Chapter 25: PKI Management
IntroductionThe previous chapter defined the format of the X.509 digital certificate. The format is a guide to understanding the benefits and limitations of the Public Key Infrastructure (PKI). PKI provides the ability to create, store, distribute, manage, and revoke public keys with the use of the X.509 digital certificate format. Very few certificates are actually created by a user , except for testing purposes, because for subjects and issuers that are not inside the same organization, a path of trust must be established to certify that the message was encrypted by the sender's private key. As a user, you cannot trust everyone who handles a certificate as it is being sent across the Internet, so PKI allows the receiver and sender of the secure message to only be concerned with trust points, commonly known as Trust Anchors (TA). The sender and receiver of the message are commonly known as the end entities. The TA is the point that an end entity will trust. A TA is normally a Certificate Authority (CA). The CA is a third-party company that is responsible for establishing a TA and a certificate path. The certificate path is the path that a certificate will take to transfer from one end entity to the other. Figure 25-1 gives an example. 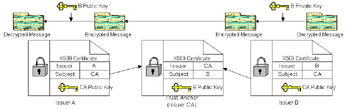 Figure 25-1: Basic certificate path Here is a description of Figure 25-1:
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |