3.2. Installing FreeBSD
| < Day Day Up > |
| The FreeBSD install process brings you to the sysinstall(8) main screen (see Figure 3-2). If necessary, change your keymap or adjust install options. If you are booting from an older FreeBSD CD yet performing an FTP install, you may need to point the install elsewhere by changing Release Name under Options. That done, choosing the standard install is probably your best bet. Figure 3-2. The sysinstall main screen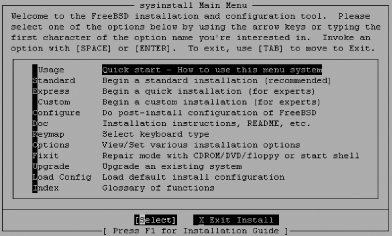 3.2.1. Preparing the DiskYour first step will be to put into effect decisions you have already made regarding filesystem slicing. Having these written down in advance helps ensure you haven't made any mistakes. Select your drive, decide whether or not to dedicate the entire disk or to leave aside some space for a maintenance partition, and move on. If you are not dual-booting, a standard boot loader is all you need. Finally, choose a filesystem layout that is appropriate for your system's task, as shown in Figure 3-3. Figure 3-3. The disklabel(8) editor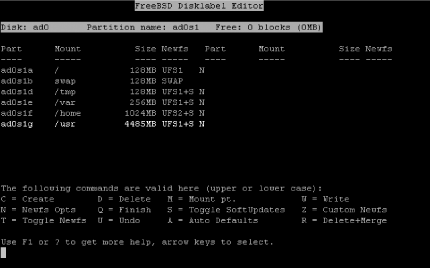 FreeBSD 5.0 added support for UFS2 filesystems and, in fact, this is the default. These filesystems provide improved performance during fsck(8), support for larger filesystems, and extended attributes for native discretionary (ACLs) and mandatory access control (TrustedBSD MAC Framework). There are no particularly compelling reasons to fall back to the UFS1 filesystem. 3.2.2. Choosing Distribution SetsThis is the meat of the FreeBSD install process. It is here that you get to pick and choose the key parts of the base operating system you will need. Figure 3-4 shows the "canned" distribution sets that FreeBSD provides. While the Minimal option seems like a good bet, it is possible to install more without sacrificing security.
The Minimal distribution set includes both the base FreeBSD operating system and basic encryption services (ssh and SSL-related binaries and libraries, pam, kerberos, etc.). If you select Minimal, you can further customize which distributions are installed by subsequently selecting the Custom option. Figure 3-4. Choosing a distribution set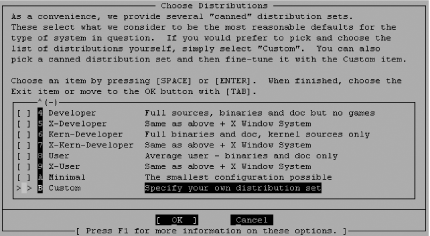 Making a system more secure will likely simultaneously make it less convenient to manage, but the converse is not true: making system administration an arduous task does not imply that your system is more secure. Install the man, catman, and info distributions. If your environment requires kerberos, then by all means install the [eBones] krb4 or [Heimdal] krb5 distributions. Alternately, the MIT version may be installed from ports (ports/security/krb5) after the install. If you plan to rebuild your kernel or perform a local upgrade (as opposed to over NFS), install the src distribution. Installing ports(7) is a matter of preference. Some prefer to install binary packages instead of compiling ports locally. Others write scripts to pull down only the ports in which they are interested. It is your call. In either case, if you plan to cvsup to the latest versions of either the entire src or ports distributions, it makes sense to install them now and pull down only differences. The examples we provide in this book will always favor ports over packages. Take note that in FreeBSD 5.x perl is a separate distribution. If you'll have need of a Perl interpreter (and you probably will, especially if you're going to be installing software from ports), install the perl distribution. As was mentioned previously, you will rarely find X installed on servers. For an infrastructure server, command-line tools are usually adequate for administration. If you are building a multiuser development system or workstation, pieces of the X distribution may be required and may be installed later. Choose your desired distributions, click OK, and FreeBSD will begin installing. 3.2.3. Post-Installation ConfigurationThe following section describes the various choices during the FreeBSD install process. Any prompt that may affect the security of your system is described below. The post-installation configuration begins by prompting you to enable your network interface. 3.2.3.1 Basic network configurationUsing DHCP during the install process can be dangerous, as discussed earlier in this chapter. When building servers, it is often easier to start with statically configured network information than worry about the implications of DHCP. You will be prompted to bring up the interface you just configured before continuing with the install process. It is safe to do so, if you trust your network or are not connected. 3.2.3.2 Network gatewayUpon completion of your network interface configuration, you are prompted: "Do you want this machine to function as a network gateway?" The answer to this prompt will depend on the role of your system. If your system will be a routing firewall, provide network address translation (NAT) services, or will for some other reason route packets, you will want to answer yes. Otherwise, say no. 3.2.3.3 inetdIf you are not providing one of the services inetd spawns, skip configuration of this super server during the install process. Even if you will be providing a service that runs from inetd (e.g., ftpd(8)), it's easy enough to configure it later, after you have hardened your system. Say No here for now. 3.2.3.4 sshdIt is very convenient to enable sshd at this stage. It means you will not need to sit with a console attached to the system while you configure it. If you have been paying attention to the security mailing lists and are confident that sshd listening on your newly installed server is safe (it has no known vulnerabilities), leave it on. 3.2.3.5 Security profile (FreeBSD 4.x only)FreeBSD 4.x installs provide a set of prepackaged security profiles available only during installation. These profiles consist of a variety of changes to system defaults (specifically, in /etc/rc.conf) that are outlined in Table 3-1. These profiles are termed Moderate and Extreme, though the term Medium is used interchangeably with Moderate.
