Chapter 3: Java Security Components
IntroductionThe purpose of this chapter is to introduce some of the many Java components for security. The difference between the Java components lies in the purpose of the component, the supporting algorithm, and the supporting protocol. In Chapter 1, the operations for security are defined as authentication, authorization, data confidentiality, and data integrity. All Java security components do have similarities based on how they are constructed . To access the security interface to use in Java applications, the Sun JDK 1.4 provides the Application Programming Interface (API). Java APIs are provided for the security operations defined in Chapter 1. The security operation, in turn , calls a Service Provider Interface (SPI) to allow other security mechanisms to be plugged in. By using an API and SPI methodology, security mechanisms can be updated or modified without modifying code. The SPI interface allows different security mechanisms to be plugged by adding entries to configuration files and adding Java engines for more algorithms. The SPI interface allows the Java security components to grow in supporting algorithms and security mechanisms. Figure 3-1 shows the association of the API and SPI. Implementations are discussed in more detail in subsequent chapters. 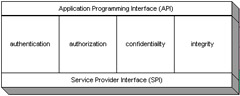 Figure 3-1: The association of the API and SPI
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |