The SAFE SMR Blueprint
| Finally, we come to the one that the CSI Exam is officially about"SAFE: Extending the Security Blueprint to Small, Midsize, and Remote User Networks." In fact, we've seen the foundation of the SAFE SMR Blueprint in the Enterprise and the VPN Blueprints. The SMR Blueprint scales things down a bit and pays attention to remote connectivity: Where a large enterprise might need to separate things out for manageability, small and medium organizations don't have that luxury. Therefore, the security needs of these organizations as a whole and their remote connectivity are combined in the SAFE SMR Blueprint. Design FundamentalsThe SAFE SMR design fundamentals will seem familiar, and they bear obvious relationships to the design fundamentals you've seen before:
These are really very similar to the design fundamentals for Enterprise SAFE, discussed in Chapter 6. A major difference is that SAFE SMR is not intended to incorporate the resiliency and scalability of the Enterprise model; the focus instead is on cost-effective deployment (and there is no e-commerce in the SMR model). For small enterprises , cost containment is a major issue; by itself, that limits the degree of resiliency that can be implemented. However, the consequence of that lack of resiliency is to make controlling access to critical network resources even more important. It also increases the importance of securing your reporting and network-management functions, along with tuning your IDS as closely as you can manage (to avoid false negatives , even at the expense of dealing with a few more false positives). In short, the design fundamentals of the SAFE SMR Blueprint are almost those of the Enterprise, without the budget or the resources. This actually reflects the case in many, if not most, real networks. AxiomsThe SAFE SMR axioms will sound awfully familiar by now (on purposeyou'll want to know them):
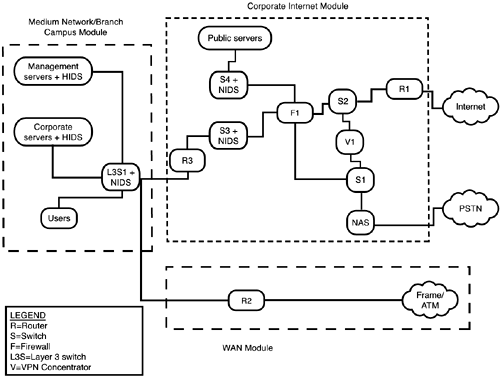
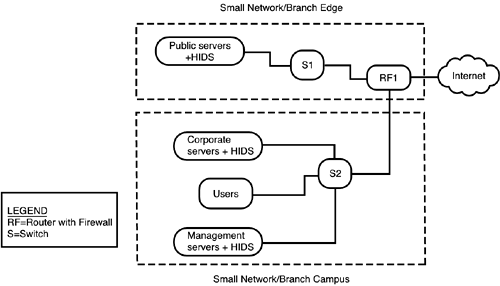
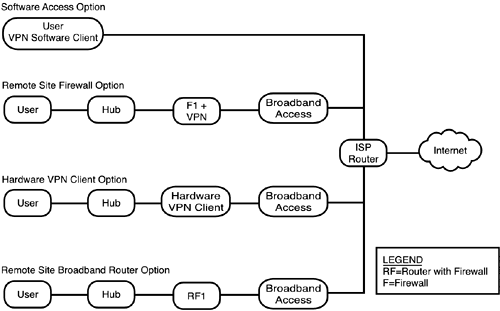
In fact, these are exactly the same axioms as those used for the Enterprise SAFE Blueprint. They were discussed in detail in Chapter 6; if you need to review that, do so now. Headend vs. Branch ConsiderationsWe've thrown around the term headend quite a bit in this chapter, mostly when dealing with VPNs. The concept is simple: When establishing a link between two locations, one location is bigger or more important in the great scheme of things than the other. This is the headend, the entry to the larger network or the greater set of resources. Thus, if you have a large enterprise with a branch campus (which might be designed according to the medium SAFE model), the large enterprise end of the connection between them is the headend, and the branch office is the branch. Likewise, that same branch might have VPNs to remote usersindividuals. For those VPNs, the branch office is the headend and the remote user is the branch. The SAFE SMR network designsthe small network design and the medium network designcan be used for locations that act as either the headend or the branch, depending on their relationship to the network and users at the other end of the connection. So what do these SMR networks look like? They're much less complex than the Enterprise model, partly as a matter of scale and partly because of the absence of the heavy resilience in the Enterprise model. Even the medium model can fit into one diagram, as shown in Figure 7.2. Figure 7.2. The SAFE SMR medium network model. Working from left to right, you can see that the servers are all protected with HIDS, and the switch connecting this module to the Corporate Internet module is also employing NIDS. (Server traffic is inspected twice because HIDS are often tuned more tightly, given the limited applications present on most servers, even multipurpose ones.) The WAN module is quite straightforward because it was on the Enterprise model: a router to perform basic filtering and traffic forwarding to and from the Frame/ATM cloud. The most complex module, though much less complex than its Enterprise cousin, is the Corporate Internet module. The public servers are isolated in a "mini-DMZ" that branches off the firewall. Like the public servers in the Enterprise model, the various servers here are set on private VLANs from a switch with NIDS. The incoming Internet connection passes through a perimeter router and then a switch. If the traffic is an incoming VPN, it is redirected to a VPN concentrator. After the VPN tunneling header is validated and stripped off, the traffic is switched on into the firewall for inspection. Then ( assuming that it passes, of course) it is switched on into the Campus module. If the traffic is incoming public traffic, it goes from the switch to the firewall and then to the public servers. Some VPN incoming traffic might be dialup; that comes in from the PSTN and passes through a NAS, after which it can be switched through to the VPN concentrator or directly to the firewall, as appropriate. The Corporate Internet module in the SMR model is thus a combination of the Corporate Internet module and the VPN module from the Enterprise model, again on a smaller scale. The small network is even easier to see, as in Figure 7.3. Figure 7.3. The SAFE SMR small network model. In this much smaller network, you see Internet traffic filtered by a router with firewall software on ingress, where it can be directed to a mini-DMZ, again protected by private VLANs (if multiple physical devices are used as servers). The Campus module is functionally the same as that of the medium model; the only difference is that the switch is scaled back to a Layer 2 switch without NIDS instead of a Layer 3 switch with NIDS. That leaves us with the remote-user model, which, as we noted earlier, uses the same architecture set as the remote end of the SAFE VPN Blueprint. This set is shown in Figure 7.4. Figure 7.4. The SAFE SMR remote-user model. In this case, we actually have four possible models, depending on how the remote user accesses the Internet. Working down from the top, the simplest model is when the user connects directly to the ISP, typically dialing into the ISP. In this case, the ISP router might be a NAS, but we know that the client's traffic will enter the Internet via a router, so this is still representational. In this simple case, the VPN software client is the "device" that creates the user end of the tunnel. Note that, with no other device intervening between this host and the big, bad Internet, all protective functions must reside locally on the PC. This host should have a software firewall (also called a personal firewall) along with antivirus softwareand both must be kept current. In the remaining cases, the user is connecting via broadband (xDSL or cable modem service). In the second case, the user's system is protected with a firewall that can terminate VPN tunnels ( caveat emptor one more timenot all broadband firewalls have VPN-termination capability). However, assuming that multiple systems are using the broadband connection, a hub can be used to distribute the secured connection as needed among them. Next is a similar situation, except that a hardware VPN client is providing the protection as well as VPN termination. This is a subtle differencethe firewall offers security with VPN, while the hardware client offers VPN plus security. Which is more appropriate depends on the nature of the outbound traffic from the remote user(s) in question. Finally comes the case in which the protection comes in the form of a router with firewall software, which can also terminate VPNs. This device is often advertised as a broadband router: It connects to broadband, provides router functionality (including DHCP and NAT), and might or might not offer multiple switched interfaces. If the switched interfaces are not available, you can again use a hub to distribute traffic as needed. Broadband routers, too, oftenbut not alwayscome with VPN termination. |
EAN: 2147483647
Pages: 177