Basic Authentication
12.2 Basic Authentication
Basic authentication is the most prevalent HTTP authentication protocol. Almost every major client and server implements basic authentication. Basic authentication was originally described in the HTTP/1.0 specification, but it has since been relocated into RFC 2617, which details HTTP authentication.
In basic authentication, a web server can refuse a transaction, challenging the client for a valid username and password. The server initiates the authentication challenge by returning a 401 status code instead of 200 and specifies the security realm being accessed with the WWW-Authenticate response header. When the browser receives the challenge, it opens a dialog box requesting the username and password for this realm. The username and password are sent back to the server in a slightly scrambled format inside an Authorization request header.
12.2.1 Basic Authentication Example
Figure 12-2 , earlier in this chapter, showed a detailed example of basic authentication:
In Figure 12-2 a, a user requests the personal family photo /family/jeff.jpg .
In Figure 12-2 b, the server sends back a 401 Authorization Required password challenge for the personal family photo, along with the WWW-Authenticate header. The header requests basic authentication for the realm named Family .
In Figure 12-2 c, the browser receives the 401 challenge and pops open a dialog box asking for the username and password for the Family realm. When the user enters the username and password, the browser joins them with a colon , encodes them into a "scrambled" base-64 representation (discussed in the next section), and sends them back in the Authorization header.
In Figure 12-2 d, the server decodes the username and password, verifies that they are correct, and returns the requested document in an HTTP 200 OK message.
The HTTP basic authentication WWW-Authenticate and Authorization headers are summarized in Table 12-2 .
Table 12-2. Basic authentication headers | |
| Challenge/Response | Header syntax and description |
| Challenge (server to client) | There may be different passwords for different parts of the site. The realm is a quoted string that names the set of documents being requested, so the user knows which password to use. WWW-Authenticate: Basic realm= quoted-realm |
| Response (client to server) | The username and password are joined together by a colon (:) and then converted to base-64 encoding, making it a bit easier to include international characters in usernames and passwords and making it less likely that a cursory examination will yield usernames and passwords while watching network traffic. Authorization: Basic base64-username-and-password |
Note that the basic authentication protocol does not make use of the Authentication-Info header we showed in Table 12-1 .
12.2.2 Base-64 Username/Password Encoding
HTTP basic authentication packs the username and password together (separated by a colon), and encodes them using the base-64 encoding method. If you don't know what base-64 encoding is, don't worry. You don't need to know much about it, and if you are curious , you can read all about it in Appendix E . In a nutshell , base-64 encoding takes a sequence of 8-bit bytes and breaks the sequence of bits into 6-bit chunks . Each 6-bit piece is used to pick a character in a special 64-character alphabet, consisting mostly of letters and numbers .
Figure 12-4 shows an example of using base-64 encoding for basic authentication. Here, the username is "brian-totty" and the password is "Ow!". The browser joins the username and password with a colon, yielding the packed string "brian-totty:Ow!". This string is then base 64-encoded into this mouthful: "YnJpYW4tdG90dHk6T3ch".
Figure 12-4. Generating a basic Authorization header from username and password
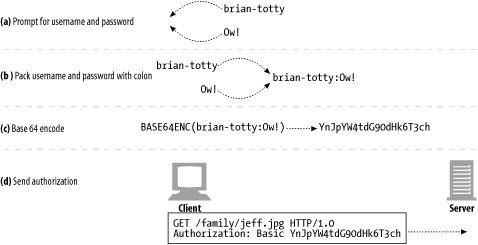
Base-64 encoding was invented to take strings of binary, text, and international character data (which caused problems on some systems) and convert them temporarily into a portable alphabet for transmission. The original strings could then be decoded on the remote end without fear of transmission corruption.
Base-64 encoding can be useful for usernames and passwords that contain international characters or other characters that are illegal in HTTP headers (such as quotation marks, colons, and carriage returns). Also, because base-64 encoding trivially scrambles the username and password, it can help prevent administrators from accidentally viewing usernames and passwords while administering servers and networks.
12.2.3 Proxy Authentication
Authentication also can be done by intermediary proxy servers. Some organizations use proxy servers to authenticate users before letting them access servers, LANs, or wireless networks. Proxy servers can be a convenient way to provide unified access control across an organization's resources, because access policies can be centrally administered on the proxy server. The first step in this process is to establish the identity via proxy authentication .
The steps involved in proxy authentication are identical to that of web server identification. However, the headers and status codes are different. Table 12-3 contrasts the status codes and headers used in web server and proxy authentication.
Table 12-3. Web server versus proxy authentication | |
| Web server | Proxy server |
| Unauthorized status code: 401 | Unauthorized status code: 407 |
| WWW-Authenticate | Proxy-Authenticate |
| Authorization | Proxy-Authorization |
| Authentication-Info | Proxy-Authentication-Info |
EAN: 2147483647
Pages: 294