Introduction
Introduction
TCP/IP stands for Transmission Control Protocol/Internet Protocol and refers to a collection of data transmission protocols used for sending messages among a distributed network of computers.
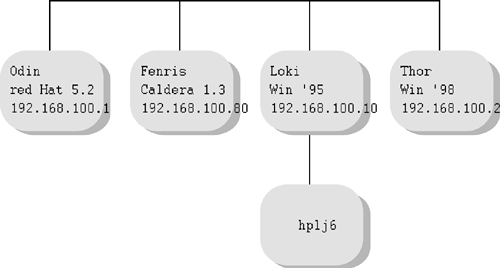
The examples in this section will be based on the following network (see Figure 31-1):
Figure 31-1. Sample Network
Open System Interconnect (OSI) Reference Model
Most discussions of TCP/IP open with a few words about the OSI reference model. The OSI model was created in 1978 to specify a standard used for the development of network systems. Real world protocol designers have been cheerfully ignoring it ever since, but it comes up whenever people start to talk about TCP/IP. Rather than break tradition, I hereby include the 7-layer OSI reference model:
| Application | The application that you are invoking at the command line to perform various tasks (e.g., telnet). |
| Presentation | This layer concerns itself with the format in which data will be handed to the adjoining layers. For example, EBCDIC to ASCII translation or encryption might be handled here. |
| Session | As the name implies, this layer is concerned with setup and shutdown of a communication session between two machines. |
| Transport | Concerned with reliable delivery and data integrity. |
| Network | This layer concerns itself with the routing of packets from one point in the network to another. |
| Data Link | In this layer, the bits received from the adjoining layers are grouped into logical units called frames. |
| Physical | This layer includes cabling and whatnot, and it is responsible for the actual transmission of data over an actual physical link. |
TCP/IP Protocol
Like most network protocols, TCP/IP bears only a peripheral resemblance to the OSI model. The TCP/IP designers had their own layers in mind:
| Application | Implementation of a protocol for a specific task (e.g., simple mail transport protocol (SMTP) for mail, telnet for remote logins). |
| Transport | The procedure two machines use to communicate with one another. For example, the TCP protocol that exists at this layer is a reliable, connection-oriented protocol (see following definitions). |
| Internet | This layer is concerned with shuffling information (arranged into packets called datagrams) between two hosts. The hosts need not know anything about how the network is organized or how the data will get there. |
| Host-to-Network | Concerned with the physical connection to a network and the transmission of data across subnetworks. |
IP Addresses
An IP address is a sequence of 4 bytes used to uniquely identify a host on a network. The bytes are usually presented in dotted octet form. For example;
127.0.0.1
is the loopback address, which is included in the /etc/hosts file to enable a machine to refer to itself.
Recall that a byte is a set of eight binary digits (zeros or ones) called bits. Because each byte contains eight bits, the maximum value a single byte can take is 255 (see Figure 31-2).
Figure 31-2. Byte Values

Address Classes
IP addresses are divided into classes. Depending on the class, either the first byte, the first two bytes, or first three bytes of the IP address refer to the Network address of the node. The remaining bytes refer to the host address. The way to tell what class an IP address is in is to look at the value of the first byte:
| 1st Byte | Address Class | Bit Division | Example |
| < 128 | A | net.host.host.host | 32.103.26.2 |
| 128-191 | B | net.net.host.host | 129.32.101.7 |
| 192-223 | C | net.net.net.host | 196.78.33.101 |
Subnet Masks
A subnet mask is another dotted octet sequence used to specify which bits in the IP address will refer to the network address and which will refer to the host address. In the simplest case, the bits used in the subnet mask are determined by the address class:
| Address Class | Default Subnet Mask |
| A | 255.0.0.0 |
| B | 255.255.0.0 |
| C | 255.255.255.0 |
Note that the subnet mask is only the default masking; it doesn't have to be done at the byte boundaries. However, a full description of subnetting is beyond the scope of this book. If you're connecting to a network that uses some strange subnet mask, talk to your network administrator. Otherwise, just accept the default for now.
Jargon
Any nontrivial endeavor will generate buzzwords, and networking is no exception. Here is a sampling of the jargon you're likely to run across in this chapter:
| Reliable | When used in the network context, this word refers to a protocol that guarantees delivery of all packets transmitted. |
| Unreliable | Protocols described as unreliable are not necessarily unreliable in the common English sense of the word; they just don't guarantee delivery of any particular packet. |
| Connection Oriented | A protocol is connection oriented if it establishes a connection between the two communicating hosts. A connectionless protocol transmits data without any direct communication ("handshaking") between the two hosts. |
| Name Resolution | Name resolution refers to the process of turning a dotted octed IP address into an English word (e.g., 192.168.100.1 = odin). |
|
| Name resolution adds a layer of complexity to the networking process. If a command doesn't work with a hostname (e.g., ping fenris), you ought to try pinging the actual IP address (e.g., ping 192 ). If the latter works but the former doesn't, you have a name resolution problem. Cheer up, things could be worse. |
|
| Most network problems are physical. For example, I spent almost an hour last Saturday trying to figure out why the little woman and I couldn't get X-Wing vs. TIE fighter to work before realizing that puppy dog had chewed up the cable. Similar things happen in industry, particularly when your wiring runs through the sales department. |
The following commands are covered in this chapter:
| arp | Maintain the address resolution protocol table |
| bootpd | Network boot daemon |
| bootptab | Dump bootp table |
| bootpgw | bootp gateway |
| bootptest | Test bootp |
| dip | Handle dialup IP links |
| hostname | Set or display host name |
| gated | Implementation of the gated routing protocol |
| gdc | Gated controller |
| ifconfig | Configure network interface |
| in.identd | User identification protocol |
| netstat | Network status information |
| nslookup | Query Internet domain server |
| rmail | Handle mail received via uucp |
| route | Display or manipulate IP routing |
| routed | Network routing daemon |
| rusers | Similar to who, but works across the network |
| tcpdchk | Check TCP wrapper |
| tcpdmatch | Predict response to TCP request |
| traceroute | Trace route of IP packet from specified host |
EAN: 2147483647
Pages: 174