Authenticating with JAAS
Up till now in this chapter, passing credentials through the Kerberos authentication mechanism have been coded directly in the GSSNames . The Kerberos login module has been set up from Chapter 16. In order to use the Kerberos login module, you need the Kerberos realm, the Kerberos Key Distribution Center that is part of the server, and the configuration file for the Kerberos login module. The basic configuration file defines the Kerberos login module to be used for authentication and gives parameters on how to load the Kerberos module. The com.sun.security.jgss.initiate entry is the parameters for the Java GSS initiator's authentication mechanism and the com.sun.security.jgss.accept entry is for the acceptor's authentication mechanism. The accept entry specifies the storeKey=true that indicates that the Kerberos secret key will be generated from the Kerberos password and stored in the Kerberos private credential set. The basic configuration file is needed by the underlying GSS-API for startup information for the Java GSS's matching authentication mechanisms and is given in Listing 17-3. Listing 17-3: Basic configuration file
/** * Login Configuration for JAAS. */ com.sun.security.jgss.initiate { com.sun.security.auth.module.Krb5LoginModule required; }; com.sun.security.jgss.accept { com.sun.security.auth.module.Krb5LoginModule required storeKey=true; };
The same type of configuration parameters can be applied directly to the initiator and acceptor. If the RichGSSService.java file was broken out into two files, one for the initiator RichGSSInitiate.java and the acceptor kept as the RichGSSService.java , the configuration file could be updated just for the client and the server in a csLogin.conf in Listing 17-4. Listing 17-4: Client/server configuration file
/** * Login Configuration for JAAS. */ RichGSSInitiate{ com.sun.security.auth.module.Krb5LoginModule required; }; RichGSSService{ com.sun.security.auth.module.Krb5LoginModule required storeKey=true principal="rich@richware.com"; };
In Listing 17-4 the service principal is defined in the client/server configuration file as "rich@richware.com" to define access to the server for any service interaction. The rest of this section describes changing the implementation to set up JAAS. Once JAAS becomes enforced, the security manager and access controller are now defined. When the security manager is defined, permissions to sockets and services must become explicit in security policies. The best way to differentiate between the client and the server is to codebase them. By codebasing the client and server, each class is put into a separate jar file, and the jar file references each grant entry. The RichGSSIntitiate.jar , which contains the RichGSSInitiate.class , references the entry for the initiator and the RichGSSService.jar , which contains the RichGSSService.jar file, references the entry acceptor.
The initiator's policy file will now need to grant socket connect permissions and service permissions to access the socket protocol and Kerberos realm. See Listing 17-5. Listing 17-5: RichGSSInitiator's policy file
grant CodeBase "file:./Login.jar" { permission java.security.AllPermission; }; grant CodeBase "file:./RichGSSInitiator.jar", Principal javax.security.auth.kerberos.KerberosPrincipal "rhelton@richware.com" { permission java.net.SocketPermission "*", "connect"; permission javax.security.auth.kerberos.ServicePermission "krbtgt/richware.com@richware.com", "initiate"; permission javax.security.auth.kerberos.ServicePermission "rich@richware.com", "initiate"; };
Listing 17-5 defines the initiator jar to give access to Kerberos user principal rhelton@richware.com to allow a socket connection and initiate the GSS for the Kerberos mechanism at richware.com with the Kerberos service principal of rich@richware.com . The grant entry gives access to initiate and connect through a socket to the Kerberos acceptor at richware.com . The Login.jar contains the Login.class file that contains the callback handlers and login functionality for the JAAS login. The reason that access must now be given by the grant entry by Kerberos and the sockets is because a security manager is defined when JAAS is set up. If a security manager was defined in the JVM during runtime and JAAS was not being set up, these permissions would still need to be defined to explicitly access resources.
The acceptor's policy file will now need to grant socket accept permissions and service permissions to access the socket protocol and Kerberos realm. See Listing 17-6. Listing 17-6: RichGSSService's policy file
grant CodeBase "file:./Login.jar" { permission java.security.AllPermission; }; grant CodeBase "file:./RichGSSService.jar" Principal javax.security.auth.kerberos.KerberosPrincipal "rich@richware.com" { permission java.net.SocketPermission "*", "accept"; permission javax.security.auth.kerberos.ServicePermission "rich@richware.com", "accept"; };
Listing 17-6 gives the functionality to the RichGSSService.jar to accept incoming socket calls and act as a Kerberos acceptor for Kerberos initiators. The last step for changing the RichGSSService.java code to support JAAS is to provide the Login.java . An example of a Login.java is given in Chapter 19. Since the initiator previously had hard coded principals, the Login code simply passes the JAAS principals and credentials, given as a JAAS Subject object, to the RichGSSInitiator.class to define the Kerberos username and password to authenticate through the GSS-API. The modules now appear as shown in Figure 17-2. 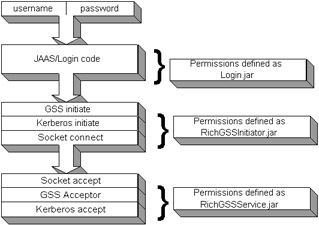 Figure 17-2: The JAAS implementation
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |