SSLTLS Improvements
SSL/TLS Improvements
There are two major improvements to SSL/TLS in Windows Vista. The first is newer cipher suites, including support for the Suite B algorithms: ellipticcurve encryption, SHA-2, and AES. Windows Vista supports the cipher suites shown in Table 7-3.
| TLS_RSA_WITH_AES_128_CBC_SHA | TLS_DHE_DSS_WITH_AES_128_CBC_SHA |
| TLS_RSA_WITH_AES_256_CBC_SHA | TLS_DHE_DSS_WITH_AES_256_CBC_SHA |
| TLS_RSA_WITH_RC4_128_SHA | TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA |
| TLS_RSA_WITH_3DES_EDE_CBC_SHA | TLS_RSA_WITH_RC4_128_MD5 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256 | SSL_CK_RC4_128_WITH_MD5 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384 | SSL_CK_DES_192_EDE3_CBC_WITH_MD5 |
| TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P521 | TLS_RSA_WITH_NULL_MD5 |
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256 | TLS_RSA_WITH_NULL_SHA |
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384 | TLS_RSA_WITH_DES_CBC_SHA |
| TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P521 | TLS_DHE_DSS_WITH_DES_CBC_SHA |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256 | TLS_RSA_EXPORT1024_WITH_RC4_56_SHA |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384 | TLS_RSA_EXPORT1024_WITH_DES_CBC_SHA |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P521 | TLS_DHE_DSS_EXPORT1024_WITH_DES_CBC_SHA |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256 | TLS_RSA_EXPORT_WITH_RC4_40_MD5 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384 | SSL_CK_DES_64_CBC_WITH_MD5 |
| T LS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P521 | SSL_CK_RC4_128_EXPORT40_WITH_MD |
SSL/TLS in Windows Vista also supports the following cipher suites, but they can only be used from code by calling the SSL/TLS Security Support Provider (such as TLS1SP_NAME) directly.
-
TLS_RSA_WITH_NULL_MD5
-
TLS_RSA_WITH_NULL_SHA
As mentioned earlier in this chapter, you can also add a custom cipher suite by a writing an SSL/TLS provider plug-in.
Second, Windows Vista makes it easier to configure the cipher suites you are willing to support for SSL/TLS; it’s simply a policy setting. You can set the policy by performing the following steps:
-
Open mmc.exe.
-
Click File and then Add/Remove Snap-in.
-
Scroll down to and select the Group Policy Object Editor.
-
Click Add.
-
Select remote computer by clicking Browse, or Finish, to access the local computer.
-
Click OK and then OK again.
-
Open the following nodes: Local Computer Policy, Computer Configuration, Administrative Templates, and then Network.
-
Click the SSL Configuration Settings node.
-
Double-click the SSL Cipher Suite Order setting.
-
Click Explain to learn how to modify this setting.
SSL/TLS Revocation Checking and OCSP
Certificate Revocation List (CRL) checks are available in all currently supported versions of Windows. When an application wants to verify a certificate is not revoked, the application reads the Certificate Revocation List Distribution Point (CDP) from the certificate. A CRL lookup could use HTTP, LDAP, or simple remote file access to fetch the CRL. The CRL is a digitally signed blob that includes revoked certificate serial numbers. If the serial number of the certificate being validated is in the CRL, then the certificate is revoked, and the application should take appropriate action.
Windows Vista also supports Online Certificate Status Protocol (OCSP), as defined in RFC 2560 (RFC 2560). OCSP has advantages and disadvantages over using CRLs because they can get large, but an OCSP lookup is small. The major disadvantage is that for OCSP to work, the application must be online, but CRLs can be cached, which means a CRL lookup may not necessarily be remote.
| Note | Windows “Longhorn” Server includes OCSP server support. |
The really good news is OCSP support is transparent in Windows Vista if the certificate being checked includes an appropriate Authority Information Access (AIA) URL. Like a CDP, an AIA can include a URL or URLs to access to determine if the certificate has been revoked or not. Figure 7-2 shows a valid AIA in a Web server certificate.
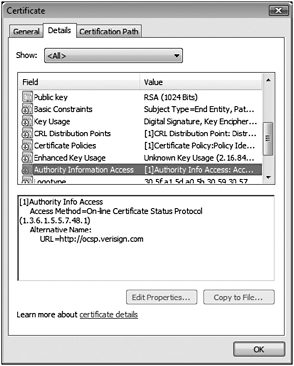
Figure 7-2: A Verisign certificate that includes an AIA for OCSP use.
If your application calls CertGetCertificateChain to verify a certificate, and the certificate includes an appropriate AIA, then Windows Vista will use OCSP to verify the certificate before checking the CRL if a CDP is present in the certificate. You can change this policy by performing the following steps:
-
Open mmc.exe
-
Add the Group Policy Object Editor Snap-in.
-
Expand the Local Computer Policy node.
-
Expand the Computer Configuration node.
-
Expand the Windows Settings node.
-
Expand the Security Settings node.
-
Click the Public Key Policies node.
-
Double-click the Certificate Path Validation Settings Properties object type.
-
Click the Revocation tab.
Figure 7-3 shows the revocation policy dialog box.
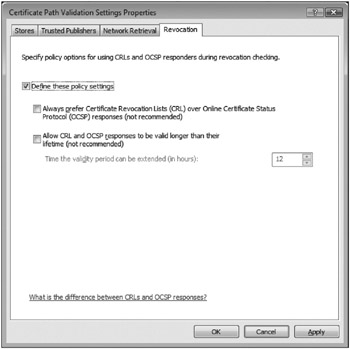
Figure 7-3: Certificate revocation policy settings in Windows Vista.
An application may fail to access a CDP or the OCSP URL, in which case functions like Cert-GetCertificateChain will fail and return a CRYPT_E_REVOCATION_OFFLINE error. If your application is in a bind, what should it do if it cannot verify that a certificate is revoked or not? We can’t give a 100 percent applicable answer because it depends on the nature of your application. If it is a sensitive application, or an application running in a sensitive environment, then you should fail operations related to the certificate use.
The certutil -url command-line tool can be used to interactively verify a certificate using a CRL or OCSP.
| Note | You can look at important certificate-related events in the Event Viewer. Open the Event Viewer, and expand Applications and Services Logs, then expand Microsoft, then expand Windows and finally expand CAPI2. |
EAN: 2147483647
Pages: 122