirements for installing SUS? (Choose all correct answers.) -
A. Pentium III 500MHz -
B. Pentium III 700MHz -
C. 265MB RAM -
D. 512MB RAM -
E. 4GB storage space -
F. 6GB storage space |
| Question 41 | Which of the following correctly identifies the order of steps in which the IP address lease process occurs? -
A. DHCPAck, DHCPRequest, DHCPDiscover, DHCPOffer -
B. DHCPRequest, DHCPAck, DHCPDiscover, DHCPOffer -
C. DHCPDiscover, DHCPOffer, DHCPAck, DHCPRequest -
D. DHCPDiscover, DHCPOffer, DHCPRequest, DHCPAck |
| Question 42 | Ryan finished configuring a new DHCP server. He installed the service and configured and activated a scope. Ryan now needs to authorize the DHCP server. Which administrative tool can he use to perform this task? |
| Question 43 | Mike is adding a new DHCP server to the network. Of the following, which steps must he complete for the DHCP server to function on the network? (Choose all correct answers.) -
A. Install DHCP. -
B. Activate a scope. -
C. Configure a scope. -
D. Authorize the DHCP server. -
E. Configure the scope options. -
F. Install Active Directory on the local server. -
G. Enable dynamic updates. |
| Question 44 | Your DHCP server must support multicasting. When configuring a multicast scope, which IP address range can you use? -
A. 192.160.0.1 “192.168.0.255 -
B. 127.0.0.1 “127.0.0.255 -
C. 169.254.0.1 “169.254.255.254 -
D. 224.0.0.1 “239.255.255.255 |
| Question 45 | Your network consists of two subnets: Subnet A and Subnet B. Each has its own DHCP server. You configure the scope on DHCP1 for Subnet A. Users are all leasing an IP address but report that they cannot access any resources outside of their own subnet. How can you most easily solve the problem? -
A. Activate the scope on DHCP1. -
B. Configure the default gateway on each workstation. -
C. Configure the 003 router option on DHCP1. -
D. Configure the 006 DNS server option on DHCP1. |
| Question 46 | Which of the following components is responsible for negotiating security between IPSec-enabled hosts? |
| Question 47 | You use a DHCP server to assign IP addresses to clients and member servers on the network. Three of the member servers host print devices. How can you ensure that these print servers lease the same IP address from the DHCP server? (Choose all correct answers.) -
A. Exclude the IP addresses from the scope. -
B. Create a separate scope for each of the print servers. -
C. Create a client reservation for each print server. -
D. Configure the DHCP options for the scope. |
| Question 48 | Because of security needs and the different needs of dial-in clients, you configure three remote access policies. When a remote access client attempts to connect to a remote access server, which of the following statements is true regarding policy evaluation? -
A. All policies in the list are evaluated. -
B. The first policy to match the conditions of the connection attempt is evaluated. -
C. Only the first policy in the list is evaluated. -
D. The first policy that gives the user remote access is evaluated. |
| Question 49 | Your primary DNS server is located in the corporate head office. The five branch offices are all configured with secondary DNS servers. The WAN links between offices are extremely slow. You want to increase the interval at which secondary servers poll the primary server for updates to the zone file. Which of the following settings should you change? -
A. Retry interval -
B. Serial number -
C. Refresh interval -
D. Time to Live |
| Question 50 | You recently deployed a DHCP server to centralize the administration of all IP addresses on the network. Prior to this step, all IP addresses were statically configured. All users are successfully leasing IP addresses but sometimes report that they cannot print to the network interface printers. The printers are not configured as DHCP clients and are still configured with static IP addresses. Upon examining the event log, you notice there are IP address conflicts. What should you do? -
A. Define separate scopes for each of the print devices. -
B. Create client reservations for the print devices. -
C. Exclude the IP addresses of the print devices from the scope. -
D. Create client exclusions for the print devices. |
| Question 51 | FKB Consulting hosts a primary DNS server in the corporate head office. The five branch offices are all configured with secondary DNS servers. Each branch office is now being configured with a second DNS server. You do not want any more traffic generated on the WAN links or the LAN from zone transfers. How should you configure the new DNS servers? -
A. Configure the new servers as secondary DNS servers with the existing secondary DNS servers as master name servers. -
B. Configure the new DNS servers as caching-only servers. -