Following the defense in depth principle, a security-minded system administrator would opt for the most secure configuration, enabling only services that are required instead of disabling services that are not: she would choose the Extreme security profile. If you choose a Moderate security profile, you will gain the ability to upgrade your system after the install while still in multiuser mode. If you choose the Extreme security profile, you will have to drop to single user mode to perform the upgrade; this is the recommended approach anyway.
When your system has been installed, you can switch to the holographic shell provided for you on vty4 (press Alt-F4), and disable all unnecessary services by modifying your startup configuration file, /etc/rc.conf. After the installation is complete and your system is up and running, you can turn any necessary services back on after you are sure there are no known vulnerabilities in these services. 3.2.3.6 Anonymous FTPThe same rules apply to Anonymous FTP as to inetd. Even if you plan to be providing unauthenticated FTP access, deployment of this service should be performed carefully and after the system has been prepared. Before configuring this service, you should set up a jail(8) as described in Chapter 2. 3.2.3.7 NFSNFS is a primitive protocol that provides file-sharing capability. Unfortunately it also provides little in the way of authentication and no encryption by itself. Deployment of NFS in a perimeter network or beyond the firewall should be avoided. Deployment anywhere else should probably also be avoided. See Chapter 4 for a more extensive discussion of the pitfalls of NFS and some possible alternative approaches. 3.2.3.8 Time zoneConsistent time is vital in a networked environment. For piecing together an audit trail, debugging mail or web application logs, or authenticating using Kerberos tickets, you should care about the system time. Resist the temptation to put your system's clock in Africa (unless, of course, your server resides in Africa).
3.2.3.9 Linux compatibilityYou may need Linux compatibility for building workstations and servers that must run proprietary commercial binaries available only for Linux (such as for audio and video streaming) and other non-BSD operating systems. If you do not foresee the need, follow a minimalist approach and skip Linux compatibility for now you can always add it later. 3.2.3.10 XFree86A graphical user interface is appropriate on workstations and development servers. Workstations will require a full complement of X-related binaries, libraries, and user interface applications; development servers often only need enough libraries to be able to run self-built GUI programs and compiling tools. Infrastructure servers do not generally run X but sometimes have X libraries installed. For example, an installation of Apache for a production web server at an ISP may also require a variety of graphics suites that rely on the existence of X libraries. In this case, the X libraries in question may be installed through dependencies in the ports installation process. 3.2.3.11 PackagesThe packages available during the install process are generally of similar age as the release. If you're installing an older version of FreeBSD (knowing full well that you will be upgrading in a moment), the packages you install in this step will be equally antiquated. However there is one package you should install now: sudo. We mentioned sudo briefly earlier in this chapter and will cover the tool in far greater detail in Chapter 4. For now, either bear with us here as we ask you to blindly install this package or become familiar with sudo by reading the relevant sections in Chapter 4 and return here. Either way, scroll down to the security category, find sudo, select it, and install it. 3.2.3.12 Finishing up the installFinally you're given the option to create a user account and set a root password. As discussed previously, it's important to create a user account instead of running around as root, and the passwords you set both for yourself and the root user should be strong. Many administrators like to add themselves to the wheel group at this point. However, you don't need to do this to gain root level access since you're using sudo. After these two steps, you find yourself at the end of the sysinstall process. Congratulations! |
| < Day Day Up > |
EAN: 2147483647
Pages: 142