C. Configure the new DNS servers as secondary DNS servers with the primary DNS server as the master name server. -
D. Configure the new DNS servers as primary DNS servers. |
| Question 52 | John is configuring a remote access server. All workstations requiring remote access are running Windows XP Professional. John wants all remote access users to authenticate using MS-CHAP version 2. What should he do? -
A. Enable MS-CHAP version 2 through the Properties of the remote access server. -
B. Edit the conditions of the remote access policy and enable MS-CHAP version 2. -
C. Configure the profile of the remote access policy and enable MS-CHAP version 2. -
D. Enable MS-CHAP version 2 through the Properties of each user account. |
| Question 53 | Your network consists of two subnets: Subnet A and Subnet B. Subnet A has a WINS server that is used by all clients on the network to resolve NetBIOS names to IP addresses. A Windows Server 2003 DHCP server assigns IP addresses to clients. The DHCP 044 WINS/NBNS Servers option is configured at the scope level to assign clients the IP address of WINSRV A. You move the WINS server from Subnet A to Subnet B and configure the 044 WINS/NBNS option at the server level to assign clients the new IP address of the WINS server. You discover that clients are still being assigned the old IP address. What is causing the problem? -
A. Clients must use the ipconfig /renew command to obtain the new WINS IP address. -
B. The IP address of the WINS server must be statically configured on client workstations. -
C. You must configure the 046 WINS/NBT node type. -
D. The new 044 WINS/NBNS option must be configured at the scope level. |
| Question 54 | You are asked to ensure that the IPSec policy put into place secures all communications while still allowing non-IPSec “aware clients to authenticate. Which of the following policies should you use? -
A. Client (Respond Only) -
B. Server (Request Security) -
C. Secure Server (Require Security) -
D. Secure Client (Respond Only) |
| Question 55 | Users on the network require remote access. All users should have the same remote access security requirements except the Administrators group. How should you configure RRAS? -
A. Create two groups within RRAS, one for users and one for administrators. Create two remote access policies and use the Windows Groups condition to apply each policy to the appropriate set of users. -
B. Create two groups within Active Directory User and Computers, one for users and one for administrators. Create two remote access policies and use the Windows Groups condition to apply each policy to the appropriate set of users. -
C. Create two groups within RRAS. Configure different settings within a single policy for each group. -
D. Create two access policies. Using the Dial-In tab for each user account, specify which remote access policy should be applied. |
| Question 56 | Which of the following commands allows you to clear the DNS resolver cache on a Windows XP Professional workstation? -
A. ipconfig /clearcache -
B. ipconfig /all -
C. ipconfig /flushdns -
D. ipconfig /cleardns |
| Question 57 | You are implementing an IP security policy for your network. SRV1 requires the highest level of security because it hosts sensitive company data. SRV2 does not require this level of security but should respond to any requests for secure communication. How should you proceed? (Choose two.) -
A. Assign the Server (Request Security) policy on SRV1. -
B. Assign the Secure Server (Require Security) policy on SRV1. -
C. Assign the Client (Respond Only) policy on SRV2. -
D. Assign the Server (Request Security) policy on SRV2. -
E. Assign the Secure Server (Require Security) policy on SRV2. -
F. Assign the Client (Respond Only) policy on SRV1. |
| Question 58 | Your internetwork consists of 10 subnets. All subnets are connected using Windows Server 2003 RRAS servers. You configured nonpersistent demand-dial connections. You do not want to manually update routing tables. You want to configure password authentication between routers. Which of the following should you implement? -
A. Static routes -
B. ICMP -
C. OSPF -
D. RIPv2 |
| Question 59 | Which of the following statements is true regarding two-way demand-dial connections? -
A. The user account name on the answering router must match the demand-dial interface name on the calling router. -
B. The demand-dial interface names must be identical. -
C. The user account names on both routers must be identical. -
D. The user account name on the answering router must be different from the interface name on the calling router. |
| Question 60 | Which of the following parameters can you use with the route command to ensure that a static route is not deleted from the routing table upon restart? |